Summary
ThreatBook captured a batch of samples on the topic of OnlyFans video leakage recently. After analysis by ThreatBook, it was found that:
- Attackers use OnlyFans video leaks as the topic to deliver trojans to users. Using JWT as a configuration file to steal information from Chrome, suspected of stealing user Facebook tokens and showing interest in their information.
- We extracted C2 from the current samples and conducted extension analysis, identifying other assets behind the attacker. We suggest using internal security devices to block them directly. Please refer to the appendix for specific attacker assets.
Incident Review
OnlyFans is a social media platform that allows users to share paid photos, videos, and other content, typically related to adult content. The platform was established in 2016 with the aim of providing creators with a way to earn income while also providing users with a platform to interact with creators. On OnlyFans, users can subscribe to the content of creators they are interested in and pay for it. Creators can earn income through these subscriptions, while also having private chats and interactions with subscribers on the platform.
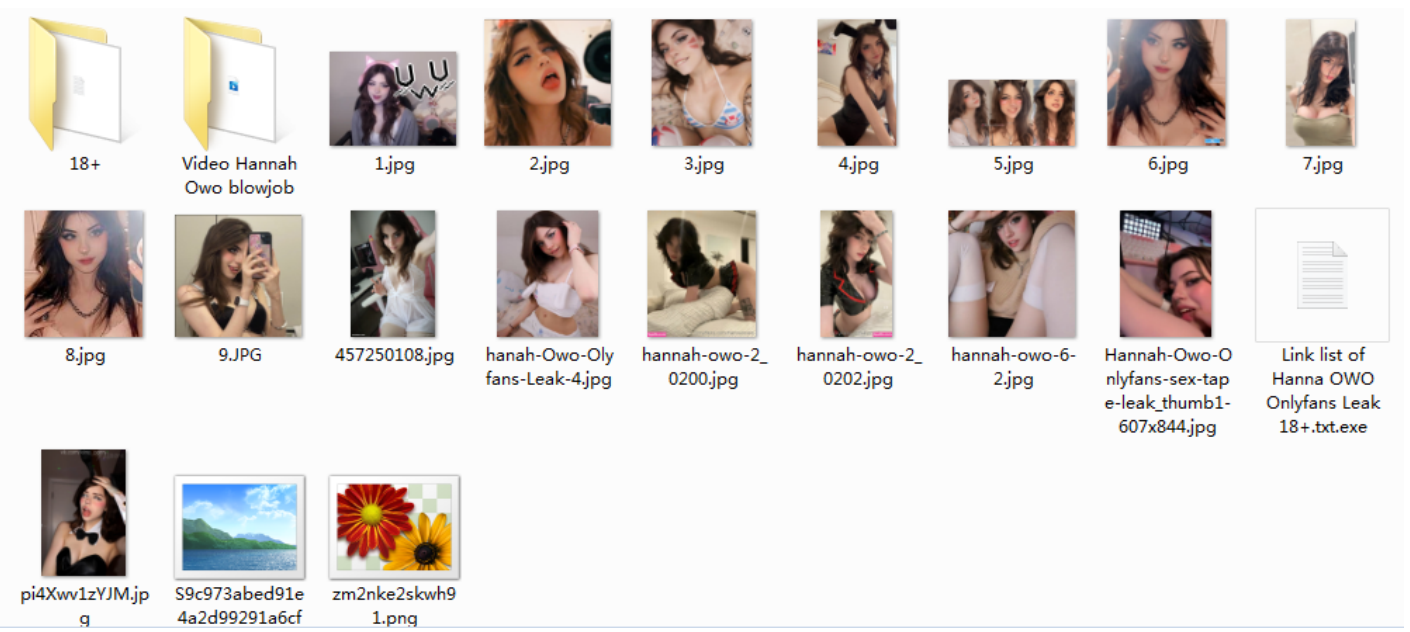
Recently, ThreatBook captured a batch of samples with the topic of OnlyFans platform video leakage. Attackers used paid content leakage as the lure, packaged images and Trojan programs together, and used pornographic images to lure users into executing Trojan files disguised as videos, suspected of stealing user Facebook tokens.
Sample analysis
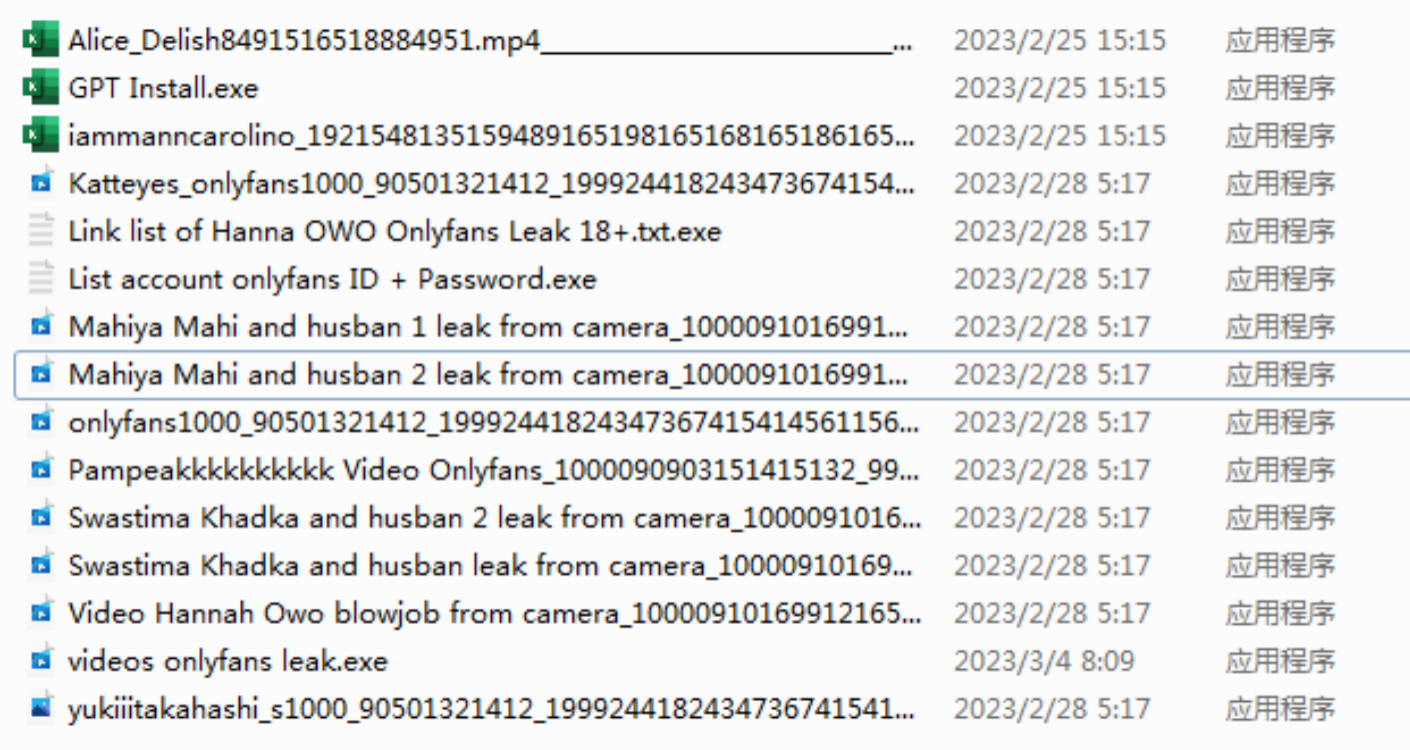
Attackers attach malicious files to the compressed package and use underscores, spaces, and long numbers to hide the suffix of the malicious file name, and disguise the icon as a video, notepad, and so on.
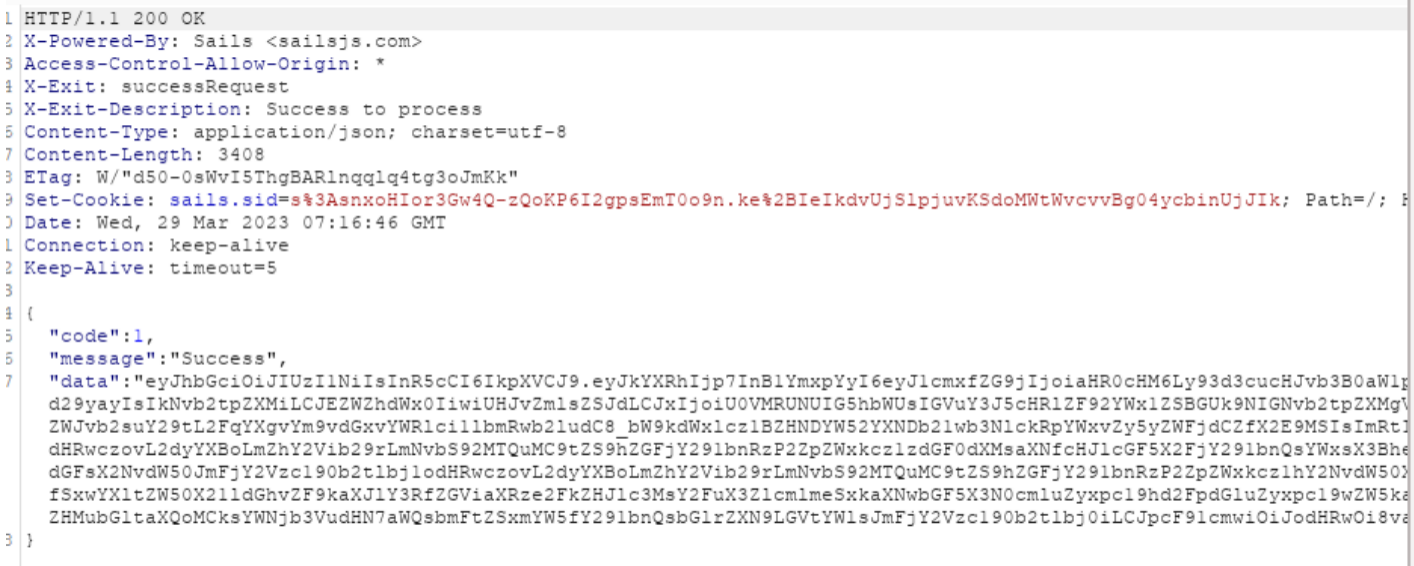
The sample is compiled by Golang and will first connect to the C2 address" http://167.179.66.121:1337/api/setting" to obtain the configuration file. The attacker utilizes the JWT token. From the decrypted configuration file, it appears that the attacker is interested in Facebook’s token.
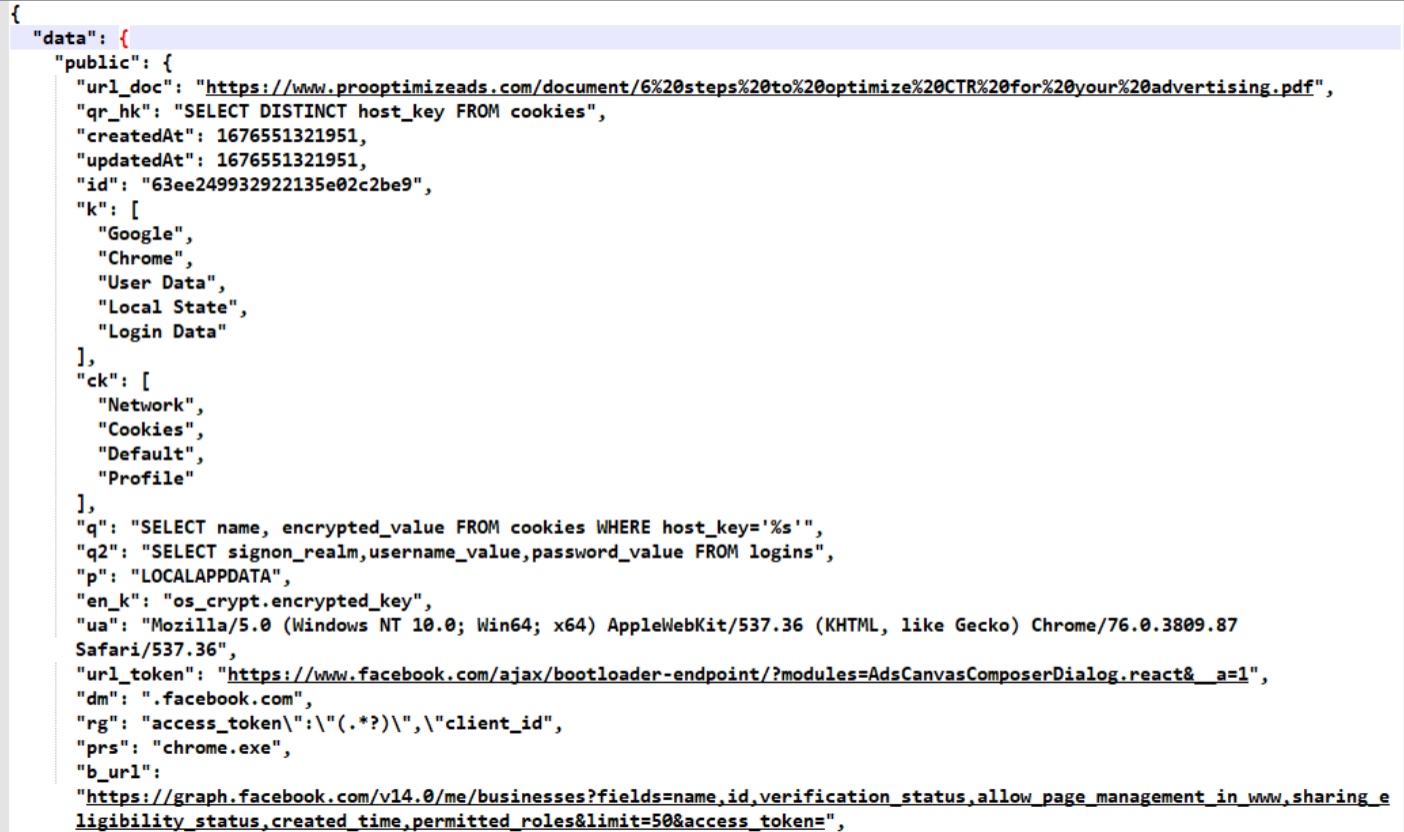
After obtaining configuration information, the Chrome.exe process will be shut down and relevant information will be stolen. The stolen information will be returned to the C2 address “http://167.179.66.121/api/version”. The specific return format is:

Association analysis
During the analysis of the samples, it was found that the attacker not only used OnlyFans as the topic to launch attacks but also used other topics such as “WhatsApp installation program” and “GPT installation program” to lure users to download and execute.
In addition, the differences in the delivered trojans are not significant. They all use Golang as the development language to steal Chrome browser information from infected hosts and send the stolen information back to the C2 address. The C2 address also uses “/api/setting” as the configuration distribution path, and “/api/version” as the reception and return path.
Appendix - IOC
C2
Hash
ae35a789f61e377dc715b0695b985d399dbcfe1650f0f10fe0ea40343fc4f0f8 22780384391c950e504c767926f341b563429dfb6ca1484efd2865265ced1580 671fdd73aac6e7cf5571bfe7930e438f3fab00867962a66a2ac34f1f96cb8140 118f0c8497bf72cc5d170434913f66669e64aa8881ed1211dafa4eb06eacb9cc 5da5e70853f2c2d6ccae7ad496e52d5935a96cfca4dc57465d1fa831d263f760 d3b7b3bce9f98beeb43e0c2adaec2fc37568551ce486805711223f6efc79194a 2e69c9cb41a285ef9625232fc8023f8c98d25a1e5f760ad6a83b80b2851dca72 ac54763c539c9f33f5b5305b477dbddc3e9cff34be5953a85c291c644c6d6e97 d3b7b3bce9f98beeb43e0c2adaec2fc37568551ce486805711223f6efc79194a 5a434625d97851d7fb6b3f411274ea0f0b87b62eb54522a3f16fe013cb1ec044 fca795be08af6a025fb1284e08995f288c43d85fe03cf544a70f4bbe75dc58fa

