Overview
Patchwork is a suspected hacker organization with a possible affiliation to a government in South Asia. Its earliest documented attack activities date back to 2009. The group primarily targets sensitive entities such as military-industrial complexes, diplomatic institutions, and research universities in countries including China, Pakistan, and Bangladesh.
ThreatBook has captured multiple attack activities attributed to the Patchwork by the Threat Hunting system. Through analysis, the following findings have been made:
- The attackers launched cyber attacks againstgovernment and universities in China through phishing emails. They executed malicious code by including malicious attachments in the emails, which were disguised as .pdf files but were actually .lnk shortcuts. These shortcuts used PowerShell to download lure and Trojan files from a C2 server.
- In terms of attack techniques, the delivery phase remains consistent with previous methods, primarily relying on phishing emails containing malicious attachments or links. The subject lines of these emails during the delivery phase often revolve around time-sensitive topics such as “Notification,” “Meeting,” “Minutes,” and other similar subjects.
- Patchwork not only employs the commonly used BADNEWS Trojan for remote control of their targets but also launches attacks using the commercial Trojan “Remcos” and the open-source penetration testing framework “Havoc.”
- By conducting source analysis on relevant samples, IP addresses, and domain names, ThreatBook has extracted multiple related IOCs (Indicators of Compromise) that can be used for threat intelligence detection. Threatbook CTI and API can be used to get relevant intelligence.
Details
Patchwork is a suspected hacker organization with a possible affiliation to a government in South Asia. Its earliest documented attack activities can be traced back to 2009. The group primarily targets sensitive entities such as military-industrial complexes, diplomatic institutions, and research universities in countries including China, Pakistan, and Bangladesh.
Recently, ThreatBook has discovered a series of attack activities attributed to this organization. In their attacks targeting China, the attackers utilize the topic of “Critical Notification” as lure to send phishing emails to target users. These phishing emails contain malicious attachments designed to trick users into executing the malicious files enclosed in the attachments.
Detail Analysis
The attackers exploit topics such as “National Key R&D Program” and “Advanced Structures and Composite Materials” to send phishing emails to target users. These phishing emails contain malicious attachments that share the same name as the email subject.


The attachments sent by the attackers in their emails are .lnk files disguised as PDF files. In reality, these .lnk files execute malicious code through PowerShell. The code’s purpose is to download and open lure files from the C2 address “msit5214.b-cdn.net.” The Trojan files, on the other hand, are downloaded from “msit5214.b-cdn.net/c” and a scheduled task named “OneDriveUpdate” is created to execute them.

The Trojan used in this attack is Badnews Trojan which is commonly used by Patchwork. In this particular attack campaign, the attackers have made some modifications to the Trojan. Previous versions of the Badnews Trojan used numerical values such as “0,” “4,” “8,” “13,” as remote control commands, and they would save the command execution results locally on the host. However, in this attack campaign, remote control commands are issued as “3fgjfhg4,” “3gjdfghj6,” “3gnfjhk7,” and only a small portion of the execution results are saved locally. The majority of the stolen content is directly sent back to the C2 address.
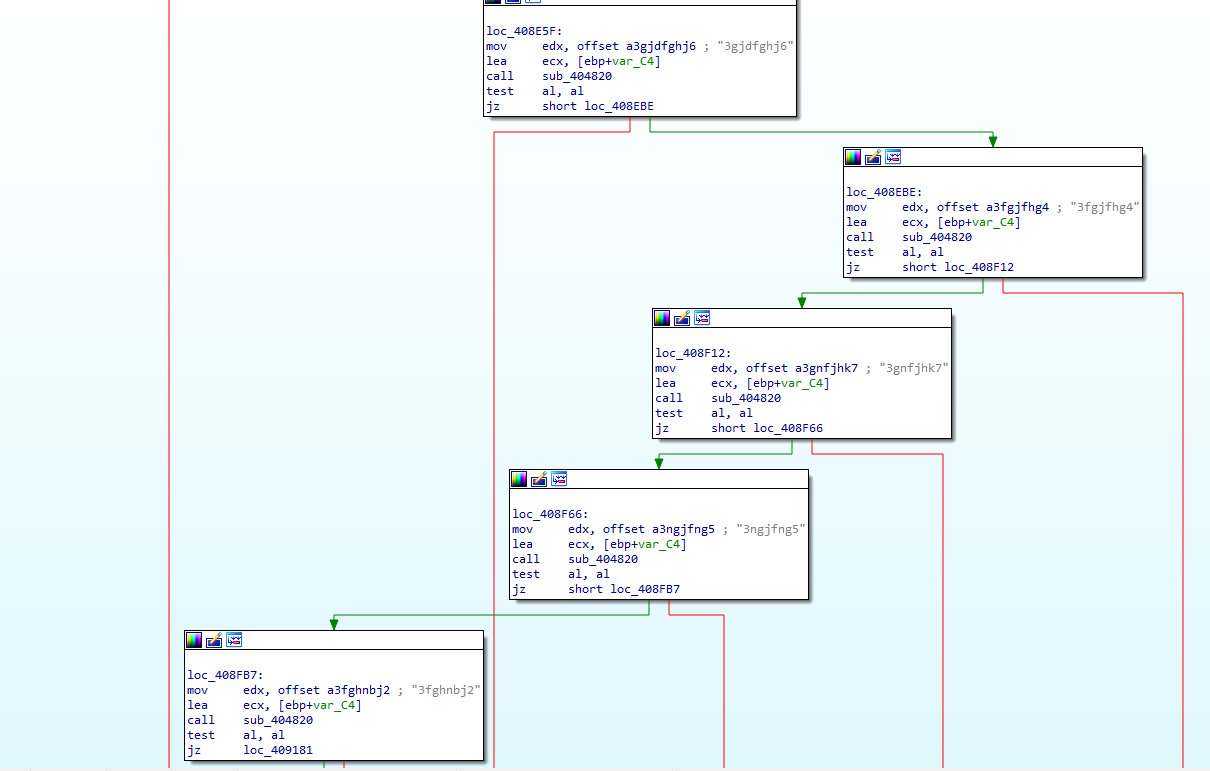
Association Analysis
In terms of domain characteristics, we have also discovered a batch of cases where this organization has launched attacks using the domain “b-cdn.net.” The attackers deliver attacks against targets using the open-source Trojan “Havoc.”
The attackers initiate the attack using the filename “Notification of Youth Civilization Open Week Activity.pdf.lnk” and employ the same attack technique to simultaneously download lure PDF files and subsequent payloads from the C2 address.

The attackers subsequently deliver a payload named “Havoc,” an open-source framework Trojan, and establish communication with the C2 address at 45.125.67.100:443.
In addition to the characteristics of the Badnews Trojan, we have also identified a batch of other samples associated with it. One example includes an attack launched with the file name “Key Points of Conversation with the Chinese Air Force.”
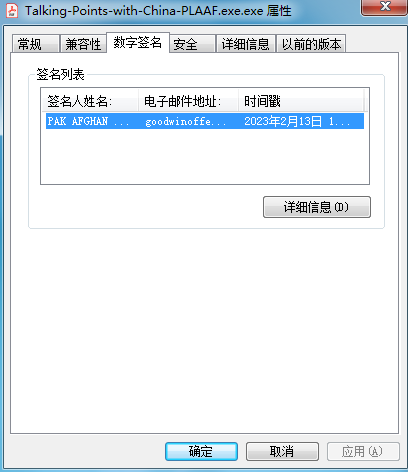
The attackers utilize a loader to decrypt and load the Remcos remote control Trojan in memory, establishing communication with the C2 address at 45.137.118.105:443.

In another sample, the attackers utilize a compromised site from Pakistan, webmail.mod.com.pk, to store the subsequent payload. Simultaneously, the attackers deliver a password-protected document named “FIA NOTICE” and a shortcut file named “password.” The shortcut file utilizes mshta.exe to execute the subsequent payload from the C2 address webmail.mod.com.pk.
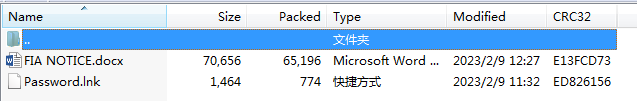
The subsequent payload remains the same as the Trojan named “Key Points of Conversation with the Chinese Air Force.” It is decrypted from memory using a loader, and the payload consists of the Remcos remote control Trojan, which is loaded and executed directly. The communication is established with the C2 address at 45.146.254.153.
In addition to content related to China and Pakistan, there are also samples that launch attacks with subjects such as “Minutes of Joint Operation Meeting with the Bangladesh Navy,” “NVIDIA GeForce Experience,” and “Turkish Delegation.” The subsequent payload in all these cases is the Remcos remote control Trojan.

Summarize
In recent captured attack activities, Patchwork continues to engage in high-frequency attacks, primarily targeting countries in South Asia. In terms of attack techniques, the delivery phase remains consistent with previous methods, primarily relying on phishing emails containing malicious attachments or links. The subject lines of these emails during the delivery phase often revolve around time-sensitive topics such as “Notification,” “Meeting,” “Minutes,” and other similar subjects. In the subsequent payload, in addition to the continued use of the BADNEWS Trojan, Patchwork has also started utilizing open-source Trojans like “Remcos” and “Havoc” for post-exploitation against their targets.
Patchwork has been conducting long-term network attacks against China, Pakistan, and countries in the surrounding South Asian region. Moving forward, we will continue to monitor the activities of this organization closely.
Appendix - IOC
IP
45.146.254.153
103.253.43.187
79.141.168.220
185.239.237.197
45.137.116.253
45.137.118.105
8.210.104.188
45.125.67.100
45.125.67.244
45.125.67.125
193.203.238.116
8.210.103.41
Domain
Hash
e30b7ba5144d6e56f89457d3c609996d52ffb3aa06e1b7b14ace6a0b1e90f86d
818bd67db5fe30f5cfdab861f996f30fa20427e3e1aa65ffe6d98f6c7af7558d
3d4ffcd1cd594f452ad1c374933eea8dd36d21a6d01372cc7f1afc636d26fa72
2de8ade5c7e304c9407d89f9a52b103b37dfac5b5431c2a9be2fe0c0382c75fe
47fb2a067f1992a87f966b51ba22bdbf32a8ad90f6efdc18a7878eaddca023c5
acdd91654cfb1424ebc5212eae69024fe33b9d992ffeca81cbd6161df80a51e2
1a22dd2f6968e76c8c044d423cd592eb1bed01d2be6fc6df901437b593384ec9
26cabb4a837e47b14b9a19fa4073173bdbf61a9e38c94c50a717636b30d34faf
4eb33942cc5eaad25f545fa4ea768b5a6002bb9dda72a991c42da7f8a9accdc1
04261cbcd4e801a43981bf9d60eb31468fb0f3ecd055ab457c5b4d317ae8915d
16aadf7a8fc02449d088670dd9b22aa9bff08c936822f84c02cb3b49f913a9cb
9dd10b29fb19973dd0b1584576adea91fe0f5af0475386b0bf33b2497b517e21
e30b7ba5144d6e56f89457d3c609996d52ffb3aa06e1b7b14ace6a0b1e90f86d
818bd67db5fe30f5cfdab861f996f30fa20427e3e1aa65ffe6d98f6c7af7558d
538b607c03aa2d0960c396529399921f957f421a3ca084d140316e2ee21889cc
5ea5c222eac8830c77f5a3e3ba2ffd437215501a7b42604d13321dbc71a34635
efcec66ab8fb14178873a48b391dfa35529088f9953d58f6a7b5cfa69ec9ecbf
04172c06edcc15dbed71db50fad935e6b82bfae78491237eee00f60ffbaf57f3
3a573796b5e6f1cc3a92eef7e268fa4e74aeddf34f5dd62f7b02109fe560ecd2
717dab9464c35bda378df8f42ceb245e1b34152fe7a5b1cefa632927c6275732
807e9c805426fa9813404ccdb44878b48b7e9644cfee2065a7a584bd43580f36
6f71f637c9572837b33d80036c0b7852db4223e104faedf57ff76306a324440c
f5766ece18b863c7747d739b4a0b944cdb13e9993dbc3401d4ea1923dbb0578a
46f812dc9ab1da606915a40d98ffd7afa7827c9c2198f26ced8a48b7d9eeb3de
3d4ffcd1cd594f452ad1c374933eea8dd36d21a6d01372cc7f1afc636d26fa72
2de8ade5c7e304c9407d89f9a52b103b37dfac5b5431c2a9be2fe0c0382c75fe
47fb2a067f1992a87f966b51ba22bdbf32a8ad90f6efdc18a7878eaddca023c5
acdd91654cfb1424ebc5212eae69024fe33b9d992ffeca81cbd6161df80a51e2
1a22dd2f6968e76c8c044d423cd592eb1bed01d2be6fc6df901437b593384ec9
26cabb4a837e47b14b9a19fa4073173bdbf61a9e38c94c50a717636b30d34faf
4eb33942cc5eaad25f545fa4ea768b5a6002bb9dda72a991c42da7f8a9accdc1
04261cbcd4e801a43981bf9d60eb31468fb0f3ecd055ab457c5b4d317ae8915d
16aadf7a8fc02449d088670dd9b22aa9bff08c936822f84c02cb3b49f913a9cb
9dd10b29fb19973dd0b1584576adea91fe0f5af0475386b0bf33b2497b517e21
e30b7ba5144d6e56f89457d3c609996d52ffb3aa06e1b7b14ace6a0b1e90f86d
818bd67db5fe30f5cfdab861f996f30fa20427e3e1aa65ffe6d98f6c7af7558d

