Recently, it has been circulating on the internet that a privilege escalation tool used by cybersecurity professionals has been backdoored, resulting in the leakage of the tool users’ identities and data. After analysis by ThreatBook Research and Response Team, this incident was identified as a targeted attack by the Southeast Asian APT group OceanLotus(APT32), who used GitHub to release a Cobalt Strike exploit plugin with a Trojan, aimed at cybersecurity personnel. ThreatBook had already grasped this attack event in November 2024 and located the attacker’s GitHub account.
In this attack, the attackers used a novel and concealed method for the first time by embedding a malicious .suo file into a Visual Studio project. When the victim compiles the Visual Studio project, the Trojan will execute automatically.
OceanLotus has recently launched targeted attacks against different industries and groups in China, as well as specific large technology enterprises. The first attack occurred between mid-September and early October 2024, and ThreatBook has captured multiple suspicious assets and Trojan files.
ThreatBook, through the analysis of related samples, IPs, and domain names, has extracted multiple related IOCs for threat intelligence detection. ThreatBook’s Threat Detection Platform (TDP), Threat Intelligence Platform (TIP), Threat Intelligence Cloud API, Cloud Sandbox S, Sandbox Analytics Platform (OneSandbox), DNS-based Secure Web Gateway (OneDNS), Threat Defense System (OneSIG), and Secure Endpoint Cloud (OneSEC) all support detection and protection for this attack event.
Incident Summary
| Attack Targets | Chinese cybersecurity researchers |
| Attack Time | Mid-October 2024 |
| Attack Vectors | GitHub poisoning |
| Attack Complexity | Complexity |
| Objective | Remote control, intelligence theft |
Incident Details
The main tactic of this OceanLotus attack was to release open-source security tool projects on GitHub, attracting Chinese cybersecurity researchers to download and further disseminate them. The poisoned account link is: https://github.com/0xjiefeng
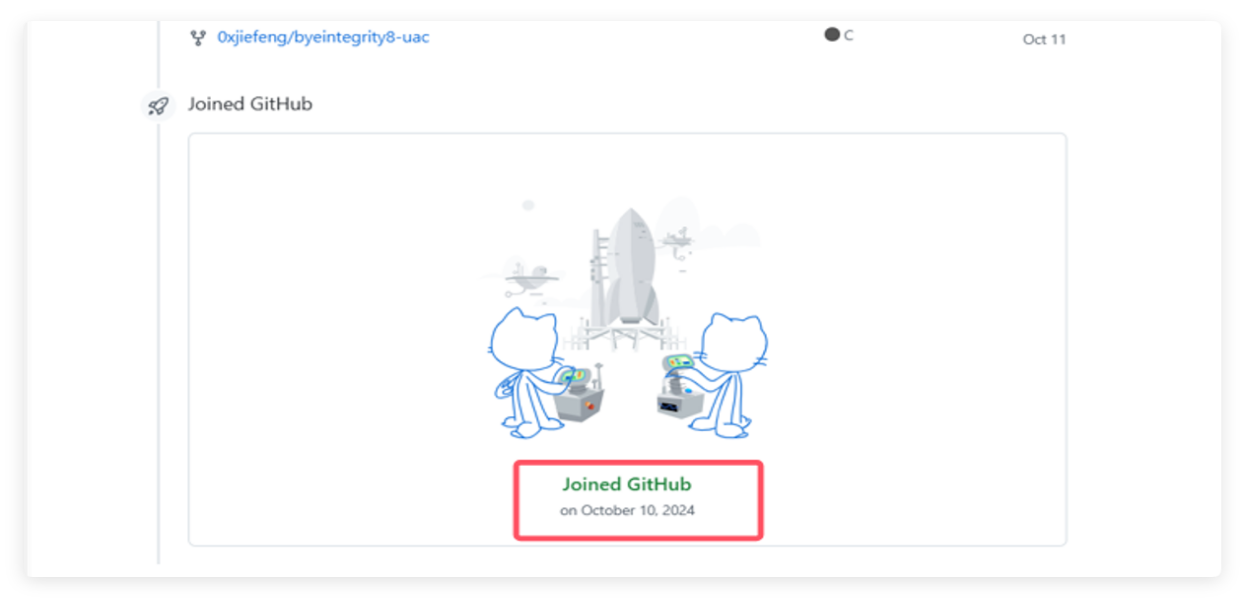
On October 10, 2024, the attacker registered this account and disguised themselves as a security researcher from a leading Chinese FinTech company, forking various security tool projects on their homepage to reduce the victims’ vigilance.
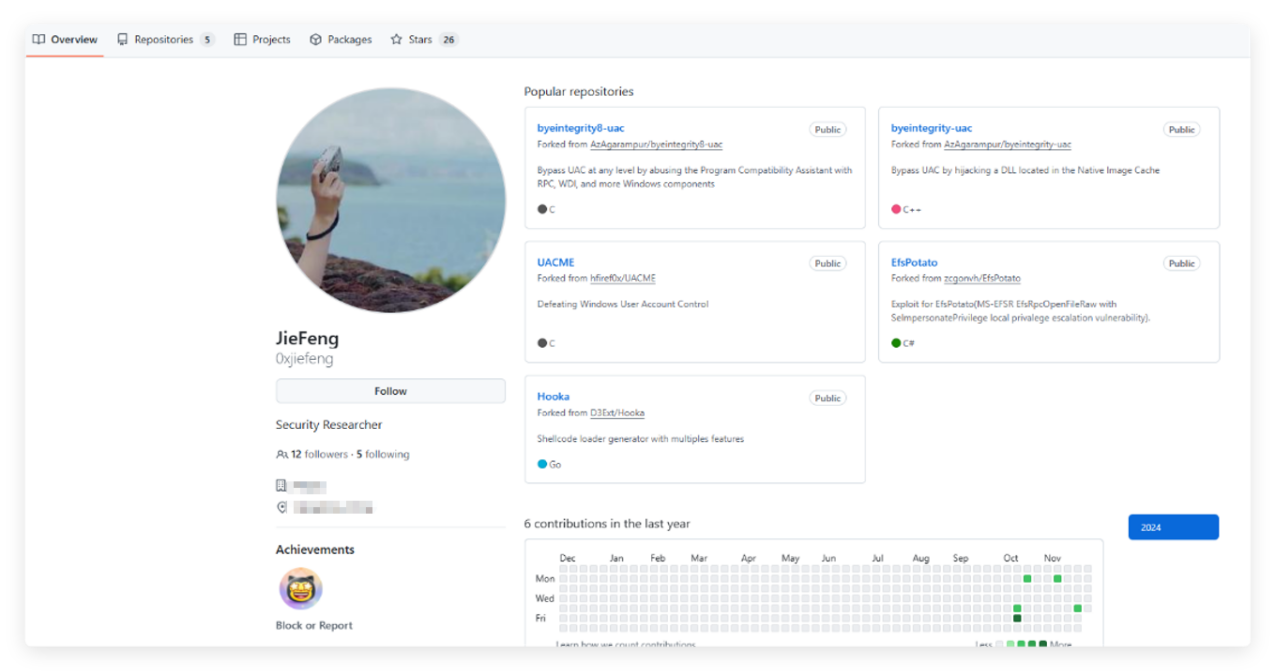
On October 14 and October 21, 2024, the attacker published two malicious poisoning projects, containing plugins for the commonly used Chinese red team tool Cobalt Strike, with new exploit functions. The attacker used Chinese descriptions in the project introduction to attract more targets in the Chinese cybersecurity industry.
Currently, the attacker’s account has deleted the published projects, but the poisoned project code has been merged into other Chinese cybersecurity researchers’ repositories and is still accessible.
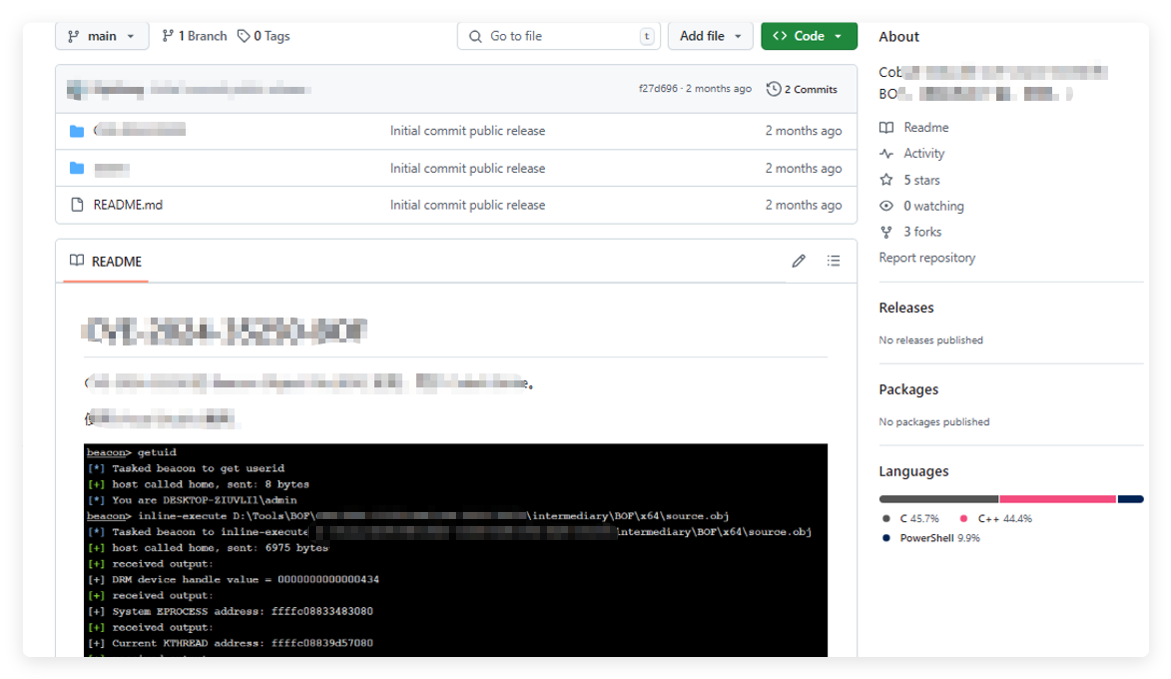
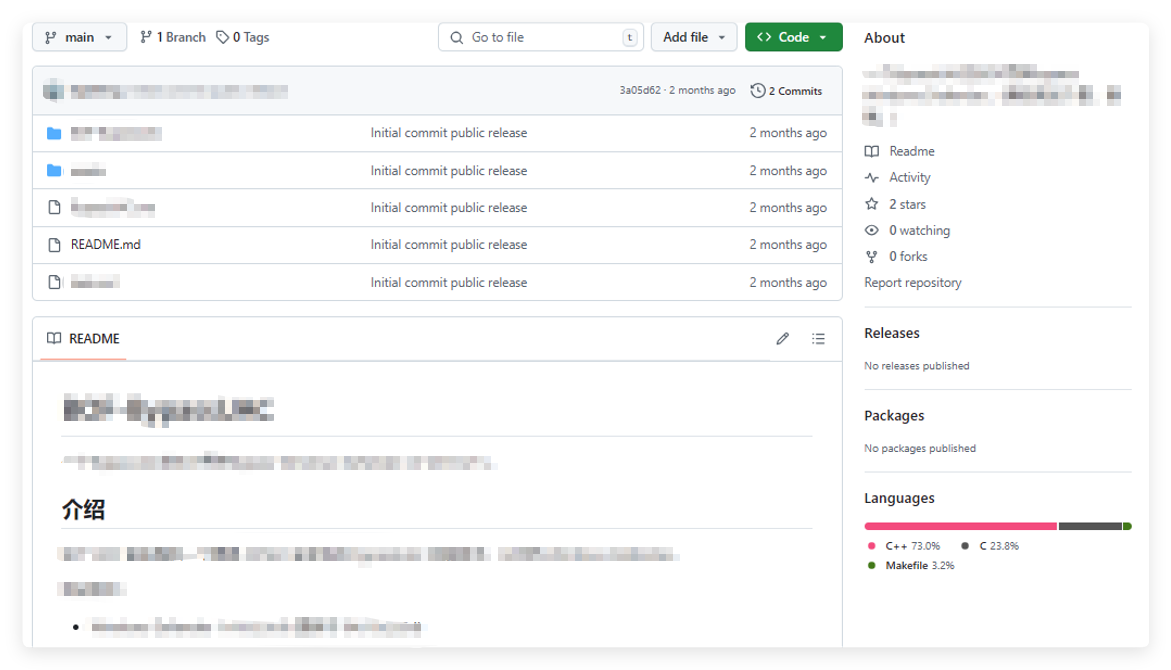
The Chinese expressions in the project introduction have obvious signs of machine translation, mainly guiding target users to use Visual Studio to open the project’s .sln file to trigger the subsequent execution of malicious code.
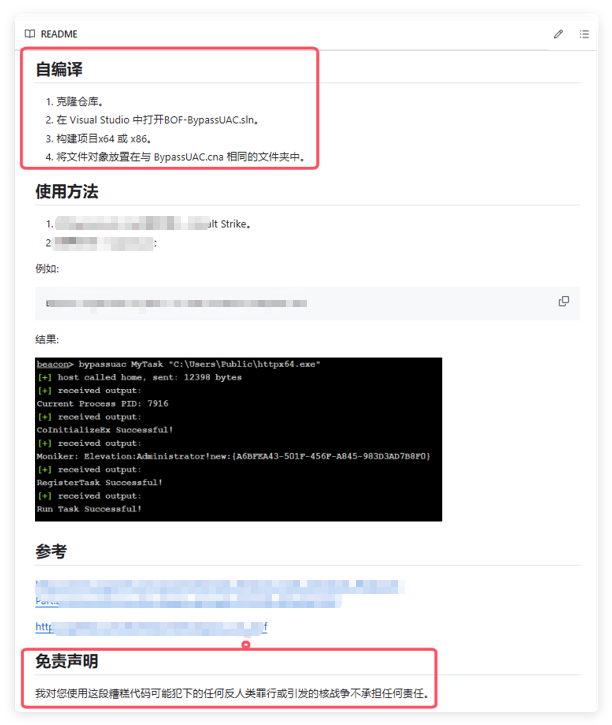
When victims use Visual Studio to open .sln or .csproj project files, Visual Studio will automatically load and call the associated .suo file, thereby triggering the execution of the malicious code. In this incident, OceanLotus used the technique of calling the .suo file for the first time. The malicious code is executed once and then overwritten and deleted, making it extremely concealed.
For related technical proof of concept, you can refer to the article:
https://github.com/cjm00n/EvilSln
According to subsequent analysis, this poisoning attack event has spread widely in the domestic cybersecurity industry, with many Chinese cybersecurity blogs sharing the poisoned project, resulting in a large number of views and forwards.
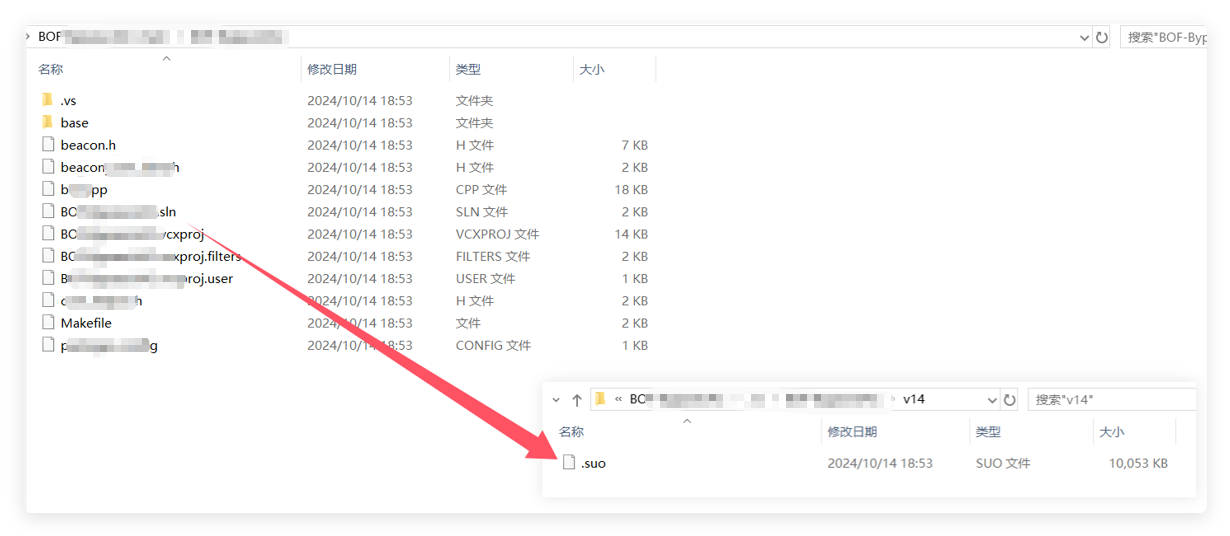
Correlation Analysis
When the target victim uses Visual Studio to open the project’s solution file (.sln) for compilation, Visual Studio will automatically load and call the related .suo (Solution User Options) file, thereby triggering the execution of the malicious code. Moreover, since Visual Studio saves new content to the .suo file when closing, the malicious code will be cleared, making the entire attack action more difficult to detect.
By loading the VsToolboxService stream in VSPackage, the malicious code is executed by deserializing with BinaryFormatter, which is encoded in base64.
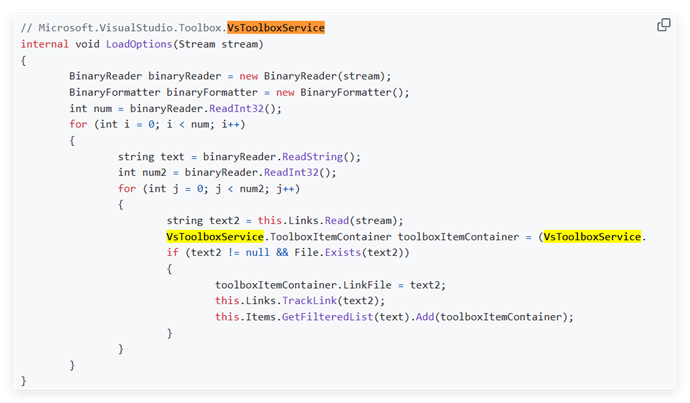
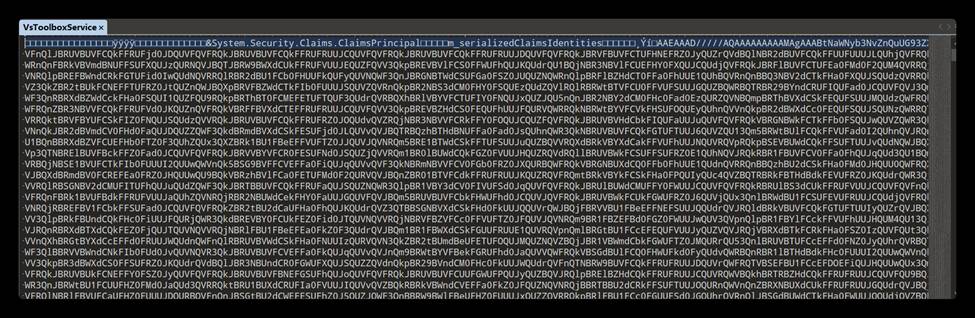
After sample analysis, it was found that after executing the project, the malicious white-on-black components are released to the directory:
C:\Users\Public\TTDIndexerX64\TraceIndexer.exe
C:\Users\Public\TTDIndexerX64\TTDReplay.dll
And it is written into the autostart registry:
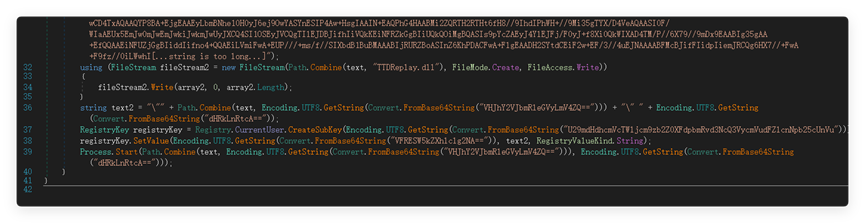
In terms of shellcode execution, the dll hollowing technique commonly used by the OceanLotus organization is used. By loading the system xpsservices.dll and hollowing it out, the shellcode is overwritten into the memory space of the dll to execute malicious functions. The program ultimately uses the API of the foreign note-taking platform Notion to achieve C2 communication, evading traffic detection and interception, and embedding commands into the Notion workspace to realize the initial sending and receiving of instructions.
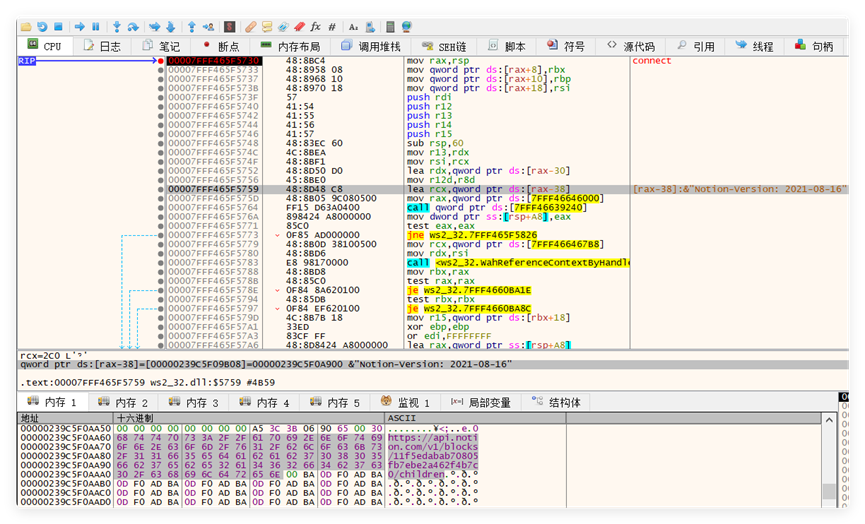
At the sample level, according to the sample’s code structure, loading method, metadata, strings, and other features, more similar files can be associated. Among the associated samples, the parent file of “tbs.dll” is the sample disclosed by the security enterprise that OceanLotus used a spear-phishing email to attack Chinese government and enterprise industries.
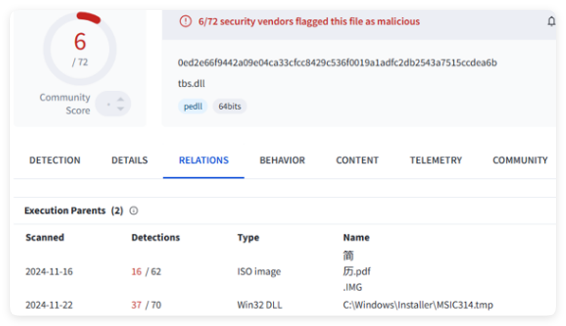
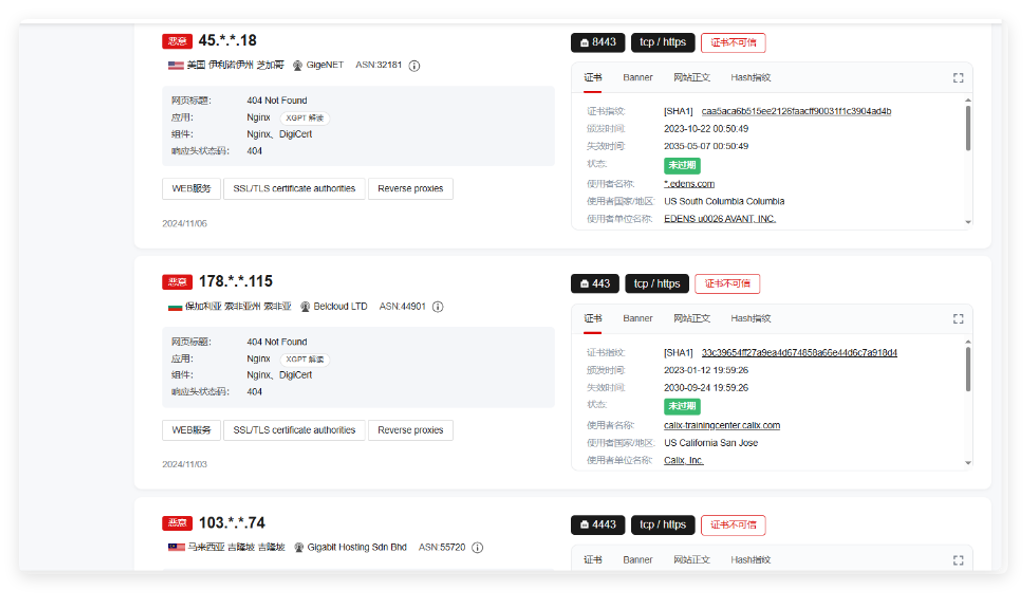
ThreatBook’s mapping data association found that the organization’s assets in this attack activity are not limited to a single C2 asset. The attack assets have significant port mapping characteristics. The time range when OceanLotus began to actively attack this time is roughly from mid-September to early October. According to the mapping data and the compilation time of the samples in this batch of attacks by OceanLotus, the asset deployment time basically matches. Through the related feature search, other active suspicious C2 addresses were also found.
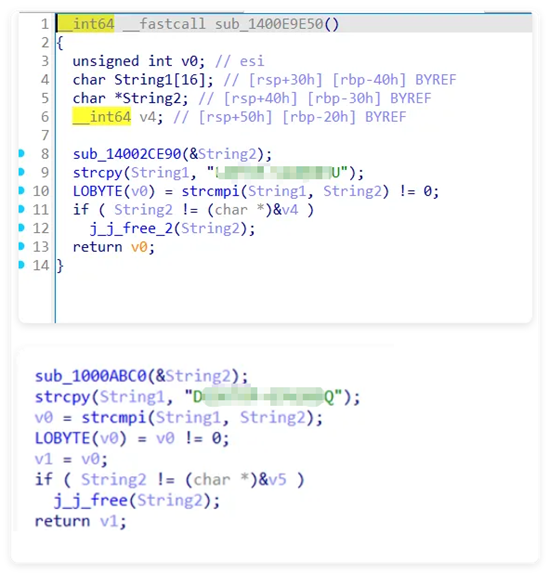
When analyzing the same batch of attack samples, it was found that OceanLotus’s attack purpose was strong this time. Some samples will check whether the victim’s computer name and target are consistent during the execution process to target specific large technology enterprise users.
IOC
Page_id back to Notion:
11f5edabab708090b982d1fe423f2c0b
Related OceanLotus attack C2s:
190.211.254.203:4443
45.41.204.18:8443
45.41.204.15:443
178.255.220.115:443
103.91.67.74:4443
154.93.37.106:443
193.138.195.192:8443
38.54.59.112:80

